Photos: Sniffing out fraud with digital forensics

Evidence uncovered in everything from PCs to PDAs
The digital forensics unit (DFU) of the Serious Fraud Office sniffs out incriminating evidence from crime scenes.
Armed with laptops and suitcases containing specialist forensic tools the 21-strong team can swiftly capture information from nearly any device, from laptops to mobile phones and PCs to games consoles.
This Logicube CellDEK forensic tool can pull data from more than 1,100 of the most popular mobile phones and PDAs, capturing information using a plug-in connector, infrared or Bluetooth.
The team aims to capture nearly all the data it needs on scene during a police search, storing a complete image of each device on its 300TB of dedicated storage - where it will help solve anything from multibillion pound corporate price fixing investigations to murders.
Picking apart the information is a painstaking process as the team first strips out the hundreds of thousands of duplicate, system or application files; most photos; attachments; and malware, to produce a clean set of data.
Cracking encryption is the second major hurdle, with the team employing the brute force of its 100 quad-core PCs to break low-grade encryption, such as password protected files.
The team does not attempt to crack high-grade encryption, relying instead on the threat of a prison sentence for individuals refusing to hand over passwords or decrypted files.
Photo credit: Nick Heath
One of the biggest challenges faced by the unit is the sheer size and scale of the fast evolving mobile phone market.
New forensic tools are constantly being devised to detect emerging devices and the team must carry around scores of connectors for nearly every mobile phone produced, a small selection of which are seen here.
Keith Foggon, head of the DFU has overseen a revamp of the unit earlier in the summer.
He said: "The PC architecture it is usually stable. But with mobile devices they change daily and consumers buy, throw away and upgrade their mobile phones, with new models coming out very, very regularly.
"That is an area where we are almost playing catch-up, we are never ahead of the mobile device forensic market."
Photo credit: Nick Heath
When forensic tools are unable to capture data from an obscure or new mobile phone it can mean reverting to a painstaking manual process of photographing each screen.
This fixed digital camera is used to capture screens from phones, a time-consuming process that can run to hundreds of images but is necessary to produce screenshots to show in court, in the event of a dispute over an issue such as SIM card references.
Photo credit: Nick Heath
A small selection of the hundreds of mobile phones that are analysed by the DFU on a regular basis.
The unit also probes phones for the City of London Police to allow it to develop tools and resources to tackle the variety of phones on the market.
Foggon says the DFU can cope with all of the major brands but still comes across handsets that leave it stumped, such as an Amoi phone that initially had it baffled.
The DFU has two attached officers from the City of London Police, soon to be increased to four, and provides evidence for a wide range of cases such as people trafficking.
Photo credit: Nick Heath
These servers are devoted solely to the 130TB of information, including half-a-billion emails, amassed during the seven-year Operation Holbein investigation into pharmaceutical price fixing.
The DFU uses about 60 per cent of its 300TB storage, which is spread over two floors of the Serious Fraud Office (SFO) headquarters.
The alleged price-rigging of generic drugs such as penicillin is estimated to have cost the National Health Service as much as £2bn.
Photo credit: Nick Heath
This degausser generates a magnetic field to wipe clean any hard discs and other storage devices.
If a drive or memory stick holds government protected data the unit will first degauss it several times using several different polarities of magnetism and then pulverise them.
The degausser comes with a remote control that looks like a car central locking keyring to allow it to be used from a safe distance.
Foggon warns: "You need to stand back two metres otherwise it degausses you as well. It can be dangerous if you have a pace maker and it can't be used too close to other equipment because it resets a lot of the machines, it killed our microwave."
Photo credit: Nick Heath
This is the workspace in which the SFO tests out new tools for forensic analysis on emerging hardware, such as solid state hard drives.
