Hackers deface old UTS system, dump user database

One of the subdomains for the University of Technology, Sydney (UTS) fell victim to an attack over the weekend, with hackers, going by the names Apollo and 0day, defacing the sub-site and dumping user information.
The two hackers left a message for the system administrators, telling them to fix their security and to "hire some staff who actually know what they are doing."
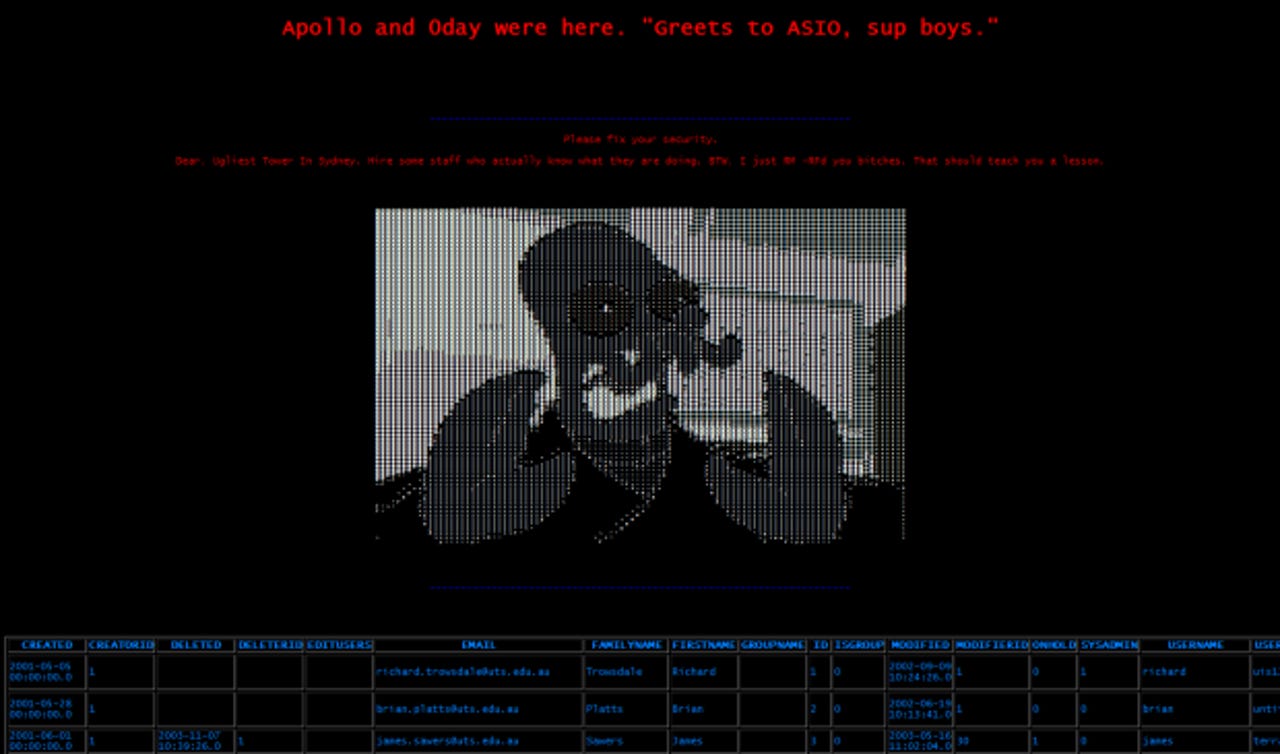
They also claimed to have deleted everything on the server as a lesson and dumped the contents of a database.
UTS confirmed the breach, stating that the server was used to publish news to the UTS website and its IT staff detected it on Saturday morning at 7:45 a.m. AEST. The main UTS website was not affected.
"The affected machine was locked down, and service restored by 9 a.m. on Sunday," UTS said in a statement.
"The university takes any security incident very seriously, and its security team and senior IT staff are working with external security experts to complete an investigation of the source and nature of the attack."
UTS said that none of the university's core IT systems were compromised, and that the data collected and exposed on the defaced page came from a "low-security risk database."
ZDNet understands that the database belonged to an older content management system that is no longer being used. The dumped database also appears to show that the system was created as far back as 2001, and in use at least up to 2004. It contains names and email addresses of staff, their log-ins, and plaintext passwords.
Accounts marked as system administrators also appear to have extremely weak passwords, such as uis123, vanilla and rooftop9.