Warning: GTA, Super Mario on Google Play are Android malware

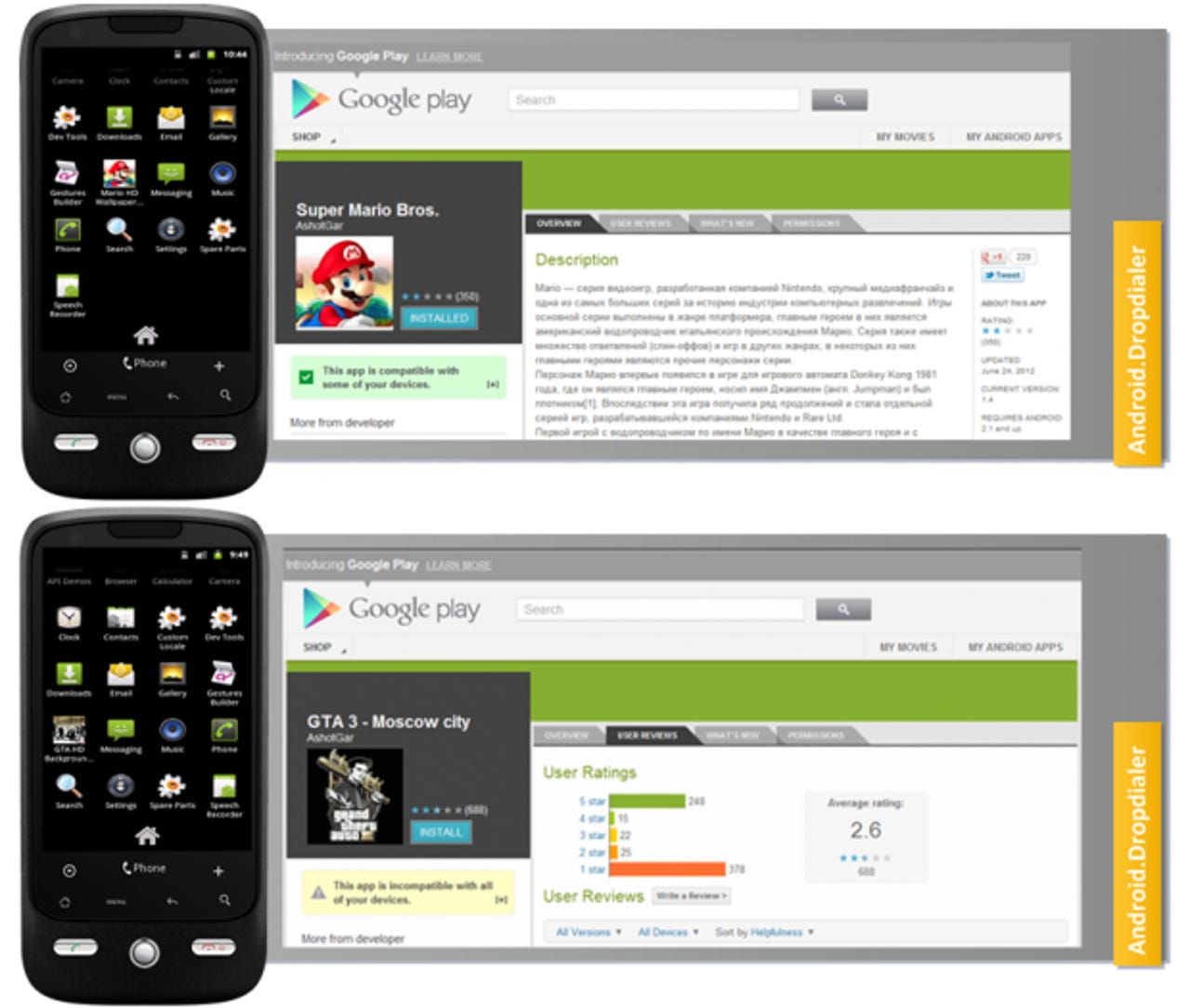
Symantec, which first discovered the malware, detects it as Android.Dropdialer and describes it as "a Trojan horse for Android devices that sends SMS messages to a premium-rate phone number." The Trojan poses as a wallpaper app, but it also installs an additional app which sends expensive international text messages to generate revenue for its creators. The security firm saw it posted as two popular titles: "Super Mario Bros." and "GTA 3 Moscow City."
The duo showed up on the official Google Play store on June 24 and managed to generate between 50,000 and 100,000 downloads. Both are disturbing statistics. Google didn't find the malware until Symantec pointed it out to the search giant, but not before tens of thousands of users downloaded it first.
What is even more worrying, however, is that F-Secure has found evidence Google did not clean its market very thoroughly. In less than 10 seconds, the security firm found more samples of the same malware, masquerading as: GTA 3: Las Vegas, Instagram After Effects, FIFA 11 Russian Edition, and Odnoklassniki Life. It would not surprise me in the slightest if more such apps were lurking in the store.
There are two things that make this malware variant particularly interesting. The two twists work in concert to trick the Android Security team and make it more difficult for security researchers to collect samples.
Symantec notes the Trojan in question uses a remote payload to avoid detection of anomalies during the automated QA screening process. The first stage is to post on Google Play, and once the app is installed on a victim's phone, it downloads an additional package, hosted on Dropbox, called "Activator.apk."
F-Secure notes that premium rate SMS numbers only work within a particular country. As such, whoever uploaded this malware made a point to make it "incompatible" outside of profitable telecom networks. This cleverly limits the malware to its target group.
It's one thing to see Android malware on third-party app stores but it's a completely different matter to see them sneak onto the official Google Play store. While users still need to be careful about what they download, I would say Google is more at fault here than anyone else.
See also:
- Warning: Fake Skype app on Android is malware
- Malware charges users for free Android apps on Google Play
- Android malware families nearly quadruple from 2011 to 2012
- A first: Hacked sites with Android drive-by download malware
- Warning: Fake Biophilla app on Android is malware
- Warning: Fake Instagram app on Android is malware