Photo credit: Nick Heath
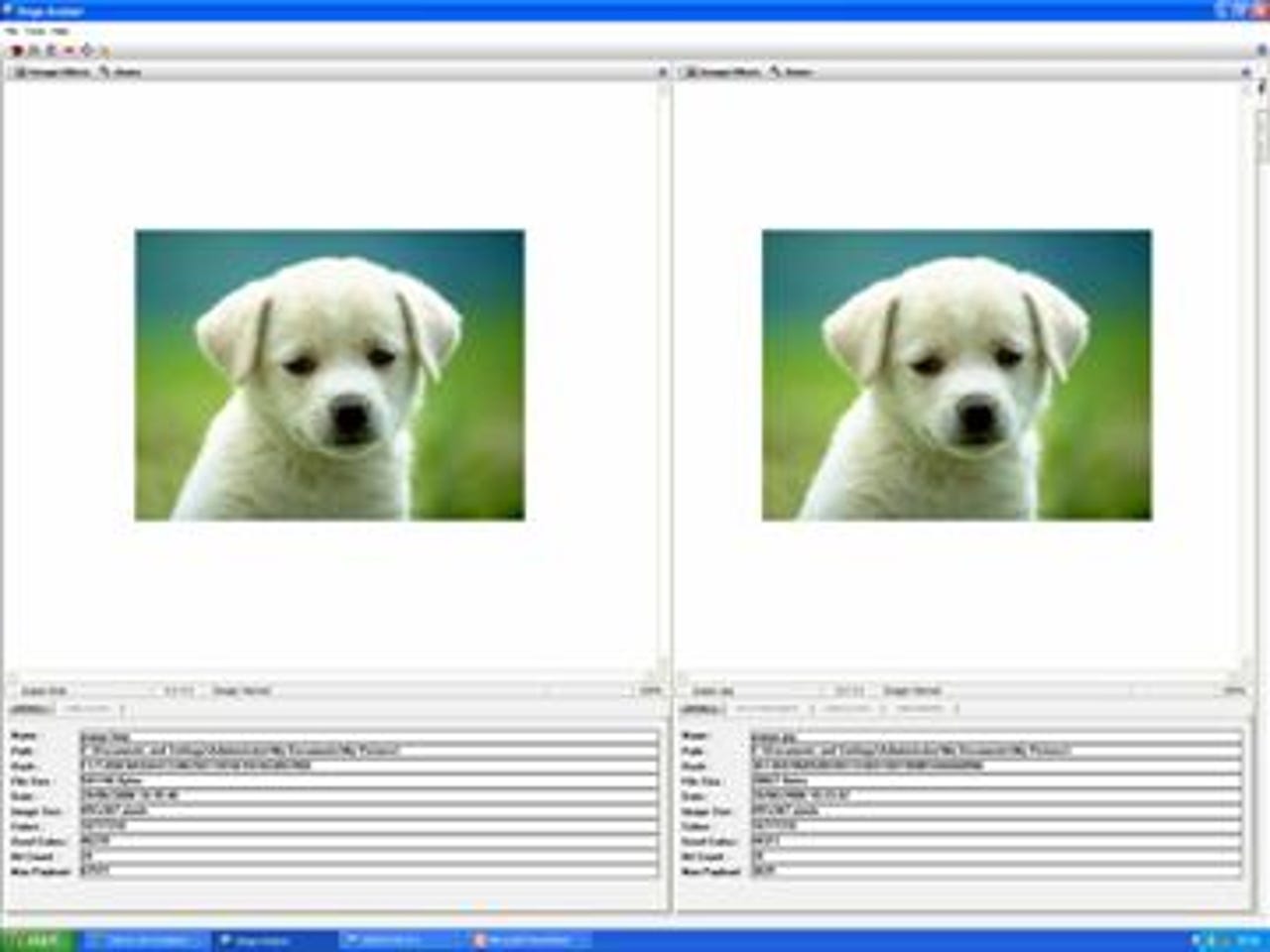
These innocuous looking pictures may look identical to the naked eye but the one on the right contains data hidden within almost imperceptible colour differences.
Foggon is concerned that the unit's job could start becoming far more difficult as criminals embrace steganography as a way of hiding information.
The subterfuge only becomes apparent when comparing the number of colours in both pictures, with 46,270 colours in the one of the left and 44,311 on the right.
Photo credit: Serious Fraud Office
Here the pictures are filtered through a specialised viewer and magnified to reveal the tiny differences in their make-up. The area of the picture that has been altered to hide the data has been circled.
Foggon says it would make uncovering evidence far more difficult if its use starts to become more widespread.
He said: "We have tools to help us analyse it but it's a long process to help us do that, it's not an easy job at all."
Photo credit: Serious Fraud Office
Here are some of the variety of tape drives that the DFU uses to process the back-up tapes seized on searches.
Photo credit: Nick Heath
These are the Rainbow Tables that contain lists of password hashes for common applications, such as those made by Microsoft and Adobe, to allow the DFU to quickly crack password protected files relating to this software.
Photo credit: Nick Heath