Localized ransomware variants circulating in the wild
Security researchers from Abuse.ch have intercepted multiple localized ransomware variants currently circulating in the wild.
The ransomware is dropped on the infected host using the Black Hole web malware exploitation kits, which exploits outdated and already patched client-side vulnerabilities.
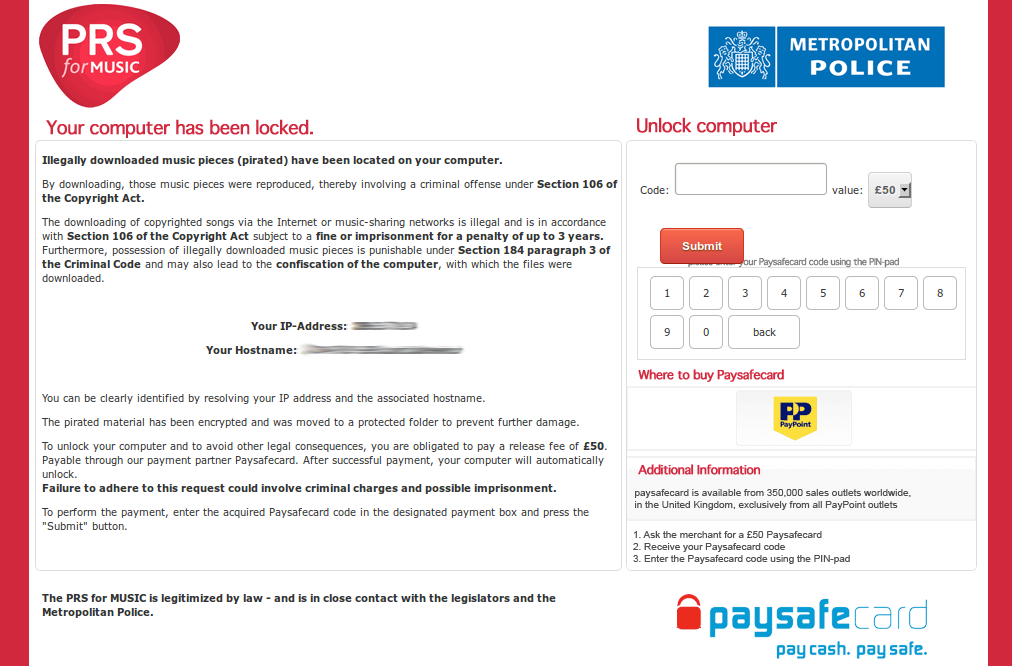
Once infected, end users are exposed to a professionally looking template impersonating a well known law enforcement agency in the targeted country, alerting they that their computer is locked due to the fact that "Illegally downloaded music pieces (pirated) have been found on their PC".
In their analysis, the researchers came across to templates localized to the native languages of the following countries:
- Switzerland; Germany; Austria; United Kingdom; France and the Netherlands
Cybercriminals are no strangers to the concept of localization. Thanks for managed localization and proofreading services targeted exclusively to cybercriminals, the value-added practice from a QA (quality assurance) perspective is becoming increasingly popular among malware authors, spammers and phishers.
End and corporate users are advised to ensure that they're running the latest versions of their third-party software, and browser plugins in an attempt to avoid getting exploited by the most popular exploit kit, the Black Hole web malware exploitation kit.
Related posts:
- New ransomware impersonates the U.S Department of Justice
- New ransomware variants spotted in the wild
- Localized ransomware variants impersonate law enforcement agencies
- Microsoft themed ransomware variant spotted in the wild
- Copyright violation alert ransomware in the wild
- New ransomware variant uses false child porn accusations
- Mac OS X SMS ransomware - hype or real threat?
- Who’s behind the GPcode ransomware?
Find out more about Dancho Danchev at his LinkedIn profile, or follow him on Twitter.