Talos finds new VPNFilter malware hitting 500K IoT devices, mostly in Ukraine

VPNFilter malware
A new strain of malware known as VPNFilter has been found infecting at least 500,000 networking devices, mainly consumer-grade internet routers, across 54 countries.
According to a blog from Cisco's Talos, the known devices affected by VPNFilter are Linksys, MikroTik, Netgear, and TP-Link networking equipment in the small and home office space, as well at QNAP network-attached storage (NAS) devices.
"The behaviour of this malware on networking equipment is particularly concerning, as components of the VPNFilter malware allows for theft of website credentials and monitoring of Modbus SCADA protocols," the researchers wrote.
"The malware has a destructive capability that can render an infected device unusable, which can be triggered on individual victim machines or en masse, and has the potential of cutting off internet access for hundreds of thousands of victims worldwide."
Preliminary findings of the researchers indicate the VPNFilter malware overlaps with versions of the BlackEnergy malware, which was responsible for attacks that targeted devices in Ukraine.
While the researchers have said that such a claim isn't definitive, they have observed VPNFilter "actively infecting" Ukrainian hosts, utilising a command and control infrastructure dedicated to that country. The researchers also state VPNFilter is likely state sponsored or state affiliated.
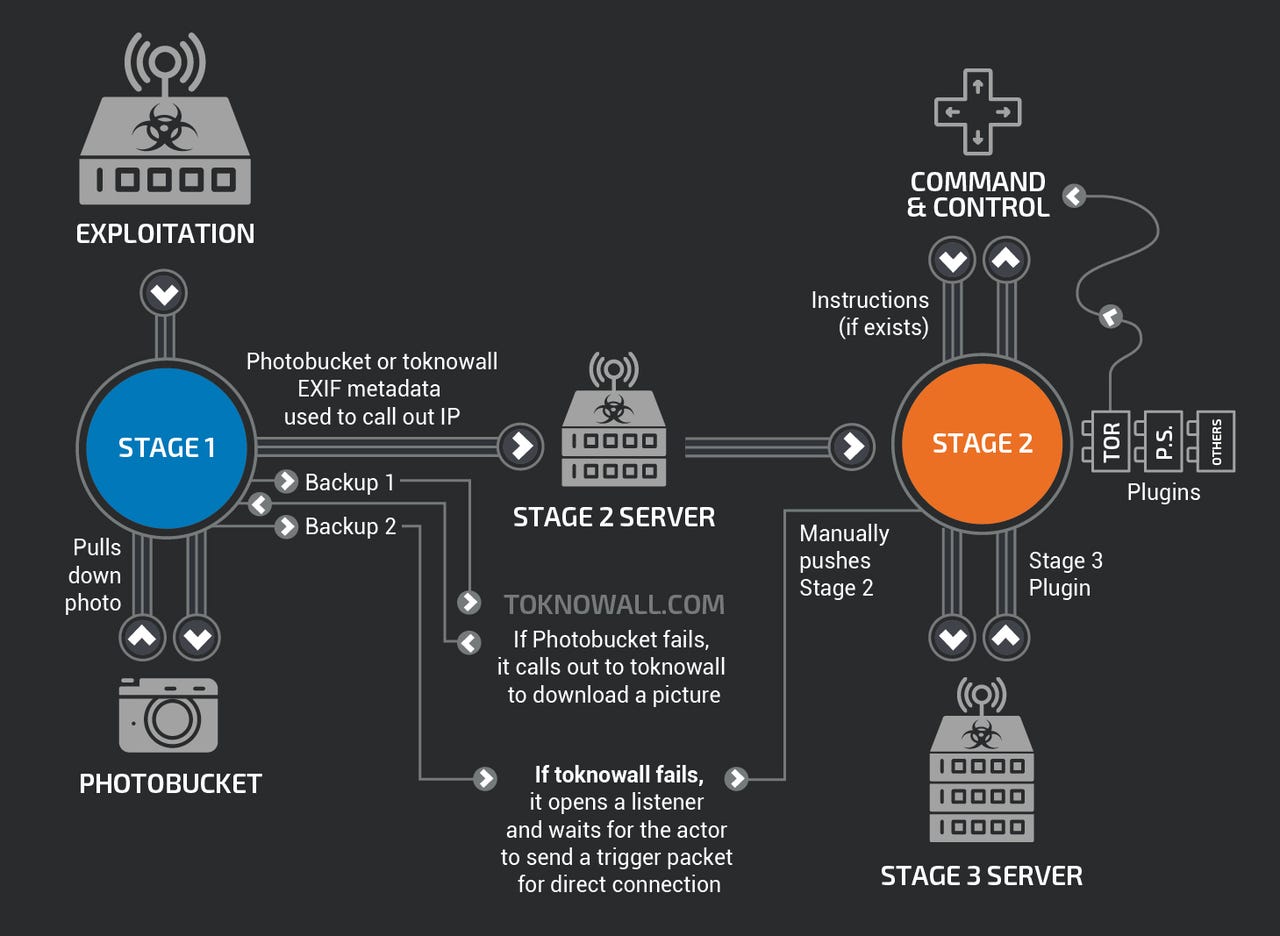
As detailed by the researchers, the stage 1 malware persists through a reboot, which normal malware usually does not, with the main purpose of the first stage to gain a persistent foothold and enable the deployment of the stage 2 malware.
