Worries arise about security of new WebAuthn protocol

A team of security researchers has raised the alarm about some cryptography-related issues with the newly released WebAuthn passwordless authentication protocol.
WebAuthn was officially launched earlier this year, in April. It's a standard developed under the patronage of the World Wide Web Consortium (W3C), the official body for all web standards.
The protocol was based on the FIDO 2.0 Web API, donated to the W3C by the FIDO Alliance, an industry consortium that includes some of the tech world's largest companies, whose role was to create interoperable authentication methods and standards.
Also: Tesla modifies product policy to accommodate "good-faith" security research
The new WebAuthn protocol will allow users of a device --such as a computer or a smartphone-- to authenticate on a website using a USB security key, a biometric solution, or his computer or smartphone's password. The ideal scenario is that WebAuthn would replace the need to create password-protected accounts on online websites, hence avoid situations where hackers pilfer this data during security breaches.
Instead, the user would register on the site using a device (via an attestation key) and later authenticate via the same device or others using authentication keys generated by that device during login procedures.
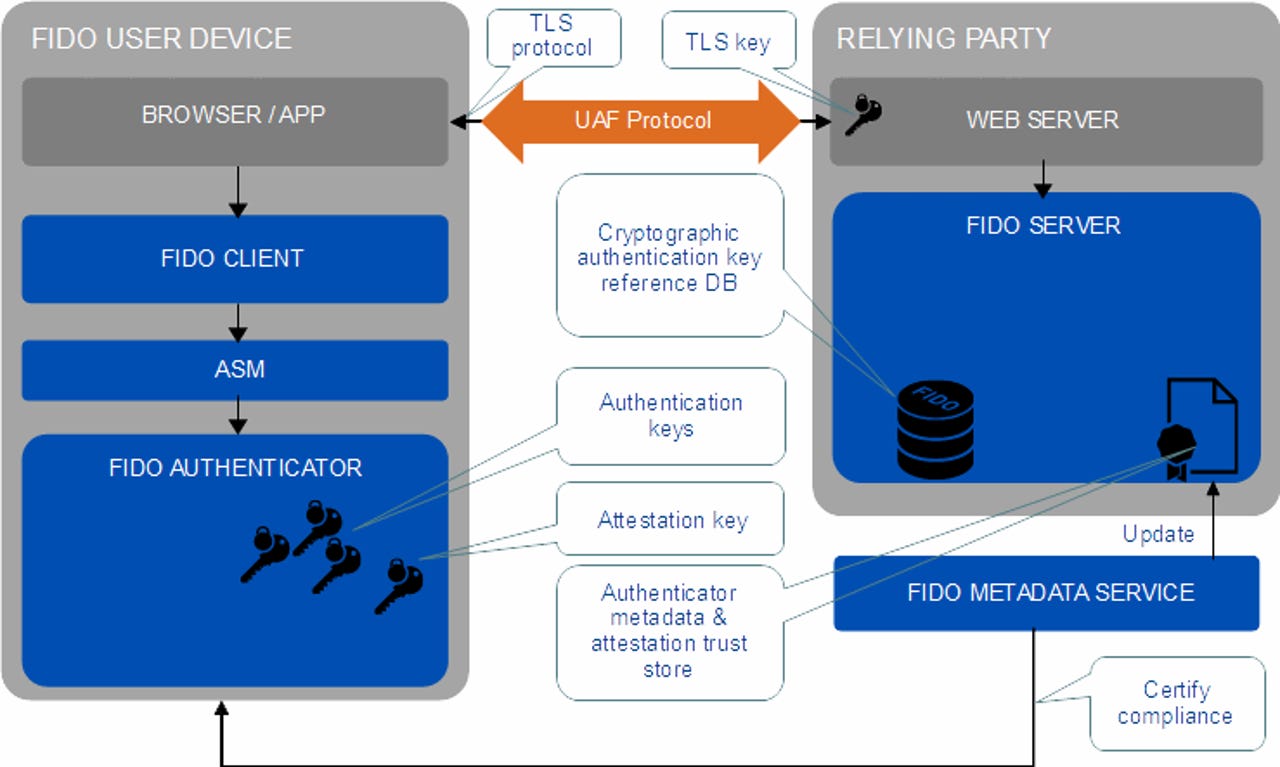
Browser makers have agreed to support WebAuthn, mostly because some of them were already members of the FIDO Alliance, but also because of the protocol's very tangible security benefits.
But at the end of last month, the team of security researchers at Paragon Initiative, known for their strong background in cryptography, have taken a close look at this new protocol making its way into browsers like Chrome, Edge, and Firefox.
In a security audit, researchers say they identified various issues with the algorithms used to generate the attestation keys (signatures).
They point out that the W3C WebAuthn specification recommends the use of outdated algorithms such as the FIDO Alliance's Elliptic Curve (EC) Direct Anonymous Attestation (DAA), or RSASSA-PKCS1-v1_5.
Also: Vulnerabilities found in the remote management interface of Supermicro servers
The Paragon team detailed a long list of issues with both algorithms in a technical report, here, but in short, they are vulnerable to quite a few known cryptographic attacks. In particular, they took an issue with the use of RSASSA-PKCS1-v1_5.
"PKCS1v1.5 is bad. The exploits are almost old enough to legally drink alcohol in the United States," they said.
But the FIDO Alliance's custom ECDAA crypto algorithm is not that safe either.
"If converted into a practical exploit, the ECDAA attacks discussed in the article would allow attackers to steal the key from a [server's] TPM, which would allow attackers to effectively clone the user's hardware security token remotely," Arciszewski said.
"The scenarios that follow depend on how much trust was placed into the hardware security token," he added. "At minimum, I imagine it would enable 2FA bypasses and re-enable phishing attacks. However, if companies elected to use hardware security tokens to obviate passwords, it would allow direct user impersonation by attackers."
But the attacks aren't your run-of-the-mill attacks. "Silver lining. Active exploits would be nontrivial in practice," Arciszewski told us.
"I don't believe that ECDAA's design is ready to shoulder this much responsibility," the Paragon expert concluded.
In subsequent email exchanges with the Paragon team, ZDNet understands that at the heart of the issue may be the confusing WebAuthn documentation released by the FIDO Alliance team, which, for legacy purposes, categorizes both algorithms as "required" (for RSASSA-PKCS1-v1_5) and "recommended" (two ECDAA-based algorithms).
This may lead to situations where implementers may believe the two algorithms may be minimal thresholds for implementation and support only these.
"There are plenty of COSE algorithms to choose from," Arciszewski said.
Also: Google open-sources internal tool for finding font-related security bugs
ZDNet contacted the FIDO Alliance team earlier this week, which, in return, got in touch with Arciszewski and his team.
"The FIDO Alliance values engagement with the security research community and responsible disclosure of potential vulnerabilities in the implementation of our specifications. Which is why, of course, this is not the first time an external cryptographer has reviewed the specifications," Brett McDowell, executive director of the FIDO Alliance, told ZDNet in a statement.
"After a close read of the blog post, we think it is positive that no fundamental flaws in the algorithm were discovered," McDowell added.
"We recognize the valid points raised about potential vulnerabilities that could be introduced by implementers if best practices are not followed," the FIDO Alliance exec added. "We have started considering what guidance we want to document for implementers and our security secretariat lead is reaching out to Scott to collaborate on this."
ZDNet understands that conversations between the two parties are going on to improve the WebAuthn protocol and its documentation.