NSA won't say if it knew about KRACK, but don't look to this leaked doc for answers

(Image via The Intercept/DocumentCloud)
The National Security Agency won't say if it knew about KRACK, a security vulnerability in a widely used wireless protocol that was revealed earlier this week.
Security
A spokesperson for the NSA declined to comment when reached, though the agency's own Information Assurance Directorate issued an advisory Wednesday warning of the vulnerability.
The agency's lack of response isn't all that surprising given that the agency almost never comments on matters of intelligence or national security, but it's hardly likely to dampen rumors that the NSA knew something about the vulnerability in the WPA2 wireless security protocol, which was revealed this week.
Under the vulnerabilities equities process (VEP), the intelligence community is supposed to submit vulnerabilities to ensure that, when appropriate, flaws are disclosed. In some cases, flaws aren't disclosed because they can be useful for intelligence purposes. The FBI and NSA uses exploits for undisclosed flaws to target computers and networks as part of its foreign intelligence missions.
In case you missed it: News broke this week that a vulnerability affects almost every modern Wi-Fi device today. The vulnerability is in the WPA2 security protocol, which debuted in 2004 when it replaced an older and broken security protocol, WEP.
At its worst, the vulnerability -- if exploited -- would allow an attacker to decrypt network traffic from a WPA2-enabled device, hijack connections, and inject content into the traffic stream -- or, in other words, an attacker would have a skeleton key to access any WPA2 network without a password.
The caveat is that an attacker would need to be within a close physical proximity to the Wi-Fi network to carry out the attack.
Given how involved the NSA has been with remote and local exploitation of networks, systems, devices, and even individuals, many put two and two together and assumed the worst.
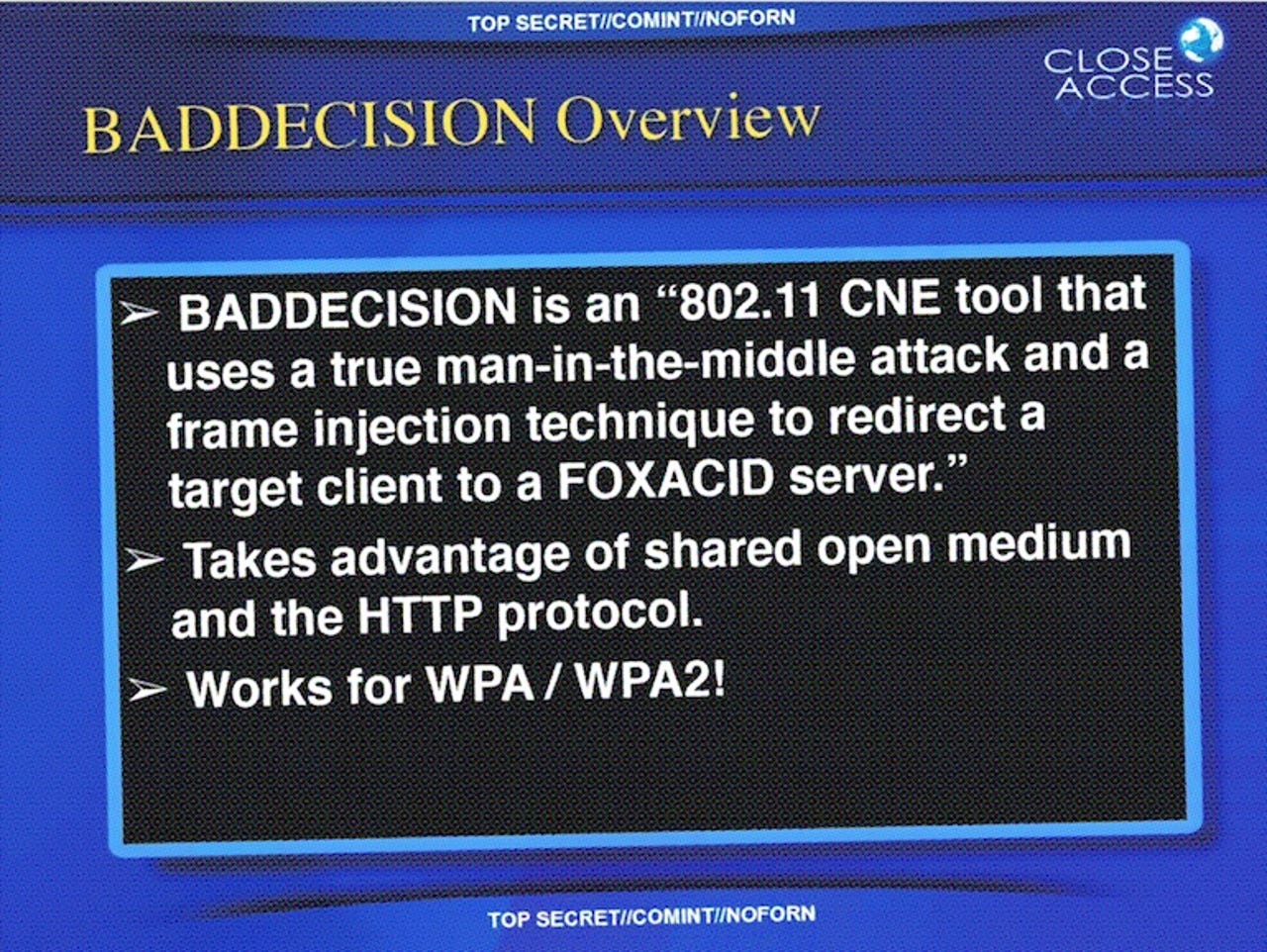
What compounded the matter was that some were pointing to a 2010-dated top secret NSA document leaked by whistleblower Edward Snowden, which detailed a hacking tool called BADDECISION, an "802.11 CNE tool" -- essentially an exploit designed to target wireless networks by using a man-in-the-middle attack within range of the network. It then uses a frame injection technique to redirect targets to one of the NSA's own servers, which acts as a "matchmaker" to supply the best malware for the target device to ensure it's compromised for the long-term. The slide said the hacking tool "works for WPA/WPA2," suggesting that BADDECISION could bypass the encryption.
