Sunbelt Software: Google search results delivering massive malware attacks

For the last two days, security software firm Sunbelt Software has been all over what could develop into a scary trend: Rigged Google search results that deliver big malware payloads.
On Monday, Sunbelt reported "we’re seeing a large amount of seeded search results which lead to malware sites." The search terms leading you to these malware payloads were pretty basic fare.
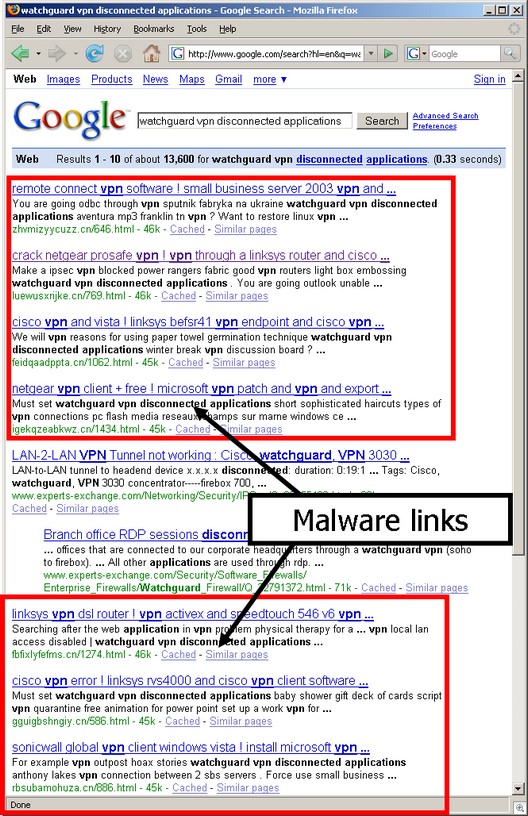
This screenshot courtesy of Sunbelt shows an example of the malware sites (Sunbelt's post has a bunch of other examples).
On Tuesday, Sunbelt researcher Adam Thomas followed up with another post. Thomas wrote:
Sunbelt Software has uncovered tens of thousands of individual pages that have been meticulously created with the goal of obtaining high search engine ranking. Just about any search term you can think of can be found in these pages.
Simply put, damn near any Google search term--even terms like "hospice"-- can take you to one of these malware sites. Computerworld quotes Sunbelt Software CEO Alex Eckelberry as saying "this is huge." I'm inclined to agree, especially considering Eckelberry's inventory: "27 different domains, each with up to 1,499 [malicious] pages. That's 40,000 possible pages."
Thomas continues:
For months now, our Research Team has monitored a network of bots whose sole purpose is to post spam links and relevant keywords into online forms (typically comment forms and bulletin board forums). This network, combined with thousands of pages such as the two seen above, have given the attackers very good (if not top) search engine position for various search terms.
In our previous post, we mentioned that the malicious pages also contained an IFRAME link which would attempt to exploit vulnerable systems. If you were unlucky enough to run across one of these links while surfing with a vulnerable system, you would become infected with a family of malware that we call Scam.Iwin. With Scam.Iwin, the victim's computer is used to generate income for the attacker in a pay-per-click affiliate program by transmitting false clicks to the attacker's URLs without the user's knowledge. The infected Scam.Iwin files are not ordinarily visible to the user. The files are executed and run silently in the background when the user starts the computer and/or connects to the internet.
Google has been notified and hopefully its fancy algorithm can nuke these bogus sites pronto.
Ryan Naraine is on vacation.