"Stage 1 utilises multiple redundant command and control (C2) mechanisms to discover the IP address of the current stage 2 deployment server, making this malware extremely robust and capable of dealing with unpredictable C2 infrastructure changes," the researchers wrote.
The stage 2 malware possesses capabilities such as file collection, command execution, data exfiltration, and device management; however, the researchers said some versions of stage 2 also possess a self-destruct capability that overwrites a critical portion of the device's firmware and reboots the device, rendering it unusable.
"Based on the actor's demonstrated knowledge of these devices, and the existing capability in some stage 2 versions, we assess with high confidence that the actor could deploy this self-destruct command to most devices that it controls, regardless of whether the command is built into the stage 2 malware," the report continues.
It has also been reported that there are multiple stage 3 modules that serve as plugins for the stage 2 malware, providing additional functionality.
At the time of publication, Talos said it was aware of two plugin modules: A packet sniffer for collecting traffic that passes through the device, including theft of website credentials and monitoring of Modbus SCADA protocols; and a communications module that allows stage 2 to communicate over Tor.
"We assess with high confidence that several other plugin modules exist, but we have yet to discover them," the researchers said.
"We assess with high confidence that this malware is used to create an expansive, hard-to-attribute infrastructure that can be used to serve multiple operational needs of the threat actor.
"Since the affected devices are legitimately owned by businesses or individuals, malicious activity conducted from infected devices could be mistakenly attributed to those who were actually victims of the actor."
Additionally, the malware can also be used to collect data that flows through the affected device.
The researchers have said VPNFilter could be used to conduct a large-scale destructive attack by using the "kill" command, which would render some or all of the physical devices unusable.
US Justice Department announces action
The United States Justice Department shortly after announced seizing a domain used in the botnet campaign.
Attributing VPNFilter to Sofacy Group, also known as apt28, sandworm, x-agent, pawn storm, fancy bear, and sednit, DoJ said the group has been operating since at least 2007, targeting government, military, security organisations, and other targets of perceived intelligence value.
"The Department of Justice is committed to disrupting, not just watching, national security cyber threats using every tool at our disposal, and today's effort is another example of our commitment to do that," said Assistant Attorney General Demers.
"This operation is the first step in the disruption of a botnet that provides the Sofacy actors with an array of capabilities that could be used for a variety of malicious purposes, including intelligence gathering, theft of valuable information, destructive or disruptive attacks, and the misattribution of such activities."
Defending against VPNFilter
Due to the nature of the affected devices, with the majority connected directly to the internet with no security devices or services in place, compounded by the fact that most of the affected devices already have publicly known vulnerabilities not patched by the average user with no built-in anti-malware capabilities, Talos said defending against VPNFilter is extremely difficult.
"The destructive capability particularly concerns us. This shows that the actor is willing to burn users' devices to cover up their tracks, going much further than simply removing traces of the malware," the researchers wrote.
"If it suited their goals, this command could be executed on a broad scale, potentially rendering hundreds of thousands of devices unusable, disabling internet access for hundreds of thousands of victims worldwide or in a focused region where it suited the actor's purposes."
Talos has also developed and deployed more than 100 Snort signatures for the publicly known vulnerabilities for the potentially affected devices.
The researchers recommend users of small and home office-grade routers and NAS devices reset them to factory defaults and reboot them in order to remove the stage 2 and stage 3 malware, and reach out to device manufacturers to ensure up-to-date patching.
Updated at 4.08pm AEST, May 24, 2018
RELATED COVERAGE
- Malware campaign expands to add cryptocurrency mining and iOS phishing attacks
- Telegrab malware hijacks Telegram desktop sessions
- This malware is harvesting saved credentials in Chrome, Firefox browsers
- IoT security: Is cryptocurrency-mining malware your next big headache?
- History repeating: How the IoT is failing to learn the security lessons of the past
- What is malware? Everything you need to know about viruses, trojans and malicious software
- Ransomware attacks are on the rise. Should businesses pay up or focus on tightening security? (TechRepublic)