Kaspersky: 12 different vulnerabilities detected on every PC
Researchers from Kaspersky have sampled their customer base, and found out that on average, every PC has 12 different vulnerabilities.
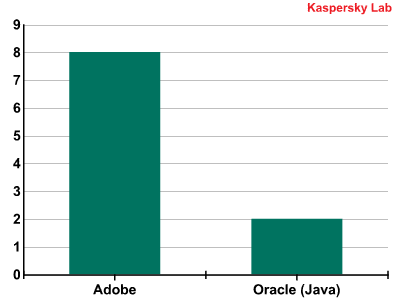
During the second quarter of 2011, the company saw 27,289,171 vulnerable applications and files detected on users’ computers, and detected an average of 12 different vulnerabilities on each computer.
Here are the vulnerabilities discovered:
- Adobe Reader / Acrobat SING "uniqueName" Buffer Overflow Vulnerability
- Sun Java JDK / JRE / SDK Multiple Vulnerabilities
- Adobe Flash Player SharedObject Type Confusion Vulnerability
- Adobe Flash Player Multiple Vulnerabilities
- Adobe Flash Player Multiple Vulnerabilities
- Sun Java JDK / JRE / SDK Multiple Vulnerabilities
- Adobe Flash Player / AIR AVM2 Instruction Sequence Handling Vulnerability
- Adobe Flash Player Unspecified Memory Corruption Vulnerability
- Adobe Shockwave Player Multiple Vulnerabilities
- Adobe Flash Player Unspecified Cross-Site Scripting Vulnerability
The company contributes the decline in Windows vulnerabilities, to improvements in the automatic Windows update mechanism and the growing proportion of users who have Windows 7 installed on their PCs. Moreover, Kaspersky Labs emphasizes on the fact that seven of the Top 10 vulnerabilities are found in one product only — Adobe Flash Player, and that vulnerabilities from 2007-2008 remain in the Top 10, with seven of the ten vulnerabilities were discovered in 2011, and the other three in 2010.
See also
- Secunia: Average insecure program per PC rate remains high
- Study: 6 out of every 10 users run vulnerable Adobe Reader
- 56 percent of enterprise users using vulnerable Adobe Reader plugins
With vulnerabilities found in Acrobat Reader and Adobe products clearly dominating the threatscape, end users and enterprise users should ensure that they are running the latest versions of their installed applications and browser plugins, at any time.