Java-based attacks remain at large, researchers say

A new Websense report suggests that approximately 94 percent of endpoints which run Oracle's Java are vulnerable to at least one exploit, and we are ignoring updates at our own peril.
According to security researchers at Websense, it's not just zero-day attacks which remain a persistent threat. Instead, Java exploits are now a popular tool for cybercriminals.
With so many vulnerabilities, keeping browsers up-to-date can become an issue — especially as Java has to be updated independently from our preferred browser, and a mobile, cross-browser workforce is difficult to manage securely. Keeping this in mind, the security team used their Advanced Classification Engine (ACE) and ThreatSeeker Network to both detect and analyze in real-time which versions of Java are currently in use across "tens of millions" of endpoints.
The researchers found that the latest version of Java, version 1.7.17, is only in use by a dismal five percent of users, and many versions are months or years out of date — just begging to be exploited.
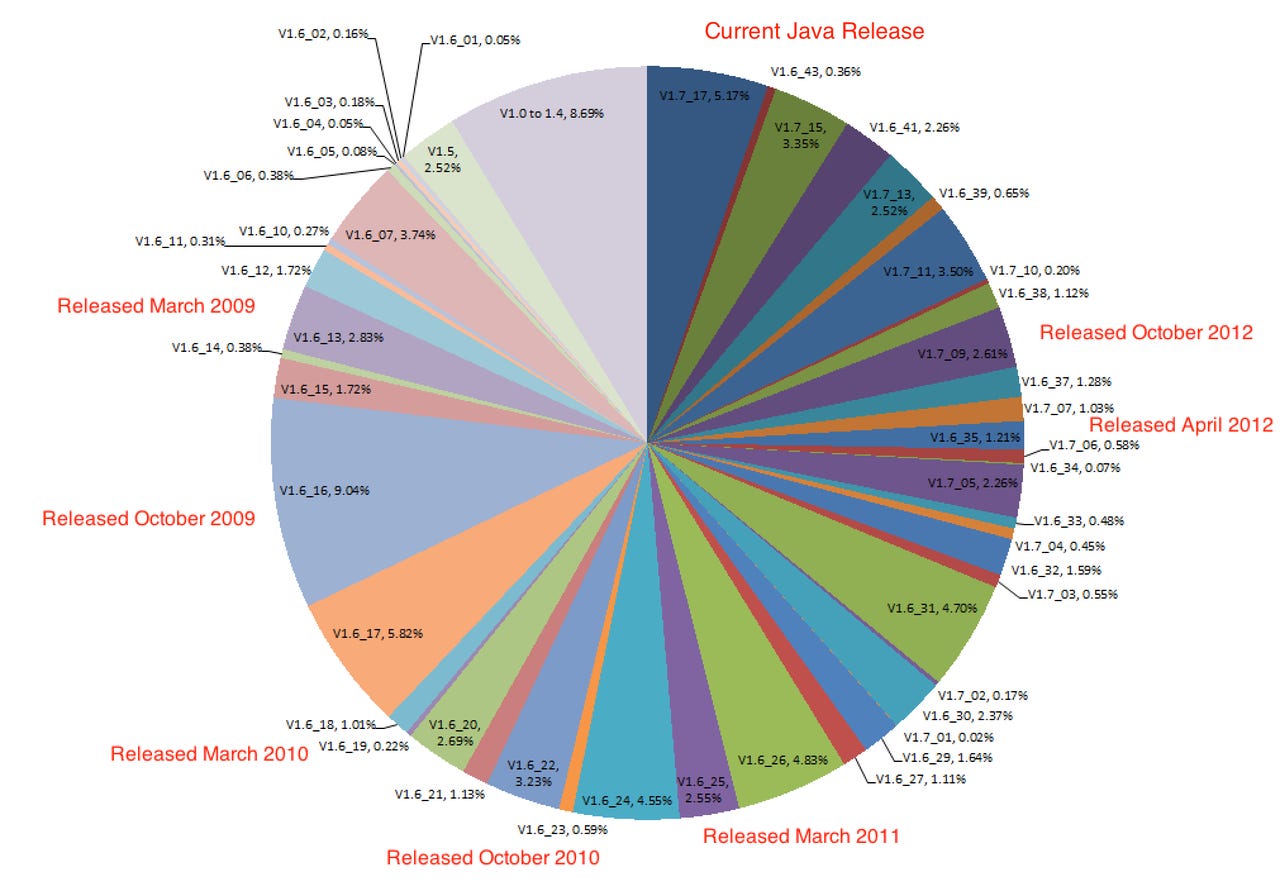
Within the digital attack space, crimeware kits — which can be purchase for as little as $200 — often come supplied with Java-based exploits. The researcher's breakdown of vulnerabilities which have exploit kits available to attack them are thus:
The most widely-detected version of Java currently in use is version 1.6.16. Over 75 percent of browsers are using Java versions which are at least 6 months old, whereas nearly two-thirds are a year out of date, and 50 percent of Java versions in use are over two years behind the times in respect to Java vulnerabilities.
All in all, the researchers say that the vulnerable population of browsers is pegged at a staggering 93.77 percent.
Time to update, folks.
Charles Renert, vice president of Websense Security Labs told Security Week:
"Controls like patch management cannot eliminate risk exposure; they can only reduce risk to what you already know. Given the increasing frequency, severity and sophistication of the latest threats, the risk gap from unknown attacks across these kinds of vectors is on the rise.
Rather than looking to update a single object or signature at a single point in time, companies must review the entire threat lifecycle and examine multiple opportunities to disrupt attacks."