Samsung connected home fridge becomes weapon in MITM attacks

[Update 13.54 GMT with Samsung statement]
Researchers have uncovered security flaws in Samsung's IoT smart fridge which can be exploited to run man-in-the-middle (MITM) attacks.
At the cybersecurity conference Def Con 23 in Las Vegas, the IoT village conducted a day of hacking activities which included penetration testing the Samsung RF28HMELBSR smart fridge. Researchers scrutinized the $3,599 Internet-connected fridge --which features an 8" Wi-Fi enabled LCD for web browsing and app access -- and discovered security holes which could place users at risk.
Hackers taking on the challenge of the fridge found that while the connected home device implements SSL, the fridge fails to validate SSL certificates -- which in turn gives attackers the opportunity to conduct man-in-the-middle (MITM) attacks.
MITM attacks are possible when a security weakness allows an attacker to spy upon a supposedly secure communications channel which may contain valuable data such as credentials and financial information, leading to data theft.
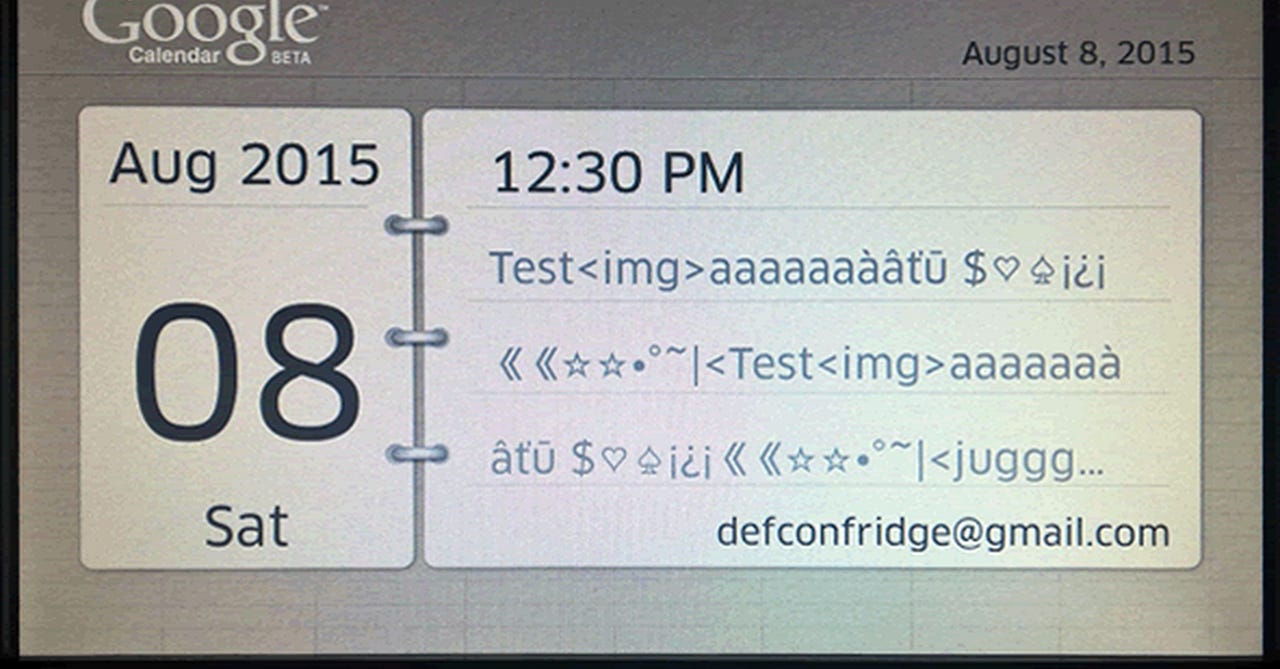
During testing, the researchers found MITM attacks could be launched against "most" connections thanks to the exploited flaw. The connections include those made to Google servers when accessing Gmail calendar information on the smart fridge's display.
Therefore, if an attacker is next door or on the road outside, they would theoretically be close enough to steal credentials belonging to the owner, which are often the keys to the kingdom of Google service users.
However, there is at least one exception to the rule. When the fridge terminal connected to the update server, the URL could be isolated and certificates produced containing based on this data -- but while the certificates contained exactly the same data as those on the legitimate website, validation proved strong.
Featured
"The terminal must have a copy of the CA and is making sure that the server's cert is signed against that one," the researchers said.
"We can't hack this without access to the file system where we could replace the CA it is validating against. Long story short we couldn't intercept communications between the fridge terminal and the update server."
The team also contemplated faking a firmware update to compromise a unit. If a fraudulent firmware update is issued, this can be used to plug malicious code into a device -- potentially resulting in an MITM foothold and surveillance. While not impossible in the case of Samsung's smart fridge, an attacker would need to guess a number of parameters, including model code names and serial numbers, to issue such an attack.
The IoT village researchers also planned to explore physical access attacks on the model, but unfortunately ran out of time. The findings, however, remain interesting as they do highlight how many new ports and avenues we are adding to our lives which may compromise our personal security and privacy.
A connected home, full of network-controllable devices including lights, fridges and home security systems can make our lives more convenient and efficient, but it is the responsibility of both vendor and user to keep these devices safe from attack.
A Samsung spokesman told ZDNet:
"At Samsung, we understand that our success depends on consumers' trust in us, our products, and the services we provide. As soon as this potential vulnerability was identified, we promptly took action to investigate and resolved the issue by deploying a software update on August 25, 2015.
The refrigerator connected to the network will commence the software update automatically. If disconnected, the update will commence once network connection is restored. Protecting our consumers' privacy is our top priority, and we work hard every day to safeguard our valued Samsung users."
10 steps to erase your digital footprint
Read on: Top picks
- How to access Wi-Fi anonymously from miles away
- Apple OS X zero-day flaw hands over root access without system passwords
- Getting physical: A $10 device to clone RFID access keys on the go
- Amazon dreams of drones-only airspace
- Strike the source: RIAA targets BitTorrent protocol to block pirate content
- Three top tips to keep connected cars safe from hackers
In pictures: