OS fingerprinting Apple's iPhone 2.0 software - a "trivial joke"
Just like every decent web service out there wanting to identify the iPhone's mobile Safari browser in order to serve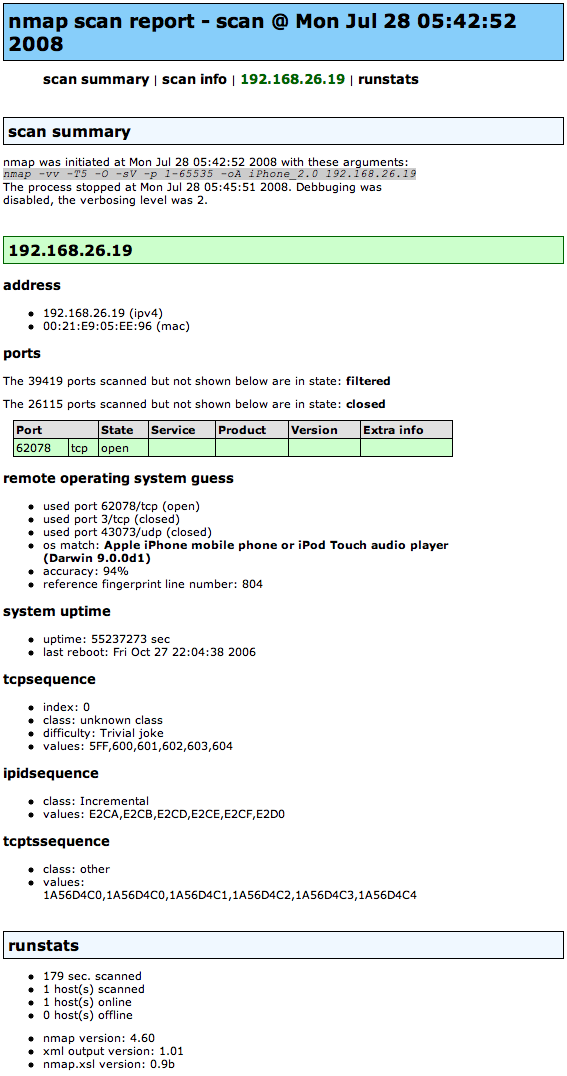
"So, nmap 4.60 is accurately identifying the iPhone 2.0 software as an “Apple iPhone mobile phone or iPod Touch audio player”. And that’s by using its single open TCP port — 62078. First, it’s reporting my last reboot as being Fri Oct 27 22:04:38 2006, which is highly incorrect. Even more interestingly, nmap is claiming that the sequence number prediction on the open port is weak (a trivial joke, as it were). That’s kind of 80’sish, so I didn’t believe it until I confirmed this via multiple connections to the port. Yep, definitely some weak ISN sauce. I’ll have to research what that service is later. Anyway, here’s the scan result."
With mobile phone providers dedicating special and sometimes too obvious netblocks for mobile users, default iPhone passwords assisting automated attacks through OpenSSH installed, next to the increasing number of customers jailbreaking and taking advantage of (insecure and misconfigured) third-party applications including those who would take advantage of tethering their iPhone's 3G connectivity for their laptops, the possibilities for building hit lists to use in remote code execution attacks through already identified devices is easier than it should be.