Petya ransomware: Free decryption tool released for the original versions of this nasty malware

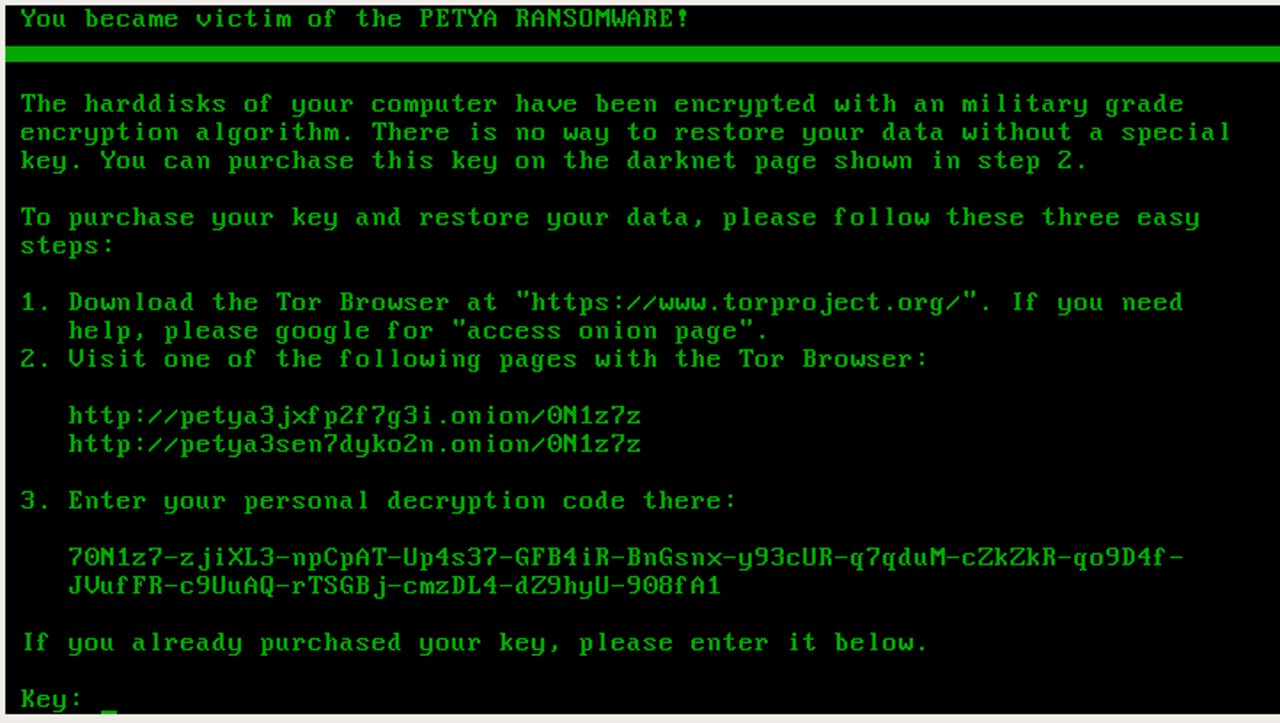
Victims of all 'legitimate' versions of Petya can decrypt their files for free.
Victims of several strains of the Petya ransomware may now be able unlock their files for free, thanks to the release of a new decryption tool for the malware family.
While the tool is capable of decrypting the standard versions of Petya, unfortunately for those infected by the Petya/NotPetya outbreak, it doesn't work for systems infected by the variant, which originated in Ukraine before spreading around the world.
Security
Even before a mutant version of Petya hit organisations across the globe, the ransomware had a reputation for being particularly nasty. Not only does Petya encrypt the victims' files using one of the most advanced cryptographic algorithms around, it also encrypts the entire hard drive by overwriting the master reboot record, in order to prevent the computer from loading the operating system.
But one version of the ransomware wasn't enough for its creators, who not only developed the original 'Red Petya', but also 'Green Petya' variants along with a golden-themed version named GoldenEye after the weapon in the 1995 James Bond film. The different versions display the Bitcoin demanding ransom note written in the colours the versions are named after.
Following the NotPetya outbreak, the author of the original version of the ransomware, Janus, released his master key and now cybersecurity researchers at Malwarebytes Labs have used the key to release a decryptor that can decrypt all legitimate versions of Red Petya, Green Petya, and GoldenEye and recover the lost files.
But the researchers warn that during tests it found that in some cases Petya may hang during decryption, or cause some other problems potentially damaging to data and said: "That's why, before any decryption attempts, we recommend you to make an additional backup."
Unfortunately, along with being able to do nothing for NotPetya victims, the Petya decryptor can't do anything for those hit by illegitimate versions of the ransomware such as PetrWrap.
Petya was one of the first types of ransomware to gain major success by spreading itself via a 'ransomware-as-a-as- service' scheme, whereby the author allowed budding hackers and cybercriminals to use the malicious code for their own ends -- in exchange for a cut of the profits.
The malware was equipped with measures to prevent unauthorised use of samples, but the group behind PetrWrap have managed to crack the Petya code and are using it to carry out their own attacks. The cryptography behind PetrWrap ransomware is so strong that there's currently no decryption tool which can crack it.
READ MORE ON CYBERCRIME
- Ransomware: An executive guide to one of the biggest menaces on the web
- The global ransomware epidemic is just getting started [CNET]
- Petya ransomware: Companies are still dealing with aftermath of global cyberattack
- 6 tips to avoid ransomware after Petya and WannaCry [TechRepublic]
- No more ransomware: How one website is stopping the crypto-locking crooks in their tracks