9/11 related keywords hijacked to serve scareware
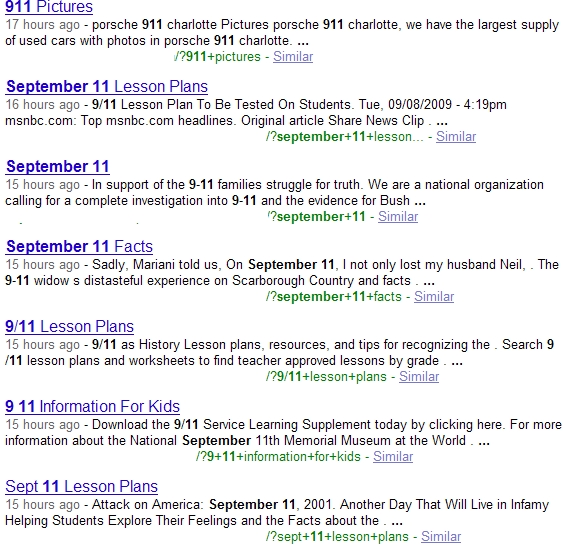
None of the sites are currently marked as harmful by the SafeBrowsing initiative, due to the evasive tactics applied in the campaign, with the majority of them already appearing within the first twenty results.
Is this a deliberate 9/11 themed blackhat SEO campaign, or is it "blackhat SEO for scareware serving purposes as usual" type of campaign?
The very same Ukrainian cybercrime group -- detailed assessments of their ongoing campaigns confirm their use of Google Trends -- that was recently hijacking Obama Speech related keywords next to U.S Federal Forms keywords, is also the same group behind the current 9/11 themed campaign.
Whereas it would first appear that they are very good at picking up trending, and very recent topics manually, the reality is that the process is completely automated, and has been for the past couple of years. This dynamic traffic hijacking in a near real-time Web is already undermining the usefulness of static lists of "dangerous keywords" or "dangerous celebrities" to search for.
- Go through related posts: Cybercriminals hijack Twitter trending topics to serve malware; Cybercriminals syndicating Google Trends keywords to serve malware; Google Video search results poisoned to serve malware; Massive comment spam attack on Digg.com leads to malware
The latest campaign is pushing Scanner-137082_2007.exe, and while its generic detection rate will inevitably improve, not falling victim to a scam that's selling non-existent security software, remains the best move.