NSA malware infected over 50,000 computer networks worldwide

A new slide leaked by Edward Snowden shows where the NSA infected more than 50,000 computer networks worldwide with malware, according to Dutch media outlet NRC.
The NSA management presentation slide from 2012 shows a world map spiderwebbed with "Computer Network Exploitation" access points in more than 50,000 locations around the globe.
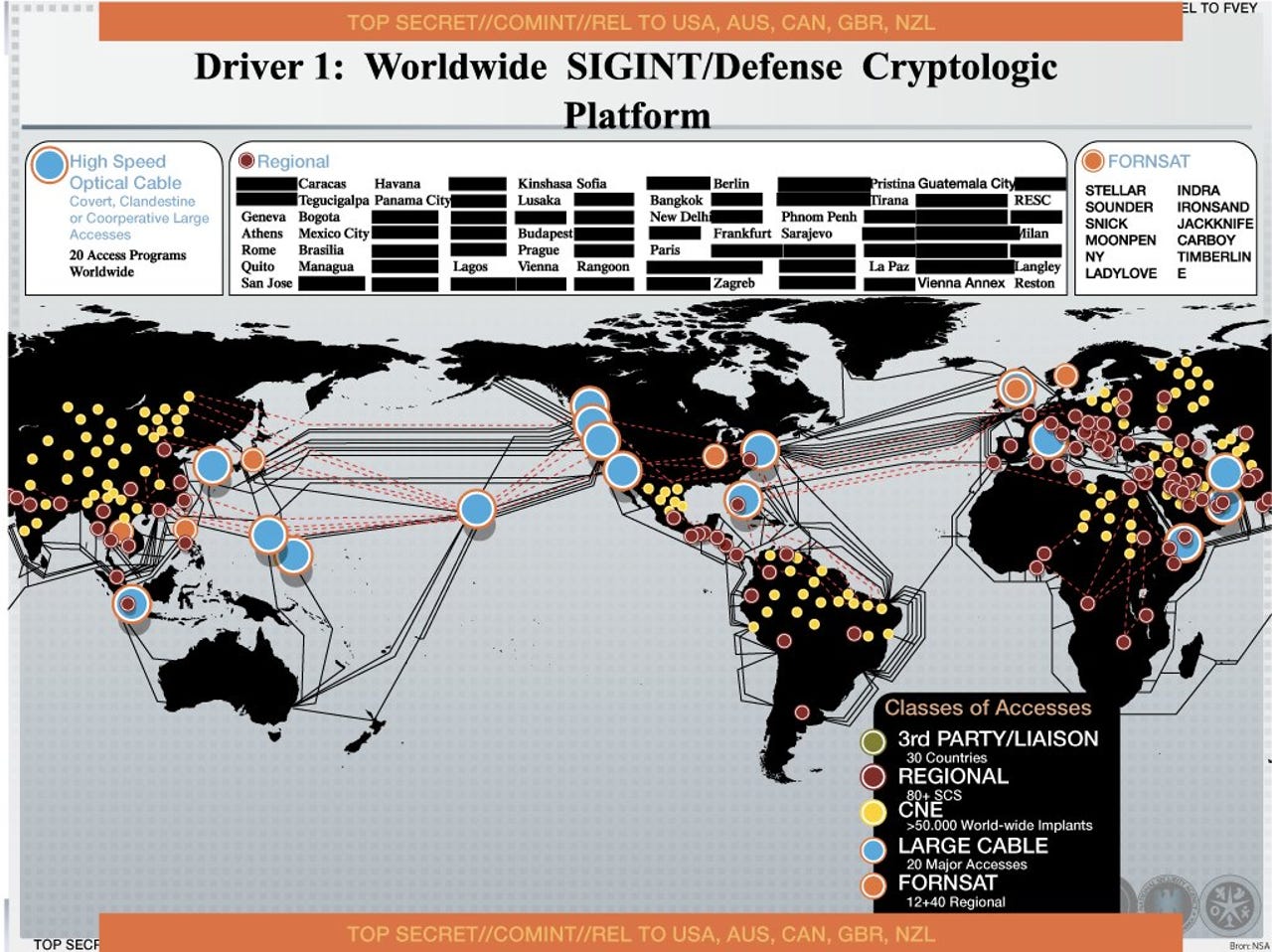
Like all the slides we've seen so far, this one is unlikely to win a Powerpoint beauty pageant anytime soon.
Not that this should deter anyone from the profoundly disturbing implications of a US government malware map being reported by a Dutch news agency -- to which the US government gave a "no comment."
Translated from Dutch:
The American intelligence service - NSA - infected more than 50,000 computer networks worldwide with malicious software designed to steal sensitive information.
Documents provided by former NSA employee Edward Snowden and seen by this newspaper, prove this.
(...) The NSA declined to comment and referred to the US Government. A government spokesperson states that any disclosure of classified material is harmful to our national security.
On the NSA's Computer Network Operations program description page it describes CNE as, "Includes enabling actions and intelligence collection via computer networks that exploit data gathered from target or enemy information systems or networks."
In an article dated August 29, 2013, The Washington Post reported on the NSA's "hacking unit" called Tailored Access Operations (TAO).
The Post wrote:
According to a profile by Matthew M. Aid for Foreign Policy, it's a highly secret but incredibly important NSA program that collects intelligence about foreign targets by hacking into their computers, stealing data, and monitoring communications.
(...) Dean Schyvincht, who claims to currently be a TAO Senior Computer Network Operator in Texas, might reveal the most about the scope of TAO activities.
He says the 14 personnel under his management have completed "over 54,000 Global Network Exploitation (GNE) operations in support of national intelligence agency requirements."
This is one letter away from being exact.
Read this
On the NSA's network ops page, there is no program with the acronym GNE - only CNE and,
Computer Network Attack (CNA): Includes actions taken via computer networks to disrupt, deny, degrade, or destroy the information within computers and computer networks and/or the computers/networks themselves.
Computer Network Defense (CND): Includes actions taken via computer networks to protect, monitor, analyze, detect, and respond to network attacks, intrusions, disruptions, or other unauthorized actions that would compromise or cripple defense information.
Across the slide top and bottom a stripe reads, "REL TO USA, AUS, CAN, GBR, NZL."
These are the so-called "Five Eyes" nations -- which include the U.S., U.K., Canada, Australia, and New Zealand.
Last week, the very same "Five Eyes" nations moved to oppose the United Nation's anti-surveillance, right-to-privacy draft resolution called "The right to privacy in the digital age".
Security researchers online are speculating that telecoms were the most likely targets for the malware.
Only 50k milware installations globally? Must be restricted to the telcos, ISPs, banks, etc that allow for bulk collection.
— the grugq (@thegrugq) November 23, 2013
They may not be too far off the mark.
NRC cites an example of Britain's intelligence service GHCQ, being found to use spoofed LinkedIn pages to install surveillance malware on target computers in Belgium telecom, Belgacom (translated):
One example of this type of hacking was discovered in September 2013 at the Belgium telecom provider Belgacom.
For a number of years the British intelligence service - GCHQ - has been installing this malicious software in the Belgacom network in order to tap their customer's telephone and data traffic.
The Belgacom network was infiltrated by GCHQ through a process of luring employees to a false Linkedin page.
NRC concludes its explosive article by telling us that the Dutch government's intelligence services has its own hacking unit, but is prohibited by law from performing the type of operations the NSA appears to have done in the CNE slide.
Unlike the feeling here in the US, where it's starting to feel like an ordered state against which a transgression can be measured has nearly vanished, and is almost forgotten.