One of my sites got hacked, and it's my own fault

It started with a text message from my wife: "ZATZ site hijacked by nasty porn." This is not exactly the message you want to get at 6pm on July 3rd. I had been planning on beginning my holiday weekend with a prolonged sittin'-on-the-couch-watchin'-TV night, but that was not to be.
Instead I'd be doing porn removal, which took until about 2am.
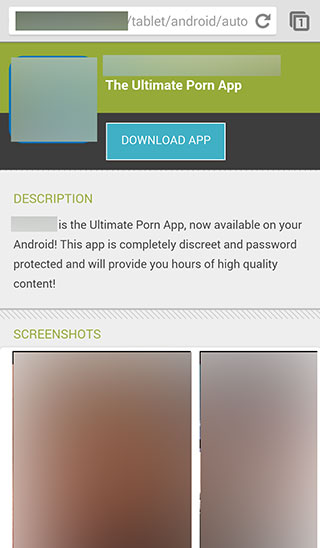
The thing is, I know better. In fact, sometime in the middle of 2013, I made a decision that led directly to my couchless July 3rd. I pretty much knew it would reach out and bite me, and it did.
Here's what happened. In today's world, all web sites are moving targets. It's always an arms race between website operators and the spammers and scammers out there who want to use them for anything from malware distribution to automated referrals to porn sites.
Because it's an arms race, it's up to the website operators to constantly update their sites, update the server software running on their sites, and update their protection systems. Failure to do all of these leaves the chance that bad guys will find a loophole, and tunnel their way in.
That's what they did on my site. What happened is they embedded a redirect message into just the mobile version of the site. As a result, if I visited the site via my desktop browser, everything looked fine. But if you visited the site via a mobile browser (as my wife did on Thursday while at Sam's Club, when she was updating our business membership), you'd find that criminals had gotten into the site's code and replaced it with a redirect to the porn site.
This was fully preventable.
And yes, I understand the irony of a cybersecurity expert getting hacked. It's like the old story of the barber who never cuts his own hair. While I would never advise anyone to leave a site untouched, there is one difference between Mr. Highfalutin Cyberwarfare Advisor being hacked and a regular website operator: I do know how to fix it. That said, mitigation sucks, especially when it gets in the way of a planned night off.
Here's how we got to this point. The ZATZ site is no longer actively updated. It was a highly visited site back in the day, but since I've moved on with my career from entrepreneur to advisor, columnist, and educator, the thousands of ZATZ articles are really now just an archive. We don't get any advertising income (although some old ads are still running on the site), and I rarely spend any time there.
It is a WordPress site. A few years ago, I moved it from UserLand Frontier to WordPress, specifically because of the high level of support available in the WordPress world. There is one disadvantage of WordPress though: given that a huge number of sites run WordPress, it's also a very visible target for hackers.
There are a wide variety of ways to harden a WordPress site, including using a many different security plugins. The ZATZ site was hardened, and it did use the security plugins.
So where did I go wrong, and why was it my fault?
While there are many things you should do to keep a WordPress site from being hacked, there is one golden rule (and it's the one I violated): always keep WordPress up to date. This includes updating the WordPress core, any themes you use, and any plugins.
I didn't do this. Around August of last year, I made a ruthless prioritization decision: leave the websites alone and work on other stuff. I sometimes have to be ruthless about how I prioritize my time, and this was a big one. I knew there was a chance of hacking, but I just didn't want to spend a weekend every few months fiddling with the site. I had an overwhelming amount of other things going on, and this just wasn't as important.
So I let the site sit.
Featured
Updating it would have required installing a new version of WordPress and paying about $800 for updated themes and plugins. Not only did I decide to make website management a lower priority (after all, this was no longer an income-producing site), but I also didn't want to spend much more money on it.
Time went on. The WordPress developers and the various plugin and theme developers updated their offerings, many times finding and fixing exploits. My site sat stuck in time, two revisions behind. As a result, my site still had the exploits.
And so, that led to my Thursday night, where I had planned to binge watch Netflix, and instead spent the night calling in the Marines and updating my website.
Thankfully, because WordPress is so popular, there is a tremendous aftermarket of resources for it, including hack-mitigation services. I'm very familiar with some of them, having met many of the developers at WordCamp. It would take a whole lot more time for met to find the hacks and remove them than to bring in one of these services.
I chose Sucuri because the company offers a free malware scanner (which I'd advise you to run on your sites right now), as well as a 24/7 monitoring and hack mitigation service. For one site, they charge $89, but for up to five sites, they charge $189. I figured that since I had other sites as well, I might as well spring for the five site service and have them check the other sites.
Within about two hours, they found and removed the offending malware, but they were quite insistent on the one thing I'd known all along: it was time to update the site.
So that's what I've been doing, on and off, for most of the weekend. I got the ZATZ site updated by 2am on Thursday, and in-between celebratory picnics, too much smoked duck, and other fixin's, I've been fixin' my sites. I've gone down the list and updated each of the sites, so they're now all robust and up-to-date.
Most — all but the most trivial — are monitored constantly by Sucuri for breaches. I'm also considering using something like InfiniteWP, ManageWP, or MainWP to provide a centralized management console for all my sites.
I got out of this hack pretty easily. Even so, being hacked is no fun, I didn't expect to spend nearly a grand in updates and services this weekend, and I never did get to binge-watch Netflix.
The most important takeaway, however, is this. No website can be stuck in time, even if the content is. The server software and security systems supporting the site must be constantly updated to prevent incursion and corruption. That sucks, but that's the world we live in.
What do you use to harden your WordPress sites? Let me know in the TalkBack below.
By the way, I'm doing more updates on Twitter and Facebook than ever before. Be sure to follow me on Twitter at @DavidGewirtz and on Facebook at Facebook.com/DavidGewirtz.