10 tech things we didn't know a week ago

1. Publishing counterfeit apps is a criminal offense
This week, the U.S. Justice Dept. said the leader and co-conspirator of Android device app piracy ring pleaded guilty to charges of distributing apps with a total retail value of $700,000. The claims boiled down to copyright infringement, a crime punishable by hefty fines and time behind bars.
2. Aereo has no "plan B" if it loses Supreme Court battle
As internet streaming giant Aereo heads to the U.S. Supreme Court in the coming weeks to defend itself against a number of broadcasters (including CBS, which owns ZDNet), the company admits that it doesn't have anything up its sleeve should it lose the case. According to Bloomberg, the company has no "plan B," which may force it to eventually shutter.
3. About 95 percent of all ATMs run Windows XP
As Windows XP has just over a week until its end-of-life, this week we learned more than 95 percent of ATMs run the aging operating system. Although cash machines won't suddenly stop working, it's enough to have banks concerned. Recent reports have shown that ATMs can be hacked using just a USB stick and malware, which can allow the attacker full access to the "holes in the wall."
4. ISPs can, in fact, be forced to block pirate sites, EU court says
Despite the U.S. government's bid to enforce site blocking through controversial legislation, EU governments might now have a cause for celebration, after the highest court in the 28 member state bloc confirmed ISPs can be required to block access to pirate sites. According to the verdict, blocking orders do not restrict an ISPs freedom to serve its customers or conduct its business. The EU decision bounces the decision-making process back to member state national courts.
5. After antitrust ruling, Amazon may have free money for you
Following the Apple "cartel" ruling that landed the iPhone and iPad maker in hot water with U.S. authorities over alleged antitrust behaviour against Amazon, the retail giant has passed the settlement back to its customers. That may mean depending on your past Kindle ebook library spending, you may have a spare few dollars of credit to spend.
6. Bitcoin is property, not currency, according to the U.S.
The U.S. government will not treat the Bitcoin cryptocurrency as currency — instead it shall be considered property, which makes it the first substantive ruling by the U.S. tax authority. According to experts speaking to Bloomberg, the ruling is not as good for consumers, and some are already asking the Internal Revenue Service to change its mind.
7. Early Microsoft code included f-bombs and bad jokes
Microsoft programmers developing the first versions of MS-DOS and Word were not afraid of throwing in the occasional joke line of code or "easter egg." In some lines of code, expletives and fart-jokes were included. Granted, the code was written more than 30 years ago and so a bunch of mostly in their early-20s can be mostly excused.
8. Government data requests to Google have more than doubled in 4 years
Google's latest transparency report shows that requests by governments have gone up by 120 percent since 2009. The search, cloud, and mobile giant has been pushing back against the U.S. Justice Dept. for months in efforts to try to release more information about the data requests made by the U.S. in the wake of the National Security Agency surveillance leaks.
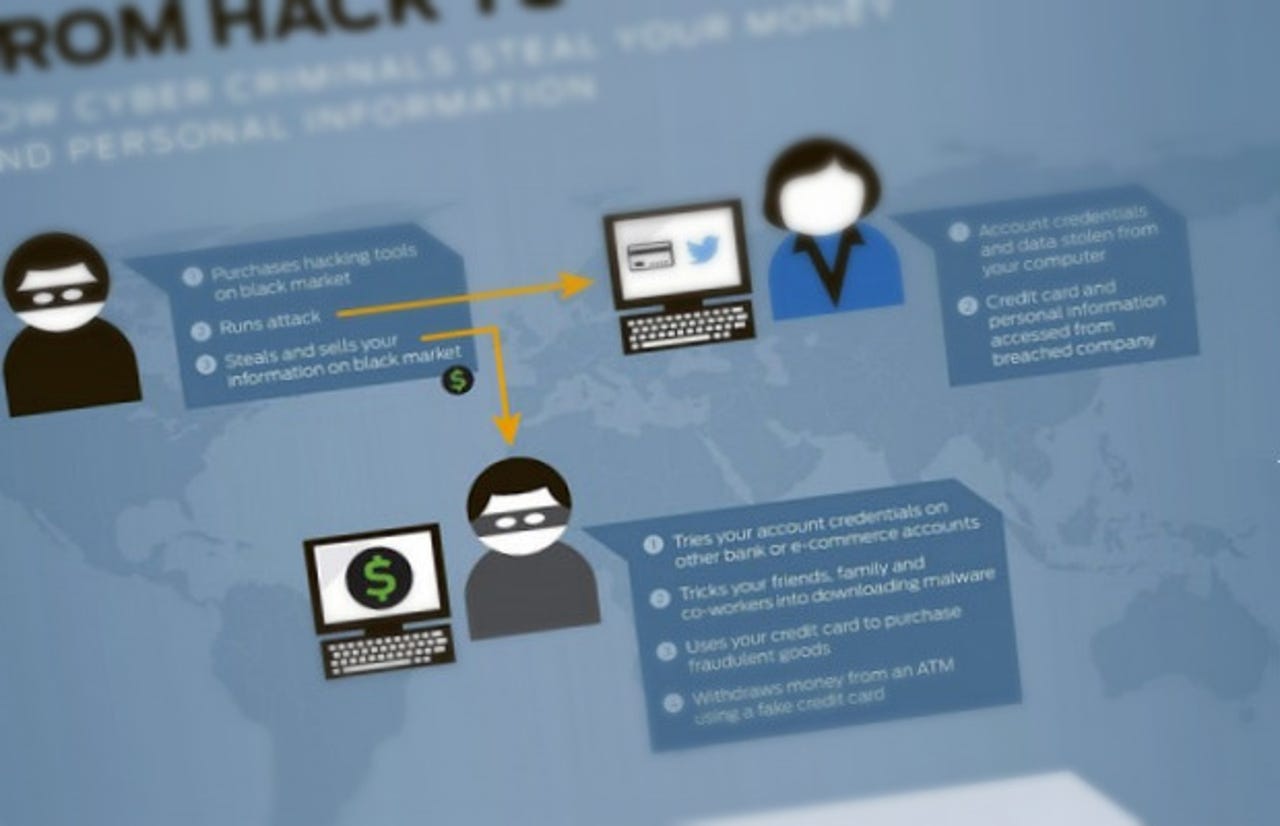
9. Stolen Twitter accounts can be 'more valuable' than credit cards
A Twitter account can be more valuable to a hacker than someone's credit card, latest research shows. Credit card data once stood at $20-$135 per account, but that dropped to about 75 cents per record. Nowadays, social media accounts can be more valuable, ranging in at as much as $325 per account, depending on the reach of the profile.
10. Tech companies can be sued for having 'illegible' privacy policies
And last but not least, soon may see the end of those lengthy, complicated, and "illegible" privacy policies, after a French consumer group filed a lawsuit against Google, Facebook, and Twitter, arguing these texts are too complex for most to understand. The group wants a French judge to remove or modify "the vast number of contentious clauses these companies impose."