IE8 outperforms competing browsers in malware protection -- again
Not only did IE8 top the chart, but also, the rest of the browsers have in fact degraded their "socially engineered malware" and phishing block rate in comparison to the results released by the company in the March's edition of the study.
How objective is the study? For starters, it's Microsoft-sponsored one. Here’s how it ranks the browsers:
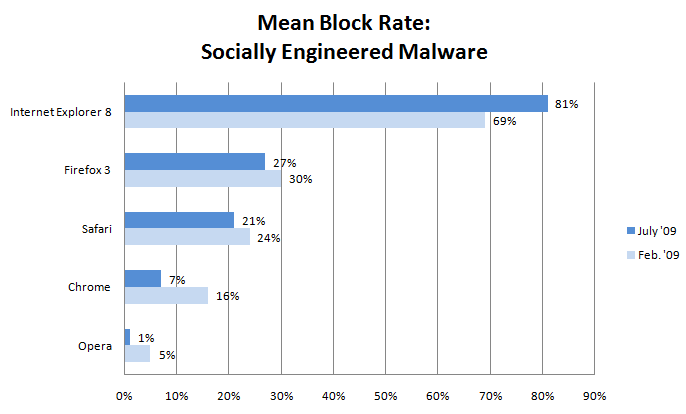
Socially engineered malware block rate:
- Microsoft Internet Explorer v8 - 81% block rate
- Mozilla Firefox v3 - 27% block rate
- Apple Safari v4 - 21% block rate
- Google Chrome 2 - 7% block rate
- Google Chrome 2 - 7% block rate
Phishing attacks block rate:
- Microsoft Internet Explorer v8 - 83% block rate
- Mozilla Firefox v3 - 80% block rate
- Opera 10 Beta - 54% block rate
- Google Chrome 2 - 26% block rate
- Apple Safari v4 - 2% block rate
And even if it is, some pretty realistic conclusions can be drawn by using some internal traffic statistics from Koobface worm's ongoing malware campaigns. The Koobface worm, one of the most efficient social engineering driven malware, is a perfect example of how security measures become obsolete when they're not implemented on a large scale. The stats themselves:
What does this mean? It means that with or without the supposedly working "socially engineered malware" block filter using a modest sample of several hundred URLs, the Koobface botnet is largely driven by MSIE 7 users. The irony is that the previous edition of the study dubbed IE7 a browser which "practically offers no protection against malware" with the lowest block rate achieved back than - 4%.
Just like the previous edition of the study, this one also excludes the notion that client-side vulnerabilities (Secunia: Average insecure program per PC rate remains high; Secunia: popular security suites failing to block exploits) continue contributing to the "rise and rise" of web malware exploitation kits. By excluding client-side vulnerabilities, the study isn't assessing IE8's DEP/NX memory protection, as well as omitting ClickJacking defenses and IE8's XSS filter, once pointed out as a less sophisticated alternative to the Firefox-friendly NoScript.
Socially engineered malware is not the benchmark for a comprehensive assessment of a browser's malware block rate. It's a realistic assessment of the current and emerging threatscape combined with comprehensive testing of all of the browser's currently available security mechanisms, a testing methodology which I think is not present in the study.