Here's how the NSA spied on UN leaders and targeted DDoS attackers

No matter what you've done on the internet, you can bet the National Security Agency has a record of it.
Newly released documents leaked by Edward Snowden shed light on the scale and scope of the XKeyscore program, a program described by one classified document as the "widest-reaching" system for gathering information from the internet.
The new batch of documents detail one of the most extensive programs used in the US government's arsenal on global surveillance, more than two years after it was first revealed by The Guardian .
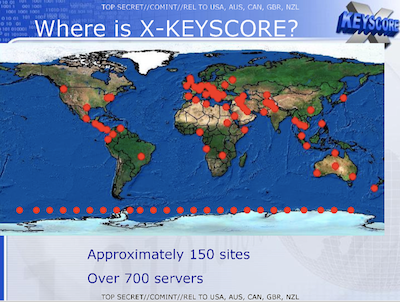
The program, which runs on hundreds of Red Hat Linux-based servers scattered around the globe (likely in US Embassy buildings), allows analysts to filter the vast amount of incidental data created when a user browses the web. The program allows analysts to selectively pick out usernames and passwords, browser history, emails sent and received, social media data, and even locations and detect whether or not a computer is vulnerable to certain kinds of malware or other threats.
A single unique identifier, such as a username, password, email fragment, or even images, can be used to trace a person's online activities with extreme precision. One of the documents said the program was successful in capturing 300 terrorists based on intelligence it had collected.
Out of all the programs, XKeyscore may be the largest in scope, with some field sites sifting through more than 20 terabytes of data per day, according to The Intercept , collected from the various fiber cables around the world.
The newly-released trove of documents details a broader scope of access to personal information that NSA analysts have.
Those include:
- The NSA was able to acquire talking points UN Secretary General Ban Ki-moon wanted to bring up with US President Barack Obama through the Blarney program, which feeds the XKeyscore program. (Blarney is thought to be a program that taps fiber optic cables at core internet choke points around the US and the world.)
- When a group of people overload a server or network with a flood of network traffic (causing a "distributed denial-of-service" or DDoS attack), users can be identified using XKeyscore. One document boasts of how "criminals" can be found through the program.
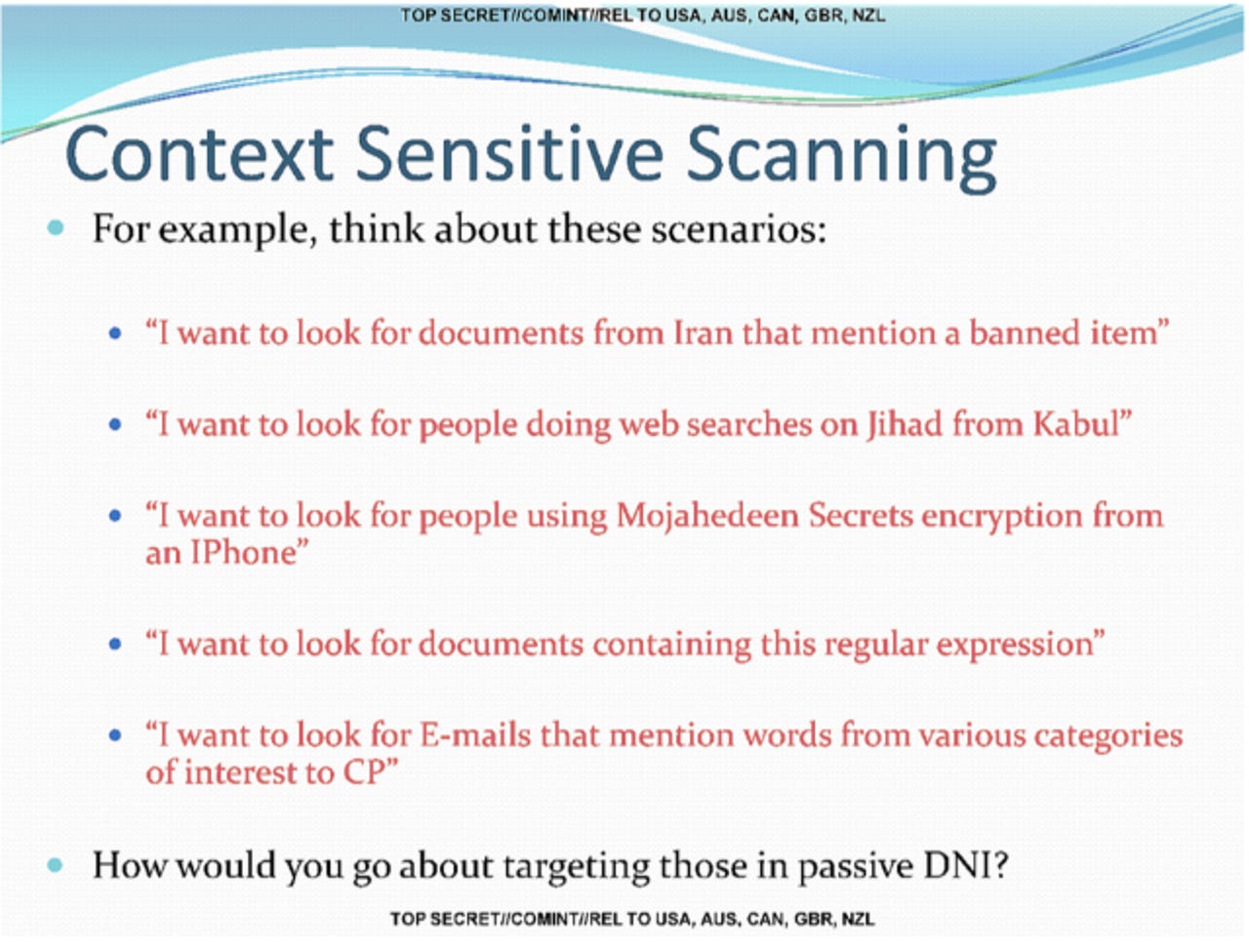
- NSA analysts can plug in queries such as "show me all the exploitable machines in [whichever] country" and have returned to them a list of computers and devices that are vulnerable to the hacking exploits of the NSA's elite intrusion unit, known as Tailored Access Operations (TAO). That also extends to "find all iPhones in Nigeria," or "find Germans living in Pakistan."
- Oversight of the program is limited at best. The system is littered with reminders not to breach human rights' laws or minimization procedures designed to prevent Americans' data from being used by the program. Yet, not everything is audited. System administrators often log in to the program under one username, "oper," which is used across multiple people and divisions, making any actions carried out under that name almost impossible to track.
- XKeyscore can search other databases, like Nucleon, which "intercepts telephone calls and routes the spoken words" to a database. (So yes, the US government is listening to some people's phone calls.) One newly-released document showed more than 8,000 people are ensnared by the program, with more than half-a-million voice files recorded each day.
- An al-Qaeda operative is said to have searched Google for his own name, among other aliases, which was picked up by the XKeyscore program, another document shows .
- The program is able to snoop inside documents attached to emails, one document says . That supposedly can help determine who had authored a Word or PowerPoint document.
- NSA has its own internal online newspaper, a document shows , which the agency dubs the "NSA Daily." It's a top secret publication, which only agents belonging to UK, US, Australian, Canadian, and New Zealand intelligence agencies can access.
The NSA said in a statement (of which portions had been used in previous statements) that its foreign intelligence operations are "authorized by law" and are "subject to multiple layers of stringent internal and external oversight."