New attack intercepts keystrokes via graphics libraries

Security
A team of academics says they can determine user key presses by watching for data leaks in how a processor computes code from standard graphics libraries.
The general idea behind this research is that the code that renders text on screen via the standard graphics libraries included in modern operating systems leaks clues about the information it is processing, even if the text is hidden behind a password's generic dots.
Also: Why free VPNs are not a risk worth taking
This type of vulnerability --known as a side-channel attack-- isn't new, but it's been primarily utilized for recovering cleartext information from encrypted communications.
However, this new side-channel attack variation focuses on the CPU shared memory where graphics libraries handle rendering the operating system user interface (UI).
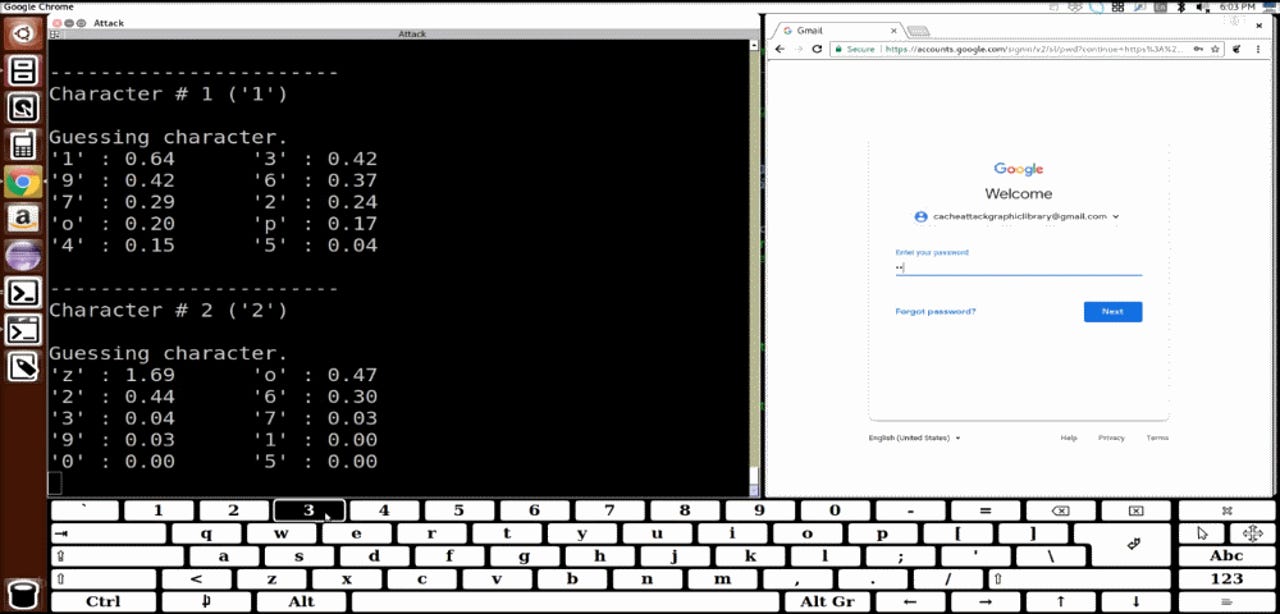
In a research paper shared with ZDNet and that will be presented at a tech conference next year, a team of academics has put together a proof-of-concept side-channel attack aimed at graphics libraries.
They say that through a malicious process running on the OS they can observe these leaks and guess with high accuracy what text a user might be typing.
Sure, some readers might point out that keyloggers (a type of malware) can do the same thing, but the researcher's code has the advantage that it doesn't require admin/root or other special privileges to work.
The attack code can be hidden inside legitimate apps and recover keystrokes with a much lower chance of getting detected by antivirus products.
But the researchers' attack isn't something to worry about just yet. This attack is only theoretical, for now, and would be very hard to pull off by a low-skilled attacker.
Preparing a side-channel attack of this type requires studying how an operating system interacts with its graphics library on specific hardware architectures. An attacker would need to have precise hardware specs of a victim's computer, but also of the software the target uses, from where it intends to steal text (most likely login passwords).
But there are also advantages for this attack. For starters, compared to classic keylogging malware, this attack also works with on-screen keyboards and is not solely limited to collecting key presses from hardware keyboards.
Furthermore, the attack can be tailored to work on any OS, including mobile operating systems. During their tests, researchers captured keystrokes from an Ubuntu and Android OS.
Must read
- Supermicro releases high-density SAS storage chassis TechRepublic
- Super Micro says no evidence of spy chips found in its hardware CNET
In addition, as the attack collects more key presses from graphics libraries, it also gets better at guessing the correct key presses.
The proof-of-concept attack researchers devised for their paper was coded to intercept only numerical and lowercase characters, but researchers say that an attacker can switch to a different prediction model to take into account uppercase letters and special characters if needed.
The research team has also recorded a demo of their attack, embedded below. They also plan to release the source code of their attack in the future.
More details about this attack will be available next year in a research paper entitled "Unveiling your keystrokes: A Cache-based Side-channel Attack on Graphics Libraries," authored by academics from the University of California, Riverside, Virginia Tech, and the US Army Research Lab.
The research team is scheduled to present their work at the Network and Distributed System Security Symposium (NDSS) that will take place in San Diego in late February 2019.
Cybercrime and malware, 2019 predictions
More cybersecurity coverage:
- New machine learning algorithm breaks text CAPTCHAs easier than ever
- Watch researchers remotely brick a server by corrupting its BMC & UEFI firmware
- SQLite bug impacts thousands of apps, including all Chromium-based browsers
- DOD doesn't keep track of duplicate or obsolete software
- US ballistic missile systems have very poor cyber-security
- Super Micro says external security audit found no evidence of backdoor chips