New LTE attacks can snoop on messages, track locations and spoof emergency alerts

(Image: ZDNet; file photo)
A slew of newly discovered vulnerabilities can wreak havoc on 4G LTE network users by eavesdropping on phone calls and text messages, knocking devices offline, and even spoofing emergency alerts.
Ten attacks detailed in a new paper by researchers at Purdue University and the University of Iowa expose weaknesses in three critical protocol operations of the cellular network, such as securely attaching a device to the network and maintaining a connection to receive calls and messages.
Those flaws can allow authentication relay attacks that can allow an adversary to connect to a 4G LTE network by impersonating an existing user -- such as a phone number.
Although authentication relay attacks aren't new, this latest research shows that they can be used to intercept message, track a user's location, and stop a phone from connecting to the network.
"Our paper discusses in detail how anyone can perform the attacks in practice," Syed Rafiul Hussain, one of the researchers on the project alongside Omar Chowdhury, Shagufta Mehnaz, and Elisa Bertino, told ZDNet in an email.
What the researchers dubbed as LTEInspector is a testing framework that can help detect vulnerabilities in LTE radios and networks.
"Among the 10 newly detected attacks, we have verified eight of them in a real testbed with SIM cards from four major US carriers," he explained. "The root cause of most of these attacks are the lacks of proper authentication, encryption, and replay protection in the important protocol messages."
He explained that these vulnerabilities can be used to spoof the location of the victim device, which could hamper criminal investigations by planting false location information, which could allow criminals to establish false alibis.
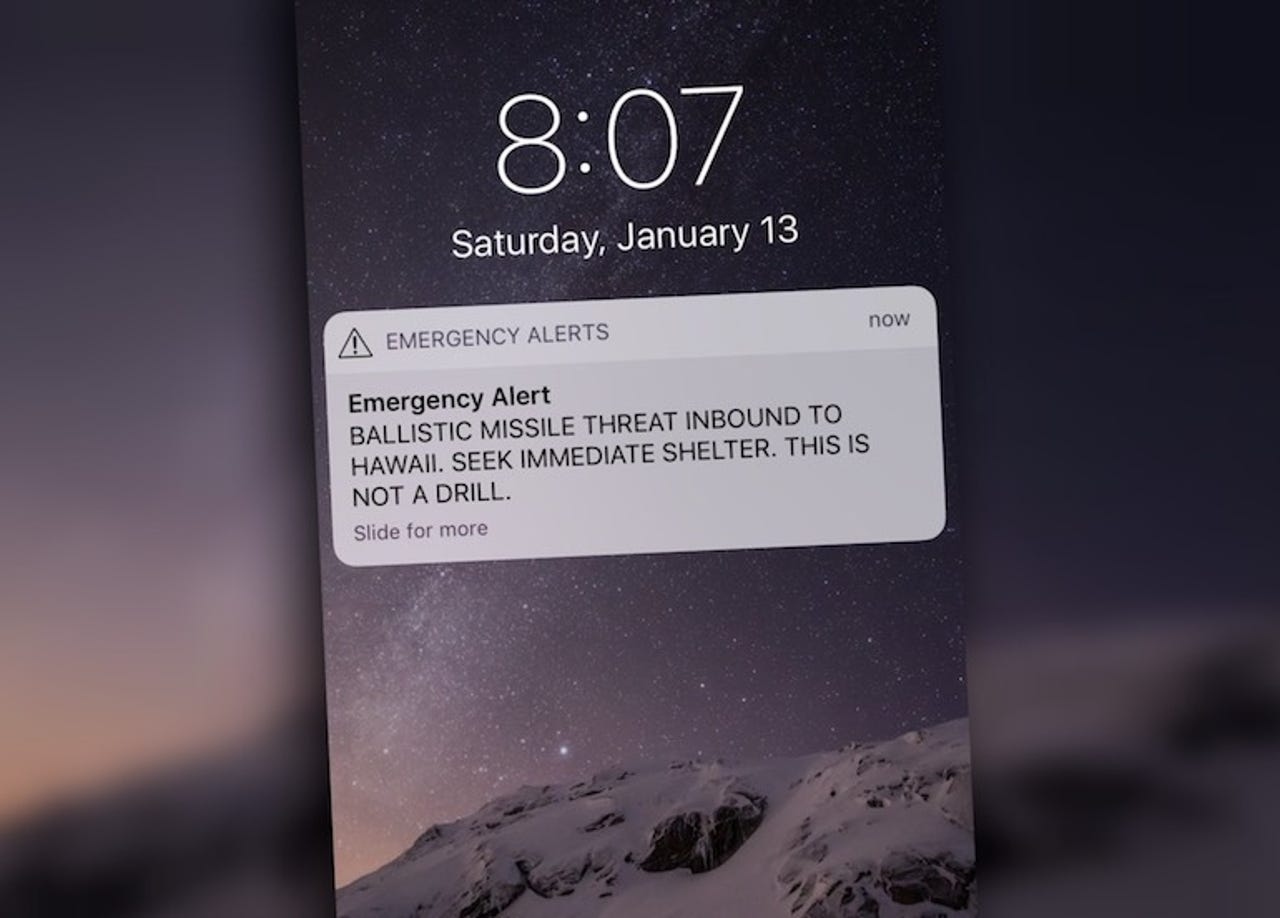
Another attack can maliciously inject warning messages, such as emergency notices and Amber alerts, to devices in a given area to cause "artificial chaos." In January, a mistaken emergency alert claiming to threaten Hawaii with a ballistic missile caused panic.
In one finding, Hussain said, the researchers noticed one major US carrier that "never used encryption for control plane messages which the adversary could exploit to eavesdrop the SMS and other sensitive data," he said.
The carrier, which he did not name, has since implemented a fix.
By using common software-defined radio devices and open source 4G LTE protocol software, anyone can build the tool to carry out attacks for as little as $1,300 to $3,900, making the cost low enough for most adversaries.
The researchers aren't releasing the proof-of-concept code until the flaws are fixed, however.
5G networks promise to be faster and more secure than any cell networks we've seen before, but 4G LTE isn't going away anytime soon -- leaving many of the vulnerabilities open for abuse, potentially indefinitely.
"Retrospectively adding security to such a deployed protocol often requires addressing challenges that are not purely technical," said Hussain.
"It's crucial to be able to test the protocol implementations before they are deployed in practice," he said.