Pro-Assad malware targets Syria activists

A report released by the Electronic Freedom Foundation (EFF) and University of Toronto's Citizen Lab details malware attacks used by pro-Syrian government forces against the opposition.
The paper (embedded below), is co-authored by Citizen Lab security researchers Morgan Marquis-Boire and John Scott-Railton and EFF Global Policy Analyst Eva Galperin.
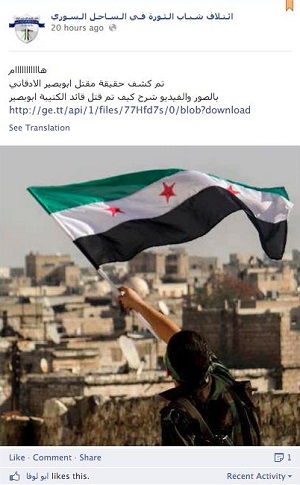
The image nearby is taken from a post to the Facebook page of the pro-opposition Revolution Youth Coalition on the Syrian Coast. [WARNING: As we report here, there have been malicious links on this page in the past. Proceed with caution.] The post, which tells the story of the killing of an opposition commander, includes a link to what it claims is a video related to the conflict. In fact, the link downloads malware, a remote access tool known as Bladakindi or njRAT. "RAT" in the context of malware is a Remote Access Tool, used for logging keystrokes and taking screenshots on the victim's system. The attackers seem to have taken over the Facebook page, because comments to the post which warned of malware in it were subsequently removed. For more details read the report.
Another example cited by the report describes an email sent to an administrator of an NGO. It includes a link to a video showing the brutal murder of a civilian. The video is actually an executable program which also drops a RAT on the system. Other related email campaigns are described in the report.
Hat tip to Bruce Schneier.
https://www.eff.org/files/2013/12/23/quantum_of_surveillance-effcl_0.pdf