New CryptoLocker ransomware targets gamers

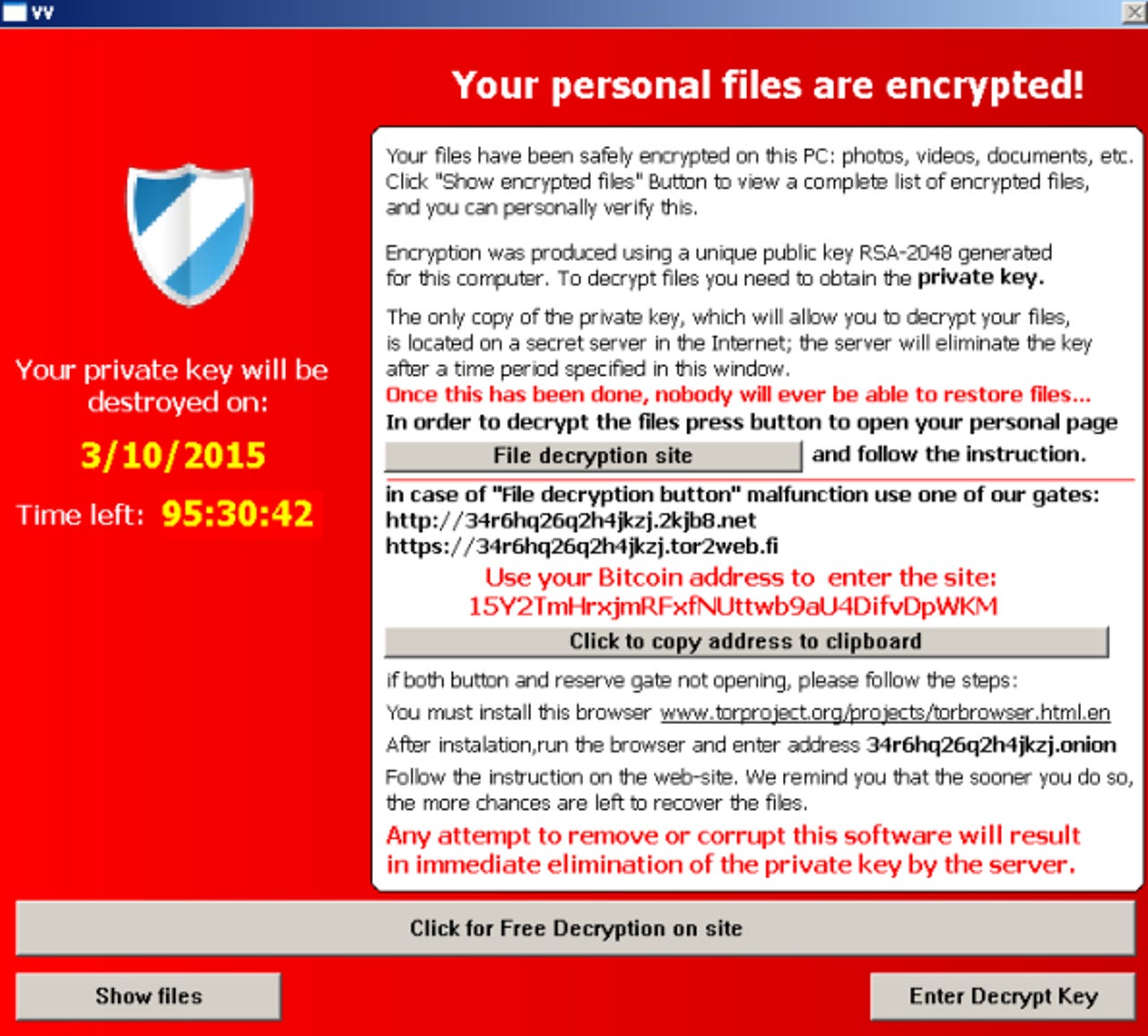
A new variant of CryptoLocker which targets gamers has been discovered in the wild.
On Thursday, Bromium Labs security researchers revealed the existence of new crypto-ransomware which is targeting gamers by making them pay to unlock what they already own. The malware, which impacts data files for over 20 games, is distributed from a compromised website which redirects visitors to the Angler exploit kit by using a Flash clip.
At the time of writing the website has not been revealed, as Bromium Labs researchers have notified the owner but are yet to receive a response.
The Wordpress-based website is still serving malware, and it is not known whether the site has fallen prey to a WP exploit. In addition, the URL which hosts the malicious Flash file keeps changing.
Instead of a typical iframe redirection, the team says the Flash clip is wrapped in a < div > tag, potentially in an attempt to avoid detection. The clip itself makes calls to JavaScript and creates an iframe within, which leads to Angler. Checks are then made for the presence of virtual machines or antivirus software before a recent Flash exploit, CVE-2015-0311 , and an older IE exploit, CVE-2013-2551 , are dropped.
The CryptoLocker variant, dubbed TeslaCrypt and first discovered by Emsisoft's Fabian Wosar, acts like typical ransomware -- locking the victim's system until payment is made. A banner is shown, demanding payment and explaining the user's files have been encrypted. A time limit is also imposed on the victim to try and instill panic and force the user to pay up. The cybercriminals demand payment through a website located via the TOR network.
See also: The ransomware guide
The CryptoLocker strain targets 185 file extensions, which is not a huge amount for this type of malware, but it does selectively focus on video games.
A number of popular single-player games have been affected, including Call of Duty, Minecraft, Dragon Age: Origins, F.E.A.R. and Half-Life 2. In addition, online games including World of Warcraft, Day Z and League of Legends are targets. However, the malware also pursues company-specific files, including EA Sports files, Valve files, Bethesda files and software such as Steam.
The researchers say:
"Encrypting all these games demonstrates the evolution of crypto-ransomware as cybercriminal target new niches. Many young adults may not have any crucial documents or source code on their machine (even photographs are usually stored at Tumblr or Facebook), but surely most of them have a Steam account with a few games and an iTunes account full of music. Non-gamers are also likely to be frustrated by these attacks if they lose their personal data."
To protect yourself from losing data, the team recommends you backup all of your files on an external hard drive regularly. Bromium Labs commented:
"As more file categories are infected, a broader audience is affected. The attackers are also getting better at incorporating BitCoin code directly into their projects. Which isn't a good sign."
Read on: In the world of security
- Anonymous targets ISIS social media, recruitment drives in #OpISIS campaign
- Poor security left Anthem customer records exposed
- Verizon rushes fix for email account open season security flaw
- Sony executive Amy Pascal steps down following cyberattack, email exposure
- Facebook funds GNU Privacy Guard development
Read on: Fixes and Flaws