Cisco uncovers targeted spearphishing threat

If you thought spearphishing malware was passé, think again. Cisco recently discovered a spearphishing and exploit attempt that targeted the Visual Basic Scripting for Applications feature in Microsoft Word.
Investigation into the malware allowed Cisco to identify a group of attacks by the same threat actor, with Cisco ultimately exposing the threat actor's network.
According to the Cisco Threat Spotlight blog, the attacks were aimed specifically toward high profile, money-rich industries such as banking, oil, television, and jewelry. Victims were duped into opening an email attachment in the form of an invoice, written specifically for the recipient.
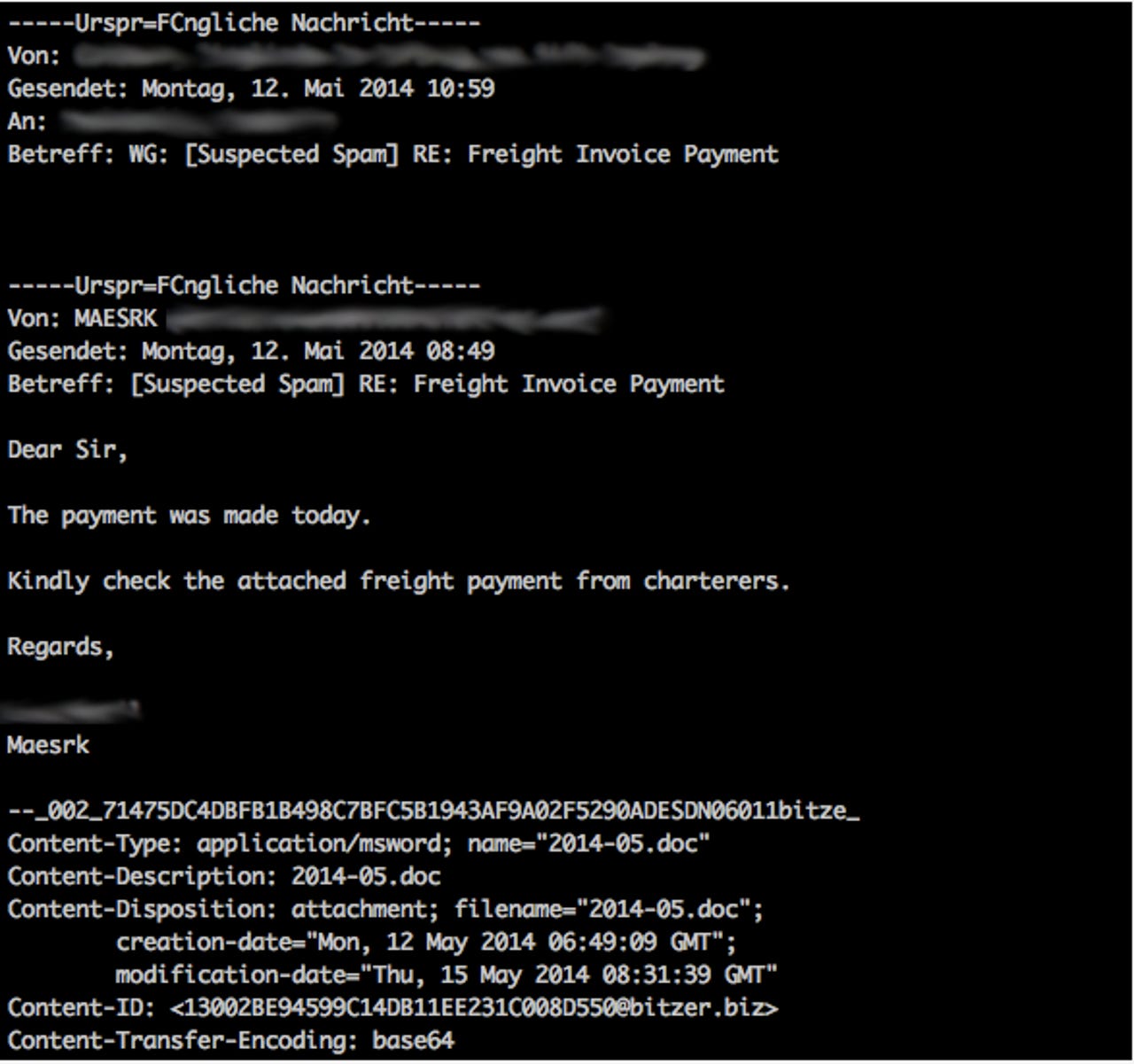
Once opened, the malicious Word attachment fired an On-Open macro, which then downloaded an executable and launched it on the victim's machine.
The threat actor used Dropbox to host four separate pieces of the payload for the exploit, with the domains londonpaerl.co.uk and selombiznet.in acting as command and control servers.
Peeling away more layers of the threat, Cisco discovered the londonpaerl.co.uk domain was a typo-squat of the domain londonpearl.co.uk, an international supplier of cultured pearls and cultured pearl jewelry. The bogus domain claimed to be an employment agency, but hidden content written into the browser revealed the threat actor had been in operation since at least 2007.
The Cisco blog explained:
It is interesting to note that previously we have blocked five backdoor components coming from londonpearl-uk.co on 5/26. All of these attacks were directed at a single customer, on the same day, within a 90-minute time frame. The customer targeted was involved in the industrial manufacturing vertical.
During the investigation we identified several different campaigns believed to be associated with this threat actor involving many other pieces of malware. Many of the domains appear to be suspended presumably due to past malicious activity. In fact, during the investigation the threat actor changed the information on some of the domains changed several times. Luckily if you monitor whois history you can still view all of this information, including the evasion attempt. While we were performing the investigation, items like addresses, email addresses and such were changed, literally, in between browser refreshes. All of the domains we've associated with this threat have been blocked for web security customers since their discovery. We will continue to monitor the situation.