New ransomware locks PCs, demands premium SMS for removal
Following the recently uncovered hybrid scareware with elements of ransomware, and last year's GPcode ransomware attacks, cybercriminals have once again demonstrated their interest in the concept of ransomware.
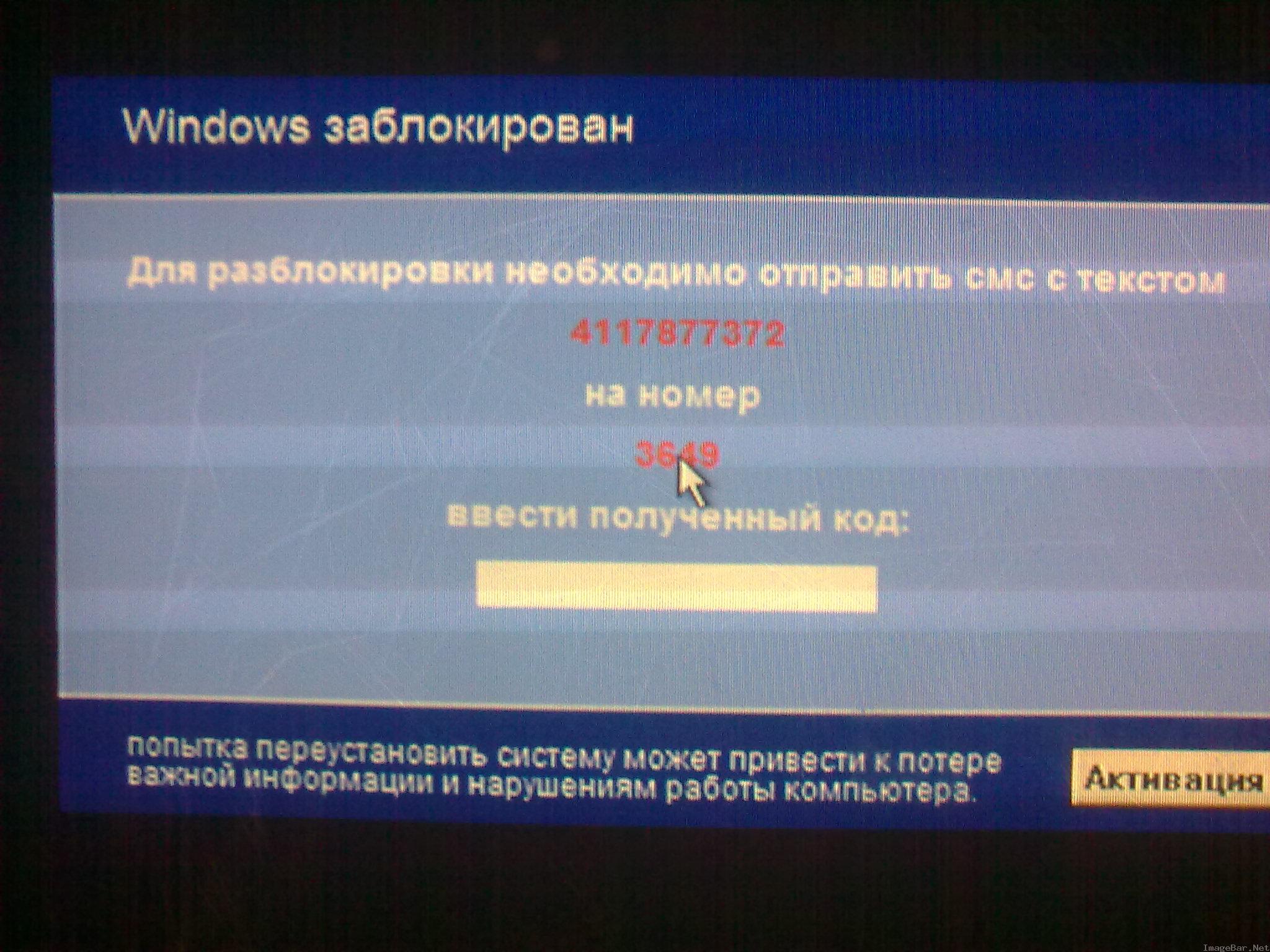
PandaLabs is reporting on a newly discovered ransomware variant which locks the affected user's PC, and demands a premium SMS in order to deactivate it.
Trj/SMSlock.A doesn't have any self-propagation functions and appears to be coming under the form of a typical fake codec that has been affecting users for over a week now. The message (in Russian) demands that the affected user sends an SMS with the pseudo-unique number to the given number in order to receive deactivation code. From a monetization perspective, the approach is pretty similar to the recent Trojan-SMS.Python.Flocker mobile malware which was transferring account credit, and mimicking the original functionality of the RedBrowser mobile malware which was automatically sending SMS messages to premium-rate numbers in 2006.
Just how dangerous is SMSlock.A? Compared to GPcode, it's the work of less technically sophisticated people, making it fairly easy to bypass. Dr.Web has even released a generator for deactivation codes so that affected users don't have to pay.