First came mass MongoDB ransacking: Now copycat ransoms hit Elasticsearch

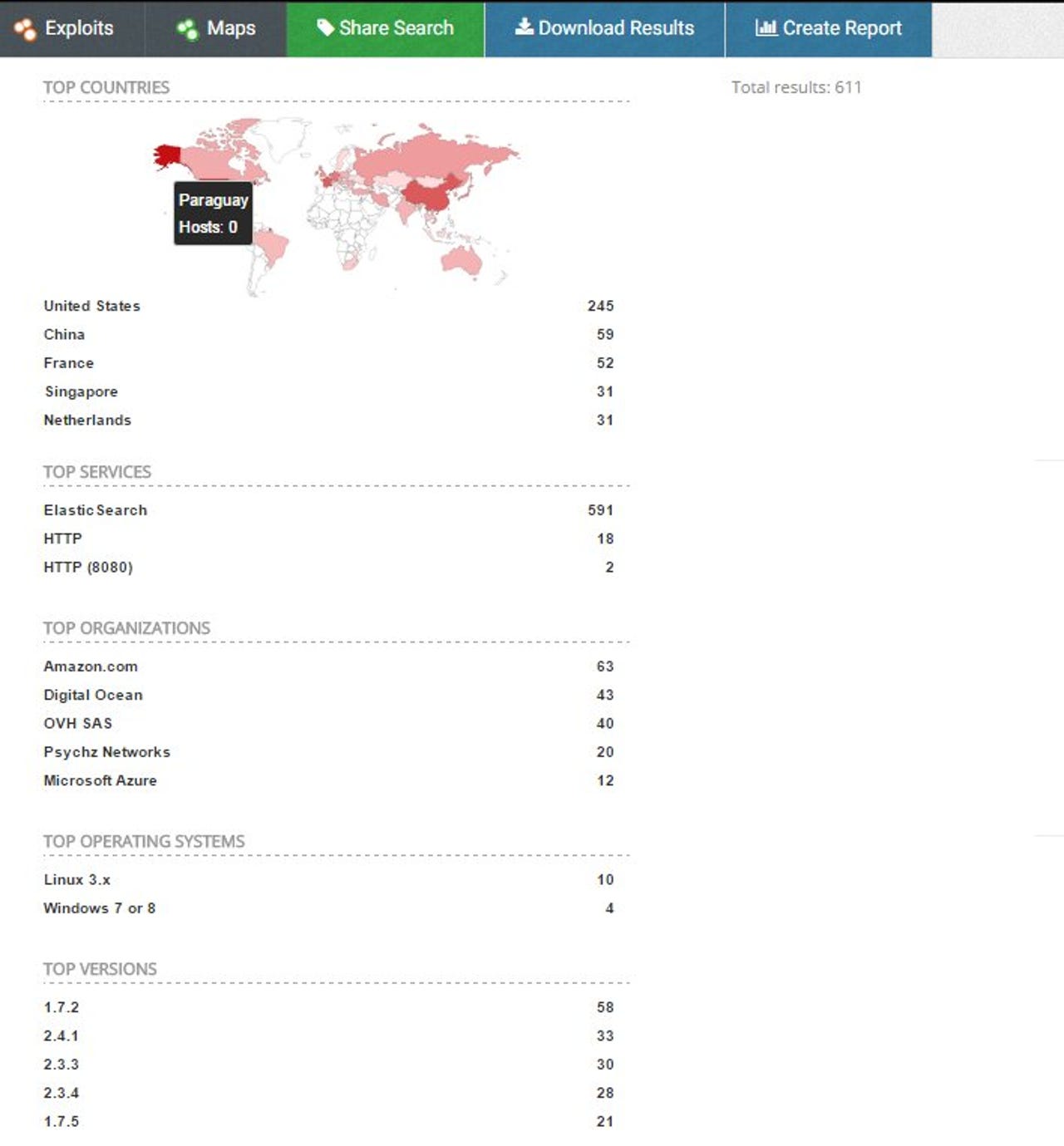
Security researcher Niall Merrigan estimates that more than 600 Elasticsearch instances have now been hit.
Hundreds of Elasticsearch instances have been wiped in the past few hours, in near-identical ransom attacks to those that have hit more than 34,000 unsecured MongoDB databases over the past week.
Developers running Elasticsearch servers are being warned to conceal them from the web to avoid being targeted by attackers who delete data and then demand a payment to return it.
An initial report by The Register counted 360 affected Elasticsearch instances. Security researcher Niall Merrigan, who tracked the MongoDB attacks, has updated that figure to over 600 instances, most of which are hosted in the US, but also China, Europe and Singapore.
If attacks on Elasticsearch instances follow the course of the MongoDB ransacking, the number could rise quickly. John Matherly, founder of the Shodan search engine, has identified 35,000 Elasticsearch servers exposed to the internet, with most of them hosted on Amazon Web Services infrastructure.
Matherly estimated there were 99,000 MongoDB databases exposed to the web. As of Thursday, Merrigan counted 34,000 wiped MongoDB servers, resulting in several hundred terabytes of lost data.
On January 3, only 2,000 MongoDB databases had been replaced with ransom notes. Notably, attackers did not actually copy the wiped data they claimed would be returned upon payment.
Elasticsearch consultant Itamar Syn-Hershko has written a detailed post explaining how developers should configure Elastic clusters to avoid falling victim to the ransom.
Owners of hacked Elastic instances will see the message below demanding payment of 0.2 BTC ($160).
This is what a typical ransom note from the Elasticsearch attackers looks like.
"Whatever you do, never expose your cluster nodes to the web. This sounds obvious, but evidently this isn't done by all. Your cluster should never, ever be exposed to the public web," warned Syn-Hershko.
In the past hour, Mike Paquette of Elastic's engineering team has posted a blog explaining how to protect Elasticsearch against ransom attacks.
While the Elastic-managed version of Elasticsearch hosted on AWS is secured by default, Elasticsearch itself does not perform authentication or authorization and hence needs to be configured properly when accessible by untrusted users.
As per the company's security advice in 2013: "Elasticsearch has no concept of a user. Essentially, anyone who can send arbitrary requests to your cluster is a super user."
Paquette said that Elastic "strongly recommended that unsecured Elasticsearch instances should not be directly exposed to the internet".
For Elasticsearch clusters not managed by Elastic, the company recommends taking the following steps:
- Perform backups of all your data to a secure location and consider Curator snapshots.
- Reconfigure your environment to run Elasticsearch on an isolated non-routable network.
- Or if you must access the cluster over the internet, restrict access to your cluster from the internet via firewall, VPN, reverse proxy, or other technology.
Read more on security
- This phishing scam poses as a charity email, delivers Ramnit banking Trojan malware
- Mobile hacking firm Cellebrite confirms server breach
- House bill aims to block tech giants from building "Muslim registry"
- Days before Trump takes office, Obama expands surveillance powers
- Nobody seems to know what Rudy Giuliani's cybersecurity firm actually does