Android botnet poses as Google app, pilfers email and SMS

Security researchers have fingered Chinese cybercriminals as the source of newly-discovered Android malware that poses as a Google app to steal messages from victims.
The malware, dubbed MisoSMS, is being distributed through SMS phishing, which sees users tempted to click on a link that takes them to the app in a non-Google store. The app is presented to victims as an Android settings app that upon installation appears as 'Google Vx' — an app clearly not from Google that will siphon off the victim's SMS and email to servers hosted in China.
Researchers at security firm FireEye who discovered the malware claim it's been used in at least 64 spy campaigns targeted mainly at users in South Korea.
Once Google Vx is installed, the app ask for administrative permissions on the device and uses that to conceal itself while it establishes a connection to the attacker's botnet infrastructure, which relies on hundreds of web-based email accounts to communicate with the app.
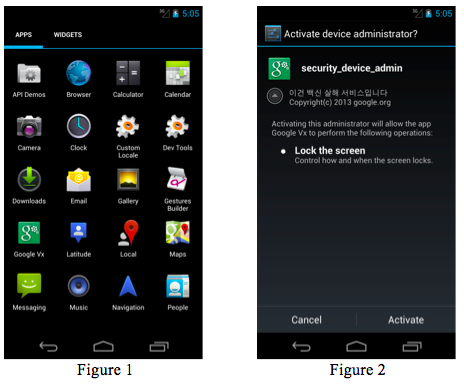
The setup allows the app to forward the content of SMS messages and the sender's number to the attacker's email accounts as soon as the text messages are received. As the app uses webmail rather than SMS to pass on the details, it will check when the device has an internet connection and will even backs up failed forwarded messages to be resent again later.
It's far from the first Android malware designed to steal SMS and not the first Android botnet to be seen. However, researchers note MisoSMS' use of webmail accounts is an interesting new element used in a number of recent attacks on Android users in South Korea.
"Some SMS-stealing malware sends the contents of users SMS messages by forwarding the messages over SMS to phone numbers under the attacker's control. Others send the stolen SMS messages to a (command and control) server over TCP connections. This malicious app, by contrast, sends the stolen SMS messages to the attacker’s email address over an SMTP connection," FireEye's researchers wrote, pointing to malware that used similar techniques discovered earlier this year by Korean security vendor INCA.
In all, the researchers have found 450 email accounts at an unnamed Chinese webmail provider that are being used in the attacks. The accounts have since been disabled.
Typically security experts advise users not to download apps from places other than Google Play, although in some markets, like China, third-party app stores are the norm, and MisoSMS is hosted in one such third-party store.
A FireEye spokesperson told ZDNet: "Miso follows a new emerging type of mobile threat that is distributed via SMS phishing, rather than traditional email. Why? It had a good chance of being delivered to the recipient unlike email where email hygiene filters gave a high chance of stopping it [...]
"Unlike most SMSishing attacks this one once installed sends intercepted SMS messages back to a number of hardcoded email addresses hosted by a provider in China. We are currently working with Korean law enforcement to ensure they have our research to help them protect consumers in South Korea."