Android users hit by scareware scam
Security researchers from Kaspersky Labs have intercepted a scareware variant targeting Android users, distributed as an Opera Virus Scanner.
According to Kaspersky:
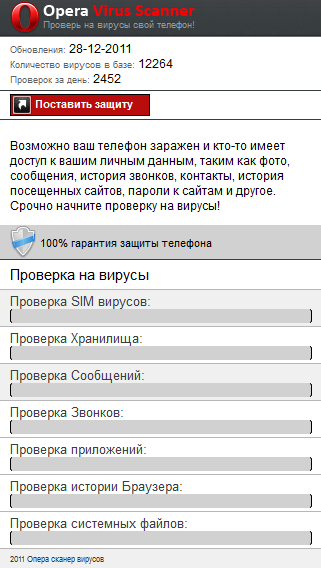
Both web pages claim that the user’s device might be infected and that somebody has access to personal data and then will ask the user to check his or her device for malware. If the user clicks on the button, the web page will emulate device scanning with the following ‘hard-coded’ results.
This web page never ‘finds’ malware on a SIM card but messages, calls, apps, browser history, storage and system files have threats, malware and are remotely accessible.
If the user clicks on the link, they'll be asked to download VirusScanner.apk, which is currently detected as Trojan-SMS.AndroidOS.Scavir. If the user is using a non-Android device, they'll be asked to download VirusScanner.jar currently detected as Trojan-SMS.J2ME.Agent.ij.
Malicious attackers are no strangers to the basics of localization and OS-porting. For instance, in the past we have seen scareware templates localized to Arabic, and DDoS bots ported across multiple operating systems.
The migration of scareware also known as fake antivirus software to mobile platforms, was a logical development largely anticipated by industry watchers.