Security consortium emerges to fight WireX botnet on Android

Researchers from Akamai, Cloudflare, Flashpoint, Google, Oracle Dyn, RiskIQ, Team Cymru, and others joined forces to combat WireX, a botnet found targeting content delivery networks (CDNs) and content providers.
WireX comprises primarily Android devices running malicious applications and is designed to create DDoS traffic, a blog post compiled by the research consortium explains.
According to the post, Google found the malware available on its Play Store a few days ago and removed the hundreds of affected applications and started the process to remove the applications from all devices.
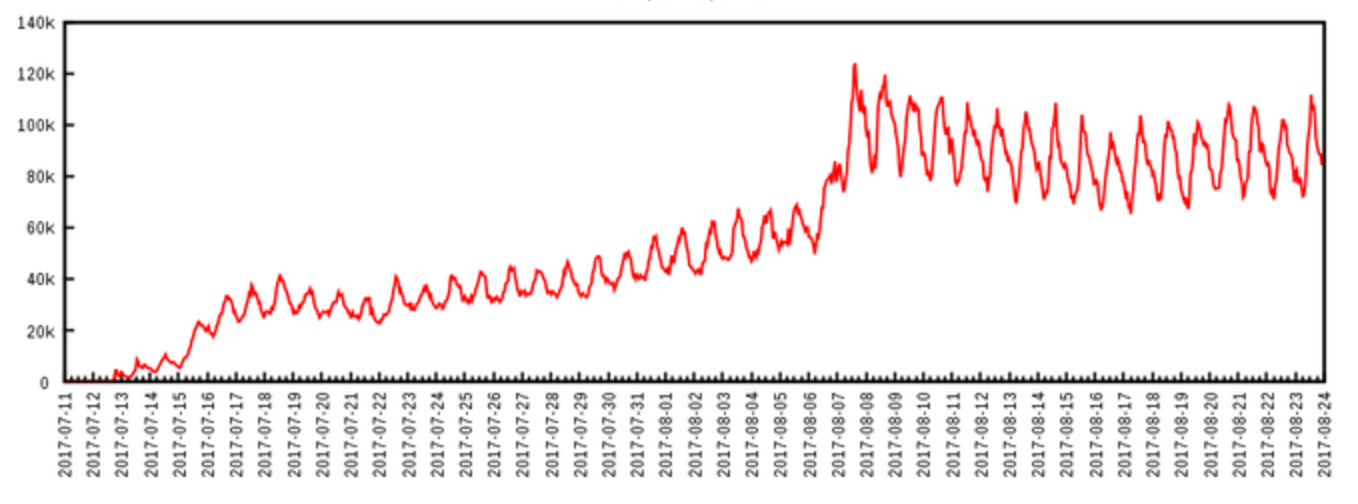
The research group believes WireX may have been active as early as August 2, but said it was the attacks on August 17 against the CDNs and content providers that drew attention.
The August 2 attacks were flagged as minor, as they were unnoticed until researchers began searching for the 26-character User-Agent string in logs, the blog explains.
"These initial attacks were minimal and suggest that the malware was in development or in the early stages of deployment," it continued.
WireX botnet unique IP addresses per hour
More prolonged attacks starting on August 15 were identified, with some events sourced from a minimum of 70,000 concurrent IP addresses. After analysis, it was found that devices from more than 100 countries participated in the August 17 attack, an uncharacteristic event, according to the research group.
WireX is a volumetric DDoS attack at the application layer.
The traffic generated by the attack nodes is primarily HTTP GET requests, though some variants appear to be capable of issuing POST requests, the researchers explained.
"In other words, the botnet produces traffic resembling valid requests from generic HTTP clients and web browsers," the post explains, noting the botnet is named for an anagram for one of the delimiter strings in its command and control protocol.
The initial researchers reached out to peers in other organisations for verification of what they were seeing. Once more eyes were on the investigation, starting with the investigation of historic log information, the blog said it revealed a connection between the attacking IPs and something malicious, possibly running on top of the Android operating system.
"We identified approximately 300 apps associated with the issue, blocked them from the Play Store, and we're in the process of removing them from all affected devices," Google is quoted as telling the research group.
Many of the identified apps fell into the categories of media players, ringtones, or tools such as storage managers and app stores with additional hidden features that were not readily apparent to the end users that were infected, the blog explains.
"At the launch of the applications, the nefarious components begin their work by starting the command and control polling service which queries the command and control server, most commonly g.axclick.store, for attack commands. When attack commands are received, the parsing service inspects the raw attack command, parses it, and invokes the attacking service with the extracted parameters," the researchers said.
"It is likely that this malware used to be related to click fraud, but was repurposed for DDoS."
In the wake of the Mirai attacks, the researchers said information-sharing groups such as the one formed to combat WireX have seen a resurgence in hope of solving internet-wide problems.
In the aftermath the global spread of WannaCry ransomware, and the subsequent Petya outbreak, cybercriminals appear to be putting a lot of effort into developing particularly vicious strains of ransomware. However, the research group said it has only strengthened the value of collaboration.
"This research is exciting because it's a case study in just how effective collaboration across the industry is," said Allison Nixon, director of Security Research at Flashpoint. "This was more than just a malware analysis report. The working group was able to connect the dots from the victim to the attacker. The group also used the information to better mitigate the attack and dismantle the botnet -- and this was completed very quickly.
"A botnet of this extreme size is concerning for the sake of the internet as a whole."