Four XSS flaws hit Facebook
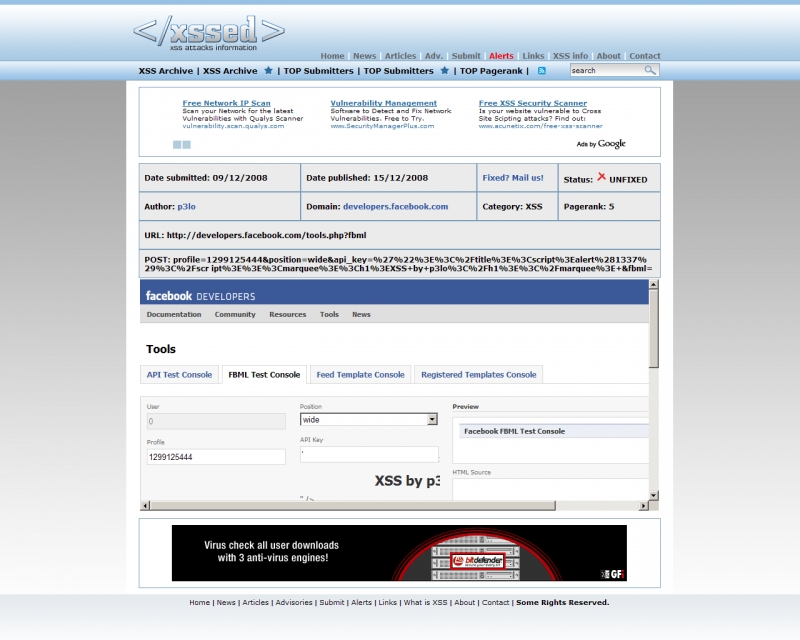
It's worth pointing out that in both of these cases there were no known cases of active exploitation, perhaps due to Facebook's quick reaction upon being notified of them. The very same lack of active exploitation was also present in several other cases throughout the year, namely, the recent XSS affecting Google's login page, and the multiple HSBC sites (still) vulnerable to XSS flaws. And if we are to exclude the XSS worm at Justin.tv which infected 2,525 profiles in July, active exploitation of such flaws is no longer favored compared to the less noisy social engineering tricks exploiting the weakest link - the Internet user social networking with a false feeling of security.
Take Koobface for instance. It scaled so efficiency without exploiting any social networking site specific flaw, only through social engineering tactics forwarding the entire spreading process to the already infected user, which in a trusted environment of friends proved to be a successful form of spreading. Despite the possibility for active exploitation of such flaws in phishing and malware campaigns, cybercriminals appear no be no longer interested in such noisy approaches, at least not while attempting to spread malware across social networking sites. Among the main reasons for this is the fact that their entire campaign would be based on a single propagation vector, which when taken care of through technical measn would render their campaign useless. Instead, just like the Koobface gang continues to do, they mix the social engineering vectors by abusing legitimate brands as redirectors to the malware infected hosts serving the fake YouTube videos.
The Web in general is an entirely different topic, since I can easily argue that the long tail of SQL injected sites can outpace the traffic that could come from a single high-page ranked site that's participating in a malware campaign. Case in point - the recent Internet Explorer zero day flaw is currently being served through SQL injections affecting vulnerable sites across the Web, a pretty logical move on which I speculated given the fact that it was originally used on Chinese forums and sites only.
For the record, the Facebook security team has been notified of the recently published flaws.