Elasticsearch ransomware attacks now number in the thousands

Since last week, ransomware attacks on Elasticsearch have quadrupled. Just like the MongoDB ransomware assaults of several weeks ago, Elasticsearch incursions are accelerating at a rapid rate.
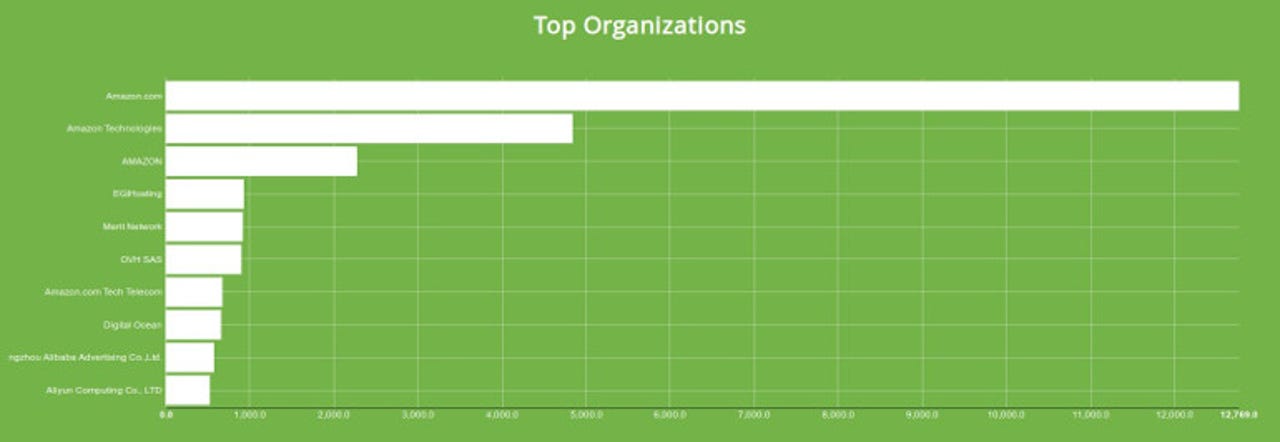
The vast majority of vulnerable Elasticsearch servers are open on Amazon Web Services.
There are an estimated 35,000 Elasticsearch clusters open to attack. Of these, Niall Merrigan, a solution architect who has been reporting on the attack numbers on Twitter, states that over 4,600 of them have been compromised.
Security
If your Elasticsearch server is hacked, you'll find your data indices gone and replaced with a single index warning. The first example read:
SEND 0.2 BTC TO THIS WALLET: 1DAsGY4Kt1a4LCTPMH5vm5PqX32eZmot4r IF YOU WANT RECOVER YOUR DATABASE! SEND TO THIS EMAIL YOUR SERVER IP AFTER SENDING THE BITCOINS...
In return for the .2 BitCoins (not quite $175), you might get your data back.
Elasticsearch is a popular, open-source distributed RESTful search engine. When used with the Lucene search-engine library, it's used by major websites such as Pandora, SoundCloud, and Wikipedia for search functionality. When used by amateurs without any security skills, it's simple to crack.
These wide-open to attack instances are typically being deployed without much on Amazon Web Services (AWS) clouds. Perhaps the people deploying them are under the illusion that AWS is protecting them. Wrong.
AWS does tell you how to protect your AWS Elasticsearch instances, but you still have to do the work. In short, RTFM.
The worst thing about this? Just like the MongoDB attacks, none of this would have happened if its programmers had protected its instances with basic, well-known security measures.
For starters, as Elasticsearch consultant Itamar Syn-Hershko explained in a blog on how to protect yourself against Elasticsearch attacks: "Whatever you do, never expose your cluster nodes to the web. This sounds obvious, but evidently this isn't done by all. Your cluster should never-ever be exposed to the public web."
In a word, "duh!"
Elasticsearch was never meant to be wide-open to internet users. Elastic, the company behind Elasticsearch, explained all this in 2013. This post is filled with such red-letter warnings as "Elasticsearch has no concept of a user." Essentially, anyone that can send arbitrary requests to your cluster is a "super user."
Does this sound like a system you should leave wide-open on the internet for any Tom, Dick, or Harry to play with? I don't think so!
So, what can you do? First, if you're using Elasticsearch for business, bite the bullet and get the commerical version of Elasticsearch. Then, add X-Pack Security to your setup and implement its security features.
By itself, Elasticsearch has no security. You must add it on.
If you're committed to doing it on your own, practice basic security. At a bare minimum this includes:
- Don't run on internet-accessible servers.
- If you make your Elasticsearch cluster internet accessible, restrict access to it via firewall, virtual private network (VPN), or a reverse proxy.
- Perform backups of your data to a secure location and consider using Curator snapshots