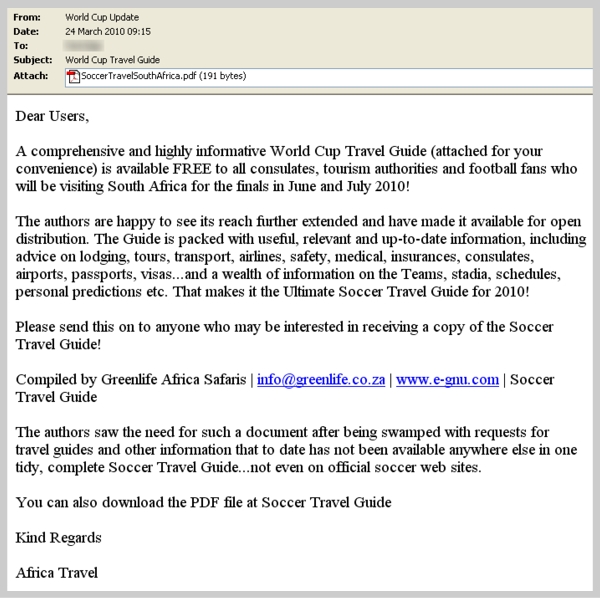
FIFA World Cup themed malware campaign spreads malicious PDF files
Researchers from Symantec are reporting on an ongoing targeted malware campaign using a FIFA World Cup 2010 theme, in an attempt to trick end users into executing a malicious PDF file, exploiting a recently patched flaw in Adobe Reader.
More details on the campaign:
- The attacker(s) have downloaded Greenlife’s PDF document, and changed it to include malicious code. They then attempted to email the malicious PDF to a user in a major international organisation that brings together governments from all over the world. We should emphasise that downloading the PDF from the Greenlife website is perfectly safe at the time of writing this blog.
- The attack makes use of a recently patched vulnerability in Adobe Reader – CVE-2010-0188. The patch for this critical rated vulnerability was released by Adobe on February 16, 2010. Since then we have observed a large number of targeted attacks attempting to exploit this vulnerability. Proof-of-Concept exploit code is available in the Internet which is contributing to the large number of observed attacks. The exploit makes use of a flaw in the TIFF file parsing in Adobe Reader. In particular, a stack overflow is caused by inserting a TIFF image into the PDF with a specially crafted “DotRange” tag.
With the event scheduled to take place in June, 2010, cybercriminals will be the first to take advantage of the anticipated traffic flow, coming from gullible bargain seekers (Survey: Millions of users open spam emails, click on links).
According to recent reports, malicious PDF files not only comprised 80 percent of all exploits for 2009, but also, represent the preferred infection vector for targeted attacks in general, for the first time ever surpassing the use of malicious Microsoft Office files.
Users should not just update their Adobe products, or perhaps even consider an alternative PDF reader, if truly paranoid. They should take a comprehensive approach when dealing with all the 3rd party applications and browser plugins, currently installed.