IBM chides security researchers

Technology giant IBM has taken independent security researchers to task for their role in making information about unpublished computer attacks available in an undisciplined manner.
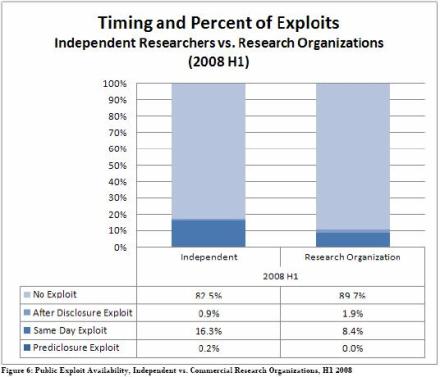
So-called zero-day computer attacks were twice as likely to occur as a result of independent researchers disclosing software bugs than their large organisational counterparts, because of poor disclosure procedures, IBM said in research published this week.
"Zero-day exploits" are those computer attacks that people are able to use before manufacturers can release security updates to block them. They are generally unknown to the public; their name is derived from the age of the attack.
Around 16 per cent of the flaws disclosed by independent security researchers resulted in zero day exploits, while only eight percent occured as a result of research organisation disclosure, according to IBM. Over 3,500 computer security flaws were disclosed in the first half of 2008.
The trend is not surprising, according to IBM, since commercial research organisations normally followed a standard vulnerability disclosure process and typically did not publish exploit code or proof-of-concept attacks.
"If there is not a proper disclosure in terms of giving a vendor time to resolve the issue, then the likelihood of malicious code — a zero day — hitting a publicly available source is highly likely to occur," Pure Hacking security consultant, Chris Gatford told ZDNet.com.au.
Independent researchers were also responsible for exploits that occured prior to any disclosure, according to IBM. The company said organisations never caused these, but 0.2 per cent of exploits of this type were caused by independent researchers.
One such example is the current DNS poisoning fears that have been caused by the DNS flaw discovered by researcher Dan Kaminsky this month. Other security researchers took a punt at the flaw, and apparently were correct, which has lead to a massive patching effort by multiple vendors.
Bug disclosure by independent researchers cause twice as many zero day exploits — but they're not the worst bugs. Credit: IBM
Despite the higher frequency of disclosure by independents resulting in zero-day exploits, Gatford said work done by the likes of Kaminsky was still vital to security.
"If it were not for people like Dan Kaminsky and other notable security researchers finding vulnerabilities in software, we would be constantly running vulnerable software that only the blackhats (malicious hackers) knew how to take advantage of," he said.
But the zero-day exploits that did result from organisations that disclosed flaws were likely to be more dangerous, according to IBM — they were responsible for 80 per cent of vulnerabilities deemed "critical", making zero day exploits that occured from these disclosures more significant.
IBM's research also reported an explosion in web applications flaws. From 2007 to the first half of 2008, web server application flaws accounted for 51 per cent of all vulnerability disclosures and amounted to over 12,000 since the year 2000. These were mostly cross-site scripting flaws, SQL injection, and file include vulnerabilities.
Australian independent software assurance consultant Bill Caelli told ZDNet.com.au the staggering number of software flaws was largely due to a failure by governments to regulate the software industry as it did other industries.
"This [research] now puts extreme pressure on the governments worldwide to stop taking a laissez faire or light-touch legislation approach to the ICT industry," said Caelli.
"There has been 40 years of evidence that industry self-regulation simply has not worked in this industry."
Software developed in the mainframe era decades ago focused on creating "fault tolerance", where systems remained stable and secure even when related software modules failed. Caelli said this idea was now ignored.
"Over the past 25 years, this fundamental approach has been totally ignored by the industry in favour of features and simplicity of user interfaces," he said.
"This is a great political problem, and not a technological one," said Caelli.