Ransomware attack may have a North Korean link, say security researchers

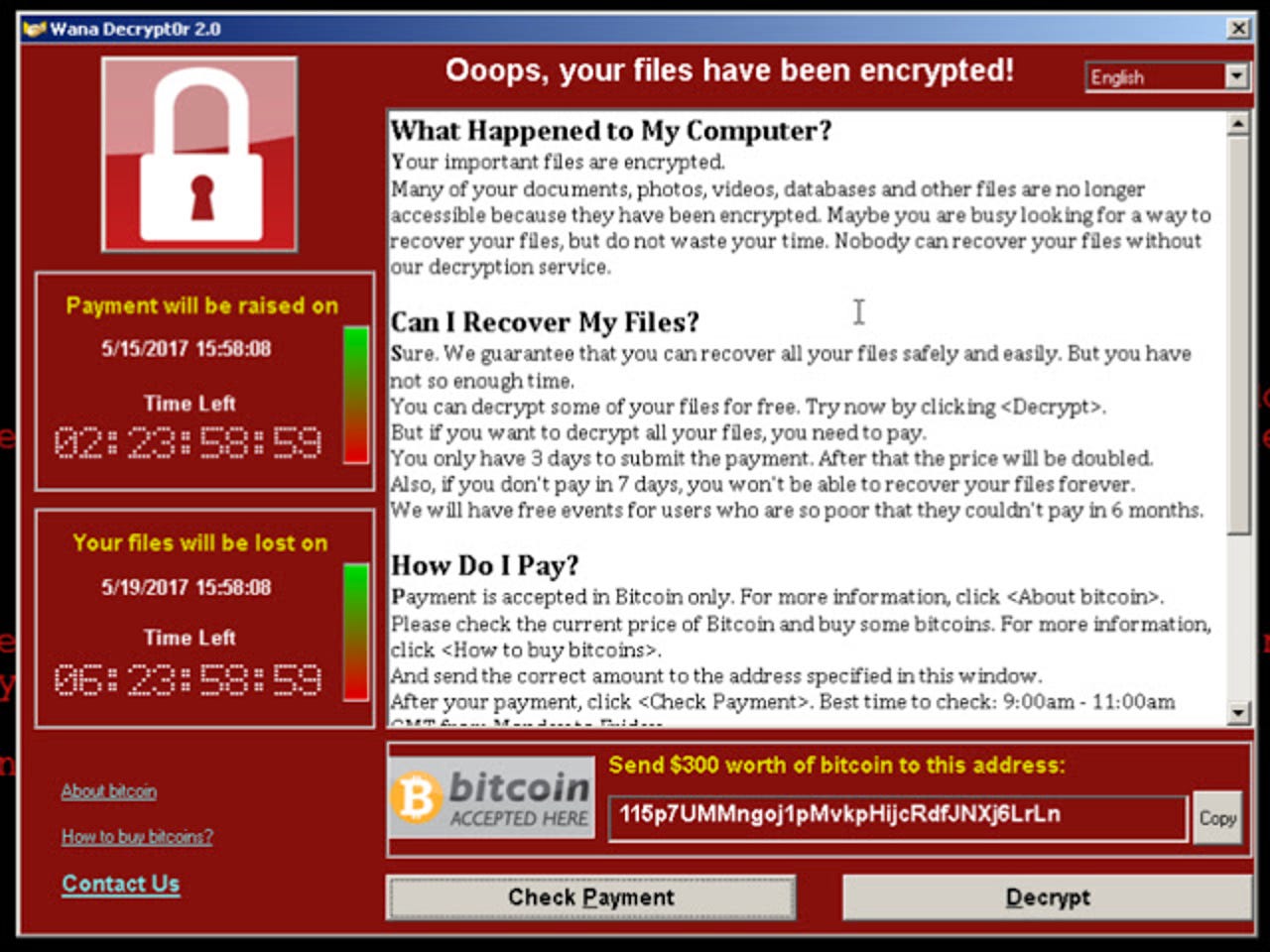
WannaCrypt/WannaCry ransomware has affected Windows XP systems across the globe.
The hunt is on to find the cyberattackers behind the massive ransomware campaign which has claimed more than 200,000 victims in over 150 countries, including the UK's National Health Service, and businesses and government institutions in Russia, China, and the US.
Law enforcement agencies across the world are collaborating on an effort to identify those behind WannaCry, but are unwilling to speculate on the identities of any perpetrators at this time.
Cybersecurity researchers, however, have tentatively linked the WannaCry ransomware campaign to the Lazarus group, a hacking operation which is believed to have links to North Korea.
A well-resourced operation, the Lazarus group has been connected to a number of high-profile cyberattacks in recent years. They include the $80m Bangladeshi cyber bank heist, as well as attacks against financial institutions, banks, casinos, and systems used by software developers for investment companies around the world.
It's thought that the group might also have been behind the 2014 Sony Pictures hack, which supposedly was carried out in response to a comedy film about North Korea, although Pyongyang has never admitted any involvement.
Speculation that Lazarus might be in involved with the recent Wannacry outbreak started when Google researcher Neel Mehta posted a mysterious string of characters in a tweet alongside the hashtag #WannaCryptAttribution'.
The string is two samples of code which share similarities: one is from a WannaCry encryptor example from February this year, and the other is a Lazarus APT group sample from February 2015.
Cybersecurity researchers at Kaspersky have posted an image of the code comparison in a blog post and suggest that the two pieces of code share a common author.
Comparison of the code behind Lazarus and WannaCry
"We strongly believe the February 2017 sample was compiled by the same people, or by people with access to the same sourcecode as the May 2017 Wannacry encryptor used in the May 11th wave of attacks," said Kaspersky researchers, adding how Mehta's discovery "is the most significant clue to date regarding the origins of Wannacry".
Researchers at Symantec have also noted similarities in the shared code between known Lazarus tools and the WannaCry ransomware, noting the SSL implementation uses a specific sequence of 75 ciphers which to date have only been seen in Lazarus and WannaCry malicious software.
While these links don't definitively prove anything, Symantec researchers said: "We believe that there are sufficient connections to warrant further investigation."
Kaspersky researchers added that "in theory anything is possible". For example, the code might have somehow been stolen or copied from the Lazarus group. Nonetheless, they say the idea of this being a false flag -- that is, an attempt to trick investigators -- is "although possible, improbable".
When machines become infected by Wannacry ransomware, their users are issued with a ransom of $300 in Bitcoin for unencrypting their files. That doubles to $600 if the demand isn't met within three days, and if a week goes by without payment, the victims are threatened with permanent deletion of their files.
However, while over 200,000 victims were infected by the ransomware worm, just 233 ransoms totalling $64,472 had been paid as of Tuesday morning, according to a Twitter bot monitoring the bitcoin wallets tied to WannaCry.
MORE WANNACRY RANSOMWARE NEWS
- WannaCrypt ransomware: Microsoft issues emergency patch for Windows XP
- Ransomware attack: The second wave is coming, so get ready now
- How to defend yourself against the WannaCrypt global ransomware attack
- Ransomware: An executive guide to one of the biggest menaces on the web
- Ransomware attack: Amidst the chaos, the blame game begins