Remote-controlled Android malware stealing banking credentials

Security researchers at McAfee have discovered a malicious Android application capable of grabbing banking passwords from a mobile device without infecting the user's computer.
The latest piece of Android Malware, dubbed FakeToken, contains man-in-the-middle functionality to hijack two-factor authentication tokens and can be remotely controlled to grab the initial banking password directly from the infected mobile device.
[ SEE: Ten little things to secure your online presence ]
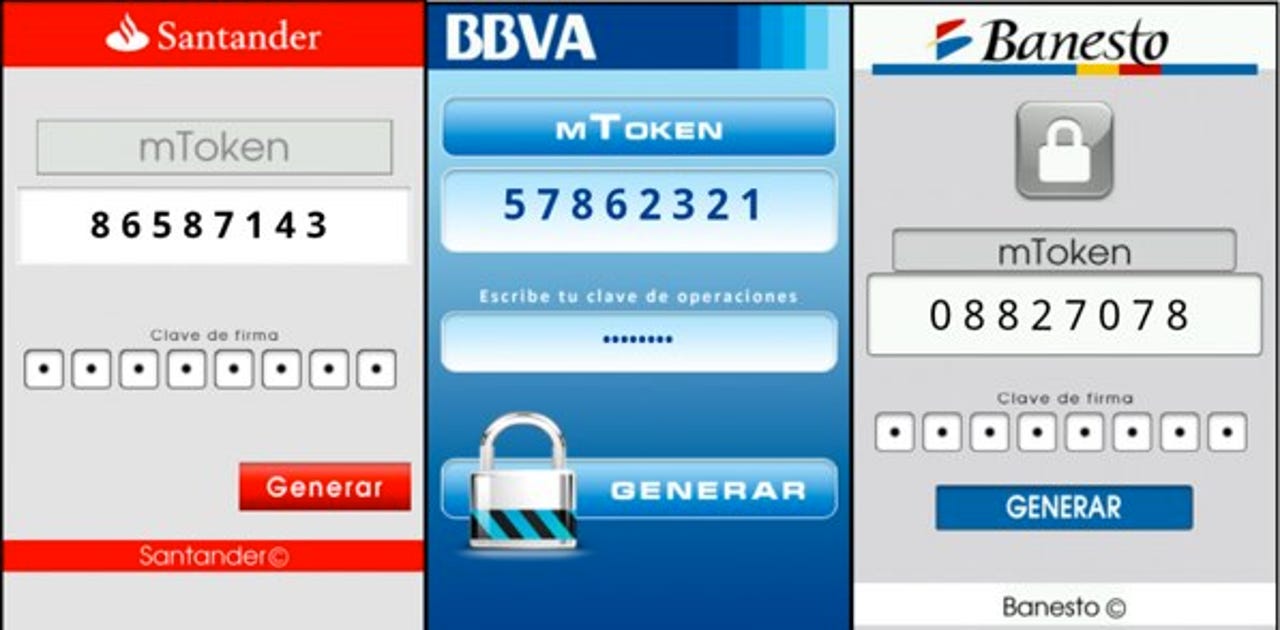
McAfee's Carlos Castillo explains:The malicious application targets specific well-known financial entities posing as a Token Generator application. In fact, when the application is installed, the malware uses the logo and colors of the bank in the icon of the application, making it appear more credible to the user:
When the application executes, it shows a WebView component that displays an HTML/JavaScript web page that pretends to be a Token Generator. The web page also appears to be from the targeted bank (same variant of the malware but with different payload).
To get the fake token, Castillo discovered that the user must enter the first factor of authentication (used to obtain initial access to the banking account). If this action is not performed, the application shows an error.
"When the user clicks “Generar” (Generate), the malware shows the fake token (which is in fact a random number) and sends the password to a specific cell phone number along with the device identifiers (IMEI and IMSI). The same information is also sent to one of the control servers along with further data such as the phone number of the device. The malware finds the list of control servers from an XML file inside the original APK," he added.
He said the malware also contains commands to update itself or spy on the infected machine.
Castillo found that the FakeToken app can also hijack the list of contacts stored in the device (name and number)
Android malware that targets financial entities is in constant evolution: From man-in-the-middle attacks we now see more sophisticated, remote-controlled banking Trojans that can get more than one factor of authentication and update itself to, for example, modify a phishing attack to get other required credentials–such as the name or the ID number of the user–to perform electronic fraud. Due to the increasing popularity of Android and mobile-banking applications, we expect that more threats like this will appear.