Fake Microsoft Patch Tuesday malware campaign spreading
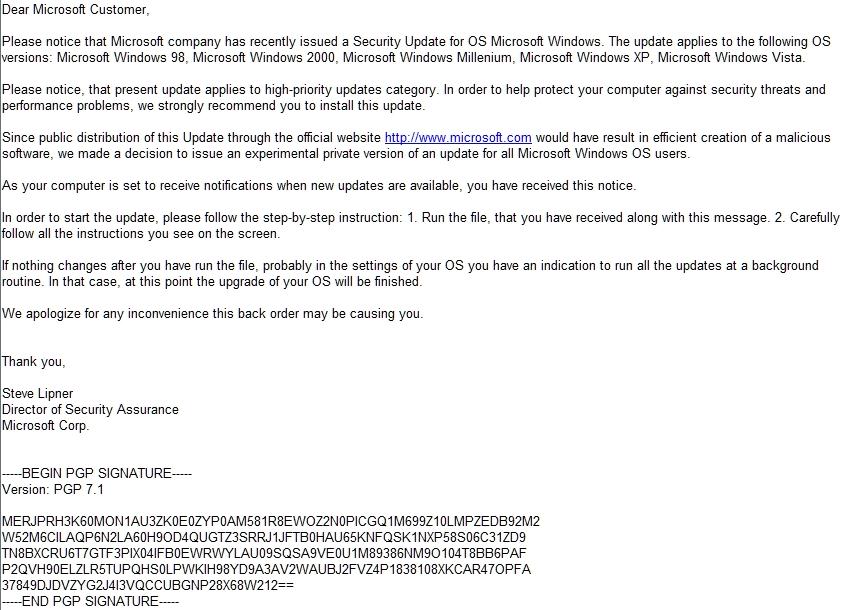
"We received some questions from customers about an e-mail that’s circulating that claims to be a security e-mail from Microsoft. The e-mail comes with an attached executable, which it claims is the latest security update, and encourages the recipient to run the attached executable so they can be safe. While malicious e-mails posing as Microsoft security notifications with attached malware aren’t new (we’ve seen this problem for several years) this particular one is a bit different in that it claims to be signed by our own Steve Lipner and has what appears to be a PGP signature block attached to it. While those are clever attempts to increase the credibility of the mail, I can tell you categorically that this is not a legitimate e-mail: it is a piece of malicious spam and the attachment is malware. Specifically, it contains Backdoor:Win32/Haxdoor."
Is timing everything when it comes to the success rate of such malware campaigns? Not necessarily.
Despite the touch points aiming to improve the trust factor, like mentioning a real Microsoft employee, spoofed FROM field as securityassurance AT microsoft.com, next to the PGP signature, given the fact that the emails aren't personalized and that spam outbreaks spreading malware by capitalizing on Microsoft's brand have cyclical pattern, namely, they re-appear every year (2005, 2007, 2008) the average end user is supposed to have a basic security awareness of this tactic. More info on the campaign :
Furthermore, this backdoor opens several TCP ports that allow remote attackers to connect to the comprmised PC and execute files, steal information from it, or upload and download files. The attachment’s file name varies, but uses the convention KBxxxxxx.exe, where xxxxxx is a random 6-digit number. Below are some of the file names we’ve seen, and are being used:
KB199250.exe KB246586.exe KB535548.exe KB572906.exe KB763412.exe
Compared to the recent targeted malware attack against U.S schools, and the massive fake CNN news items campaign taking advantage of client-side vulnerabilities, this one is definitely going to have a lower success rate - no matter the timing.