Google says Chinese Great Cannon shows need to encrypt web

For a month and a half, China's new Great Cannon attack injected HTML and JavaScript aimed at flooding GitHub and Greatfire.org servers into web requests to popular Chinese search engine Baidu.
Described at the time as a significant escalation of state-level information control and a censorship tool powered by weaponising users, Google said on the weekend that the attack would not have been possible if the web had embraced moves to encrypt its transport layers.
"This provides further motivation for transitioning the web to encrypted and integrity-protected communication," Google security engineer Niels Provos said in a blog post. "Unfortunately, defending against such an attack is not easy for website operators."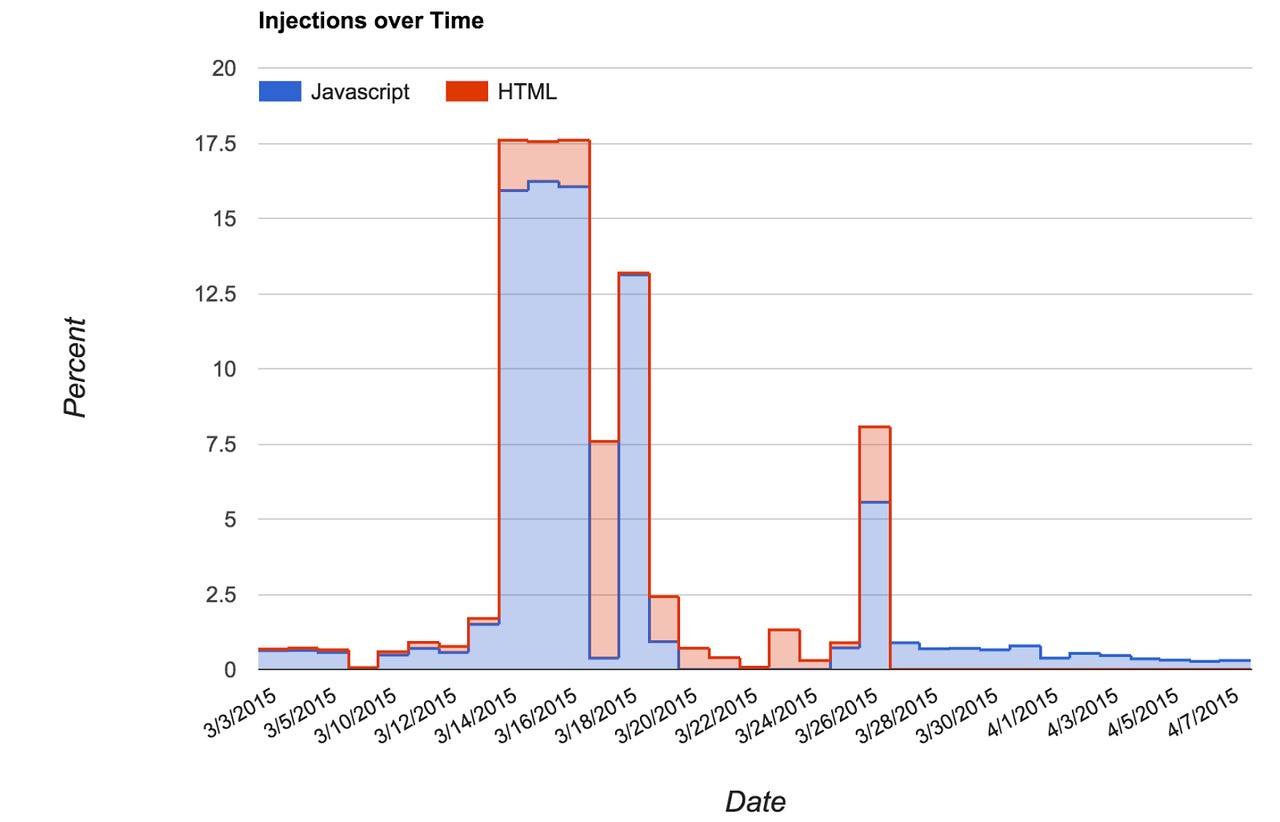
Using analysis from Google's Safe Browsing infrastructure, Provos said the Great Cannon attack lasted from March 1 to April 15, and involved testing phases before the attack ramped up on March 14 against Greatfire.org.
"At first, requests were made over HTTP and then upgraded to to use HTTPS," Provos said. "On March 14th, the attack started for real and targeted d3rkfw22xppori.cloudfront.net both via HTTP as well as HTTPS. Attacks against this specific host were carried out until March 17th.
"At some point during this phase of the attack, the cloudfront hosts started serving 302 redirects to greatfire.org, as well as other domains. Substitution of JavaScript ceased completely on March 20th, but injections into HTML pages continued."
According to Google, on March 25, the attack switched from Greatfire to Github.
"The attack against GitHub seems to have stopped on April 7th, 2015, and marks the last time we saw injections during our measurement period," Provos said.
During the attack, 19 different JavaScript replacement payloads were detected, and although Google said it was unable to determine a number for different HTML attacks, the payloads were similar.
Provos said that although Google's Safe Browsing analysis was limited to HTTP, and therefore could not be pinned on anyone, it showed that hiding such attacks is difficult.
"Another hope is that the external visibility of this attack will serve as a deterrent in the future," he said.