No longer fun and games: Steam account hijacking becomes booming business

In what security researchers call a "booming business," cybercriminals are developing malware for use against Valve's Steam gaming platform to rob players of their accounts, virtual items and achievements.
PC gaming has always attracted a following, but as broadband replaced slow dial-up services, the upgrade became the catalyst for online gaming platforms. Far removed from the days of handheld consoles, NeoPets, Tetris and Space Invaders, gamers can now stream and purchase games online, play with others across the world and exchange hard cash for virtual items.
There is a downside, however. Just as burglars are most interested in high-value items you have in your home, gamer accounts can also store virtual items and currency worth stealing and selling.
Steam is one of the most popular and largest gaming platforms online today. Catering for over 140 million users, Steam also attracts less savoury types who are willing to break into accounts belonging to others in order to rinse them of everything from characters to virtual items.
Therein lies an avenue for exploit -- and one malware creators are willing to pursue.
Security
In an in-depth investigation of the Steam platform and threats that it faces, Santiago Pontiroli, a researcher with Kaspersky Lab, and Bart P from Panda Security said in a blog post on Securelist that due to Steam's purchase functions and item trading, cybercriminals have become more and more interested in exploiting the platform.
According to the researchers, criminal gangs across Eastern Europe, in particular, have been watching Steam very closely. However, they are not the only ones interested in hijacking and pillaging accounts -- as Steam itself admits to seeing almost 77 thousand accounts taken over fraudulently every month.
This is roughly 2,500 accounts belonging not only to new players but both experienced and professional gamers and contributors which are hijacked per day.
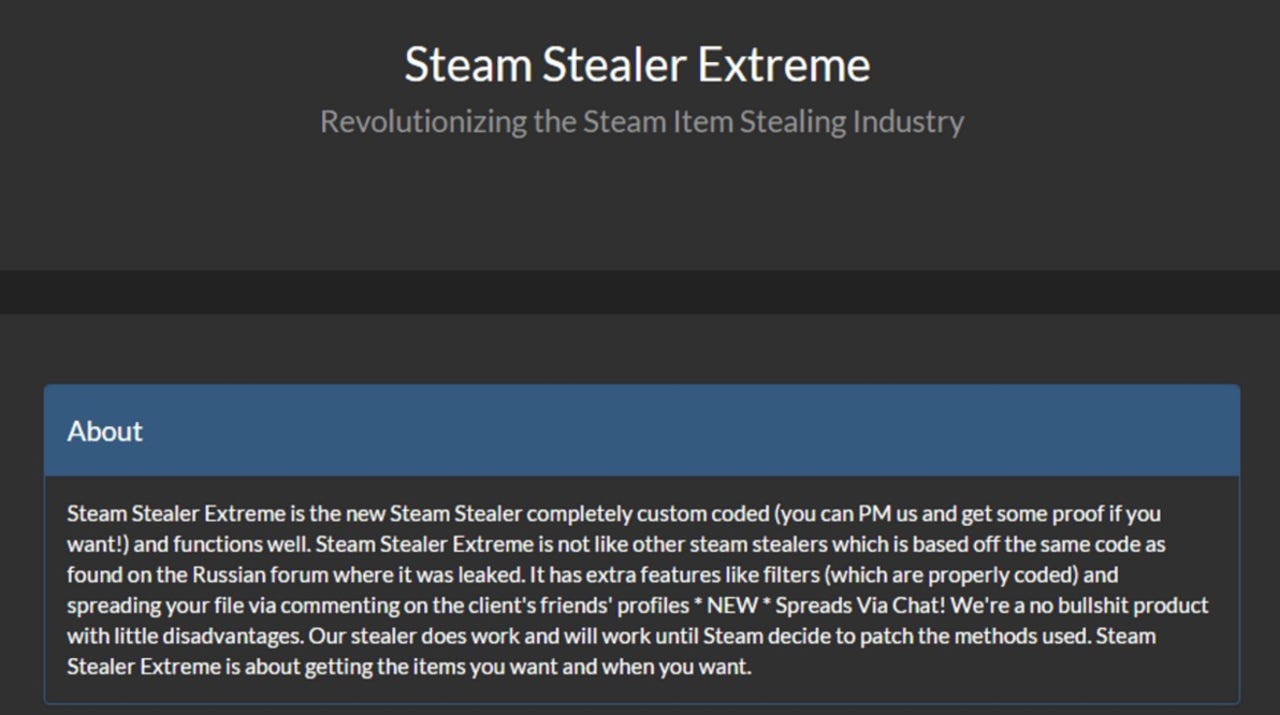
As you can see, this is a serious issue -- and likely only to get worse thanks to Steam Stealer, malware tailored for this purpose and let loose in the wild.
Steam Stealer is the umbrella name for a variety of stealer malware strains based on leaked source code from a Russian underground forum. Now available with different features, specialisations, free upgrades and user manuals, the security team says the "simplicity" of its use is encouraging everyone and anyone to enter the cybercrime scene to get hold of that elusive item or hobble rival gamers by stealing their accounts.
"The focus on selling stealers to anyone with money to spend means that a staggering number of script-kiddies and technically-challenged individuals resort to this type of threat as their malware of choice to enter the cybercrime scene," the team says.
The malware is usually spread through social engineering and fake websites or messages sent directly to victims which contain malicious links.
The Steam Stealer package only requires a user to select their required programming language and comes equipped with an array of APIs and libraries which can be integrated without effort into Steam.
However, it is the bargain price of the package, only $15, which sets this apart from usual malware-as-a-service business models. Usually, prices can reach up to $500 for such user-friendly malware packages, but in this case, just a few extra bucks will get you not only usage rights but the full source code and a user manual.
As a result, few package builds go beyond $30.
Valve knows there is a problem with account hijacking and malware, but theft remains rampant and difficult to control. What Steam gamers can do in the meantime, however, is implement their own security measures -- including implementing two-factor authentication, enforce email confirmations and verification for item trades, changing their passwords regularly and remaining wary of any URLs sent through the platform.
If you make the job difficult, you can likely avoid becoming a victim, as the researchers concluded:
"Remember that cybercriminals aim for numbers and if it's too much trouble they'll move on to the next target."
2016: The best high-end laptops for business users
Read on: Top picks
- How to increase your Bitcoin mining profit by 30 percent with less effort
- SMS Android malware roots and hijacks your device - unless you are Russian
- Bug bounties: Which companies offer researchers cash?
- Shodan: The IoT search engine privacy messenger
- What happens when you leak stolen bank data to the Dark Web?