Super-expensive ransomware linked to online cybercrime market, say security researchers

Jaff ransonware is linked to an online marketplace selling stolen accounts.
A fast growing form of ransomware has been linked to a much wider cybercrime operation which deals in stolen bank details and hacked accounts from online stores including PayPal, eBay and Amazon and more.
Jaff ransomware sprung to life last month, indiscriminately targeting millions in its first few hours with malicious PDF attachments sent via phishing emails. Victims are extorted for a particularly high ransom of 1.79 Bitcoins - currently $4,613 - in order to regain access to their files.
The ransomware shares similarities with the notorious Locky family and like Locky, is distributed by the Necurs botnet, leading researchers to believe there's a link between the two campaigns.
But it now appears that may be just one element of the operation behind Jaff, which allegedly shares links with a large cybercriminal web store.
Working alongside CSIS Security Group, researchers at Heimdal Security have discovered that Jaff ransomware shares server space with an online marketplace which provides access to tens of thousands of compromised bank accounts and details of the victim they belong to, including location, balance and email address.
The web store also claims to provides cybercriminals will access to hacked online shopping accounts - including 1.8 million compromised PayPal accounts - with prices per stolen item ranging from under a dollar to several Bitcoins.
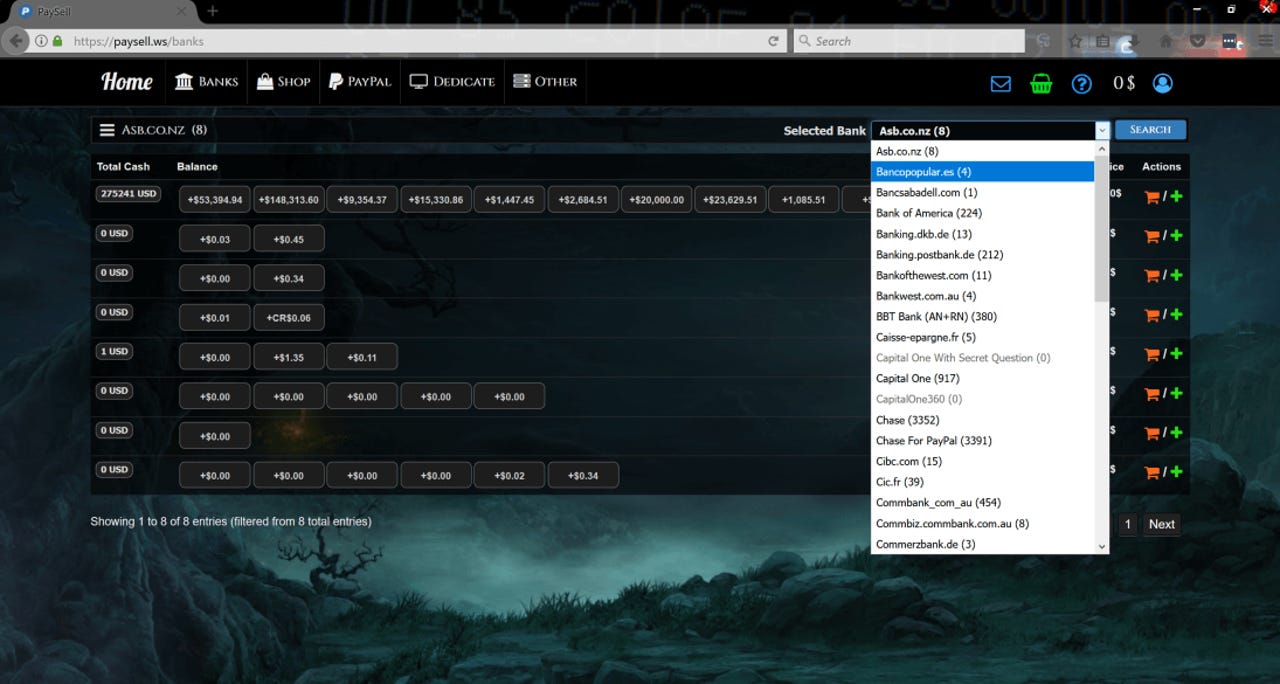
Bank details available for sale in the Paysell store
The store doesn't include any sort of vetting process for new users, meaning that even the lowest level wannabe cybercriminal can gain access to stolen credentials and finances, as well as the ability to make purchases through comprised accounts.
However, the store also provides filters for more ambitious buyers, listing which accounts have the most lucrative potential, including details of accounts at one New Zealand bank totaling over $275,000.
Banks from all over the world are listed as for sale, with the highest volumes of compromised records originating from the US, Germany, France, Spain, Canada, Australia, Italy and New Zealand.
The banks and online shopping websites themselves are unlikely to have been compromised, but rather hackers have stolen accounts via breaking weak or reused passwords. It's also possible that users have been duped by phishing campaigns.
Researchers say the server used to host the store is hosted in St Petersburg, Russia and that the same server serves as part of the infrastructure used to carry out Jaff ransomware attacks - and that it's just one way in which the two malicious services overlap.
Given that Jaff is distributed by the Necurs botnet, it perhaps isn't a big surprise to find the ransomware is linked to a cybercriminal forum dealing in stolen financial data. Necurs has previously been associated with distributing of large-scale data-stealing banking Trojan campaigns such as Dridex.
Ransomware has become one of the biggest menaces on the web. A ZDNet guide contains everything you need to know about it: how it started, why it's booming, how to protect against it, and what to do if your PC suffers an attack.
READ MORE ON CYBERCRIME
- Ransomware: WannaCry was basic, next time could be much worse
- Dark Web: The smart person's guide [TechRepublic]
- Ransomware: An executive guide to one of the biggest menaces on the web
- Your identity is sold for $1 in the Dark Web [CNET]
- Easy to carry out, difficult to fight against: Why ransomware is booming