Stupid passwords, irritating UAC & what spam you get


The latest release of Microsoft's comprehensive Security Intelligence Report has some fascinating nuggets in, among the hundreds of pages of vulnerability, malware and threat trends.
Anyone who’s responsible for even a single server needs to take the section on Conficker to heart. Despite the fact that there hasn't been a new version of Conficker in years, and that the exploits in SVCHOST.EXE were long since patched, why is a worm from 2009 still one of the main threats in enterprises? Because they haven't bothered to enforce strong passwords. Conficker looks for passwords like using passwords like “admin”, “admin123”, “administrator”, “default”, “test”, “12345” and (perhaps the saddest one) “security” - and in far too many cases it finds them. Got an admin password? Go change it to something that will actually protect you. Do it now; we’ll wait.
The vulnerabilities you most need to worry about, because there are so many of them, are attacks on HTML, JavaScript and Adobe Reader. Worry about users pirating software as well; the most common family of malware in Q4 of 2001 and the only common family of malware that got more common as the year went on is Keygen; infected tools that generate keys for pirate software. That 'free' copy of Photoshop comes with an unexpected bonus infection.
One set of figures caught my eye in the report; infection rates for different versions of Windows. The figures for malware removed from PC using the MSRT tool is higher for Windows Vista than it is for Windows XP (the figures are normalised so the sales figures aren't relevant.

This seemed odd, as Vista was a more secure OS than XP. Certainly XP SP3 added a lot of security improvements; by the end, XP was a pretty robust OS, but by SP3 Windows 7 was ready to test (and it continues to have fewer infections than any other Microsoft OS except Windows Server 2008 R2, where the option of Server Core means far fewer vulnerabilities because there's less code running). So why is Windows Vista getting infected more? Microsoft suggests it's because malware writers are targeting newer systems as XP finally slips away into the sunset, especially 64-bit systems, and that XP was disproportionately protected by turning off the Autorun feature - but that was a vulnerability in Vista as well.
My suspicion is that Vista users are falling to attacks targeted at Windows 7 users that they're not as well protected against. Once reason they're not as protected, and the real reason I think Vista has more infections than XP, is that the User Account Control protection in Vista is really pretty annoying if you install enough software to be vulnerable to installing malware. It was designed to shift you to running as a limited user by getting you to complain to the developers of software that insisted you run it as admin, so it had to be annoying. It wasn't designed as a firm security barrier, but it does offer protection; but it's annoying enough that many users just turn it off.
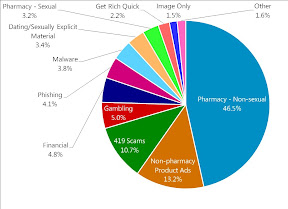
The other surprise is that most spam isn't want you think it is. Forget all those Viagra adverts; it's standard pharmacy ads that fill up your inbox and junk folder (the kind Google got fined a swingeing amount for helping pharmacies outside the US put in search results). Unexpected inheritances and phishing messages and fake gambling sites are a mere fraction of the total compared to messages offering you hair restorer and cheap prescriptions. I guess that’s probably a sign that spam is mainstream.
Mary Branscombe