Local root escalation vulnerability in Mac OS X 10.4 and 10.5 discovered
Yesterday, an anonymous reader released details on a local root escalation vulnerability in Mac OS x 10.4 and 10.5, which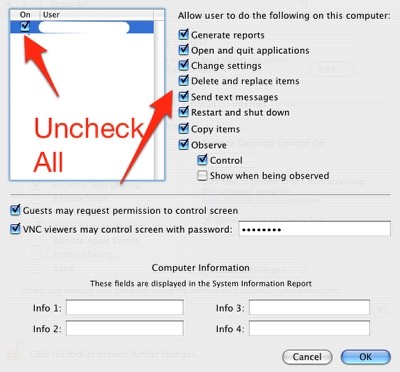
"Half the Mac OS X boxes in the world (confirmed on Mac OS X 10.4 Tiger and 10.5 Leopard) can be rooted through AppleScript: osascript -e 'tell app "ARDAgent" to do shell script "whoami"'; Works for normal users and admins, provided the normal user wasn't switched to via fast user switching. Secure? I think not."
Find out how to fix it.
You've got several possible workarounds, you can remove the Apple Remote Desktop located in /System/Library/CoreServices/RemoteManagement/, or you can go through the visual Workaround for the ARDAgent 'setuid root' problem.
Moreover, the AppleInsider speculates on the potential for abuse :
The effects of malicious code run as root may range from deleting all the files on the Mac to more pernicious attacks such as changing system settings, and even setting up periodic tasks to perform them repeatedly. Not all Macs are vulnerable, however. If a user has turned on Remote Management in the Sharing pane of System Preferences under Mac OS X 10.5, or if a user has installed Apple Remote Desktop client under Mac OS X 10.4 or earlier and has activated this setting in the Sharing preferences, the exploit will not function. Mac OS X 10.5’s Screen Sharing function has no effect on this vulnerability.
And even though the vulnerability can also be executed via a remote connection under specific circumstances based on the configuration, physical security to prevent the unauthorized local access is as applicable as it's always been.