Admin rights to blame for 97 percent of critical Microsoft flaws - Report

An analysis of Microsoft Patch Tuesday bulletins suggests that 97 percent of all reported critical security vulnerabilities could have been mitigated simply by removing administrator rights.
The figures are from the 2014 Microsoft Vulnerabilities Report by UK-based security firm Avecto, in which the company pulled data from every patch issued by Microsoft in 2014 -- 240 in total.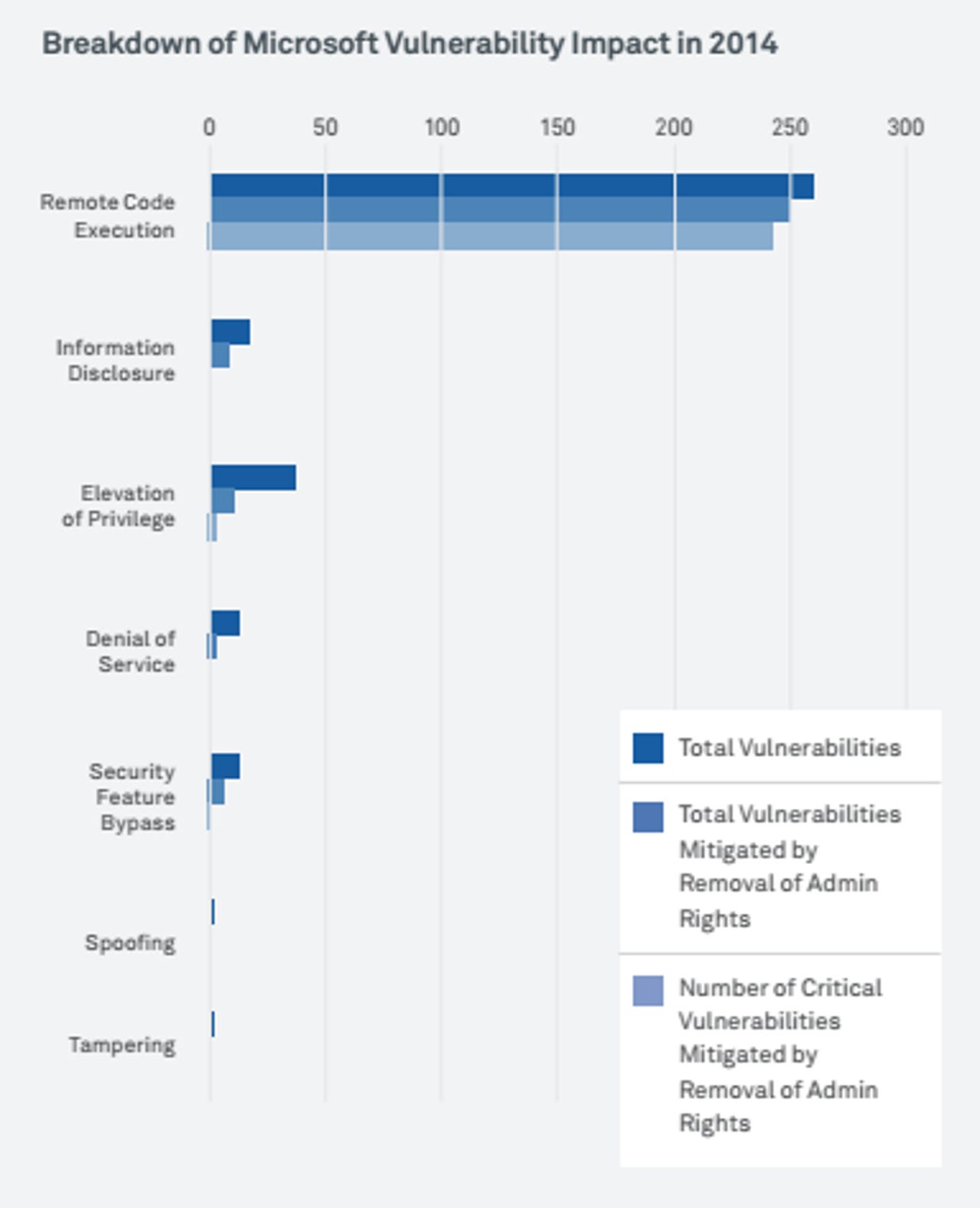
In 2013, the same report found that 92 percent of 147 total vulnerabilities with a critical rating could have been prevented via the same admin rights removal -- indicating a 63 percent year-over-year increase in the total number of critical vulnerabilities.
Breaking the numbers down further, admin rights were used to exploit 97 percent of Windows OS flaws, 99.5 percent of those in Internet Explorer, and 95 percent in Office.
Featured
So what privileges are lost when a user is stripped of their administrator rights? Avecto explains that admin rights typically include the ability to install, modify and delete software and files, in addition to adjusting system settings. Normally, admin rights should not be granted on a majority of employee machines.
The reason, the report pointed out, is because user accounts with those types of admin privileges are the primary targets for exploitation by malware, as they provide unrestricted access to an endpoint.
"Our 2014 analysis highlights the continued benefits of stripping away admin rights," said Paul Kenyon, EVP of Avecto. "Time and time again, the removal of admin rights proves to be a simple and effective threat mitigation strategy -- and yet many businesses are still overlooking this fundamental practice."
Kenyon also lamented how there is a misconception that passive tools such as detection technologies can provide adequate protection, although the evidence clearly demonstrates otherwise.