Cross-platform Trojan attacks Windows, Intel Macs, Linux

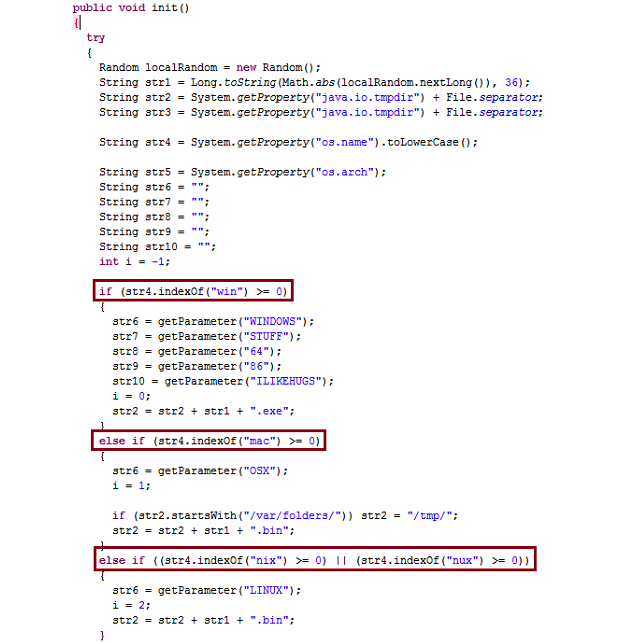
Just like last time, the Trojan downloader checks your operating system so it can pick which malware to download onto your computer. The Web-based social engineering attack relies on a malicious Java applet to install backdoors on Windows, Mac, and Linux computers. When you first visit such a compromised site, you are prompted to install the Java applet, which unsurprisingly hasn't been signed with a certificate. If you do so, the applet checks which operating system you have (Windows, Mac OS X, or Linux) and then drops a corresponding Trojan for your platform.
F-Secure, which first found the Web exploit, detects the initial malware as Trojan-Downloader:Java/GetShell.A. The respective payloads for Windows, Mac, and Linux are detected as follows: Backdoor:W32/TES.A, Backdoor:OSX/TESrel.A, and Backdoor:Linux/GetShell.A. The Trojan downloader was written using the Social-Engineer Toolkit (SET), an open-source and publicly-available Python tool designed for penetration testing.
The security firm says the payloads remain the same, with only their implementations changed. The Windows payload is in the form of a shellcode which is executed using the SET module shellcodeexec.binary, but has the same behavior. Instead of connecting to a remote server to get additional shellcode to execute (which then opens a reverse shell), the OS X binary immediately opens a reverse shell, which attackers can then leverage with ease. The Linux binary remains the same except that it is using a different server.
Malware writers love using a cross-platform plugin as an attack vector because it allows them to target more than one operating system, and thus more potential users. It shouldn't surprise you that Java is being used: the platform has loads of security holes, and it runs on all the major operating systems.
See also:
- Malicious Chrome extensions hijack Facebook accounts
- Malware tricks Facebook users into exposing credit cards
- Up to 1.5 million Visa, MasterCard credit card numbers stolen
- New Flashback variant silently infects Macs
- Wikipedia: If you see ads on our site, you have malware
- New targeted Mac OS X Trojan requires no user interaction
- Over 600,000 Macs infected with Flashback Trojan