Cue the conspiracy theories. No wonder some thought the hacking tool was an early NSA-only version of KRACK.
KRACK vulnerability coverage: WPA2 security flaw puts almost every Wi-Fi device at risk of eavesdropping | Here's every patch for KRACK Wi-Fi vulnerability | Special report: Cyberwar and the Future of Cybersecurity | How the cybersecurity elite are working to prevent a digital apocalypse | A guide to the frightening future of online conflict | Ransomware: An executive guide to one of the biggest menaces on the web
But several security researchers, experts, and former NSA staffers we spoke to dismissed the idea.
"This isn't KRACK," said one former NSA staffer, who asked not to be named.
The exploit is an agency version of Ettercap, a publicly available tool that conducts man-in-the-middle attacks to carry out address resolution protocol (ARP) spoofing or poisoning, as it's also known, the person said.
ARP spoofing exploits a lack of authentication in the protocol, effectively allowing an attacker to trick a target device on a wireless network into sending traffic to a malicious device.
Others we spoke to, like Nicholas Weaver, a senior staff researcher at the International Computer Science Institute in Berkeley, Calif., also pointed to ARP spoofing as the method of attack.
"ARP spoofing is effectively the same thing as DHCP spoofing, you're responding to a broadcast request you aren't supposed to," he said.
When reached, even Vanhoef said that he didn't think the NSA program had anything to do with the KRACK vulnerability he discovered.
"It seems they use ARP poisoning to get a man-in-the-middle position," said Vanhoef. "But that would mean they can connect to the WPA2 network, and hence have the correct credentials."
"From that perspective, it doesn't seem to attack WPA2 encryption," he said.
The NSA, for its part, might have the financial resources and the computational firepower to break into networks and covertly spy on billions using hardware and software vulnerabilities.
But, as times have shown, the agency isn't as omnipotent in cyberspace as some people might think.