Tech support scams evolve, borrow tricks from ransomware creators

Ransomware continues to evolve and it is becoming more and more of a challenge for the general public to stay shielded from such threats and security experts to stay on top of the evolving strains of ransomware being found in the wild.
Security
It is not just the malicious code itself, however, which is a problem. Now, support scammers are taking tips from ransomware developers to make their own fraudulent schemes more sophisticated and successful.
Ransomware is a particularly virulent type of malicious code which, once installed and executed on a vulnerable system, encrypts the contents of a PC and demands payment -- usually in Bitcoin -- in exchange for a key to decrypt files and return access to a victim.
Countless ransomware families such as CoinVault, TeslaCrypt, and Petya generate a fortune in fraudulent revenue for operators every year, who not only target the average consumer, but also businesses, hospitals, and transport networks without thought.
In the past, tech support scams have often taken the form of simple cold calls and malware-based fake alerts which attempt to frighten PC users into thinking their PC needs a "cleaning" from companies such as Microsoft. More recently, screen lockers have also emerged.
Tech support scams have now gone a step further and have taken a page out of the ransomware book in a new effort to frighten users into paying up for a fake service, according to researchers from Malwarebytes.
See also: Remove ransomware infections from your PC using these free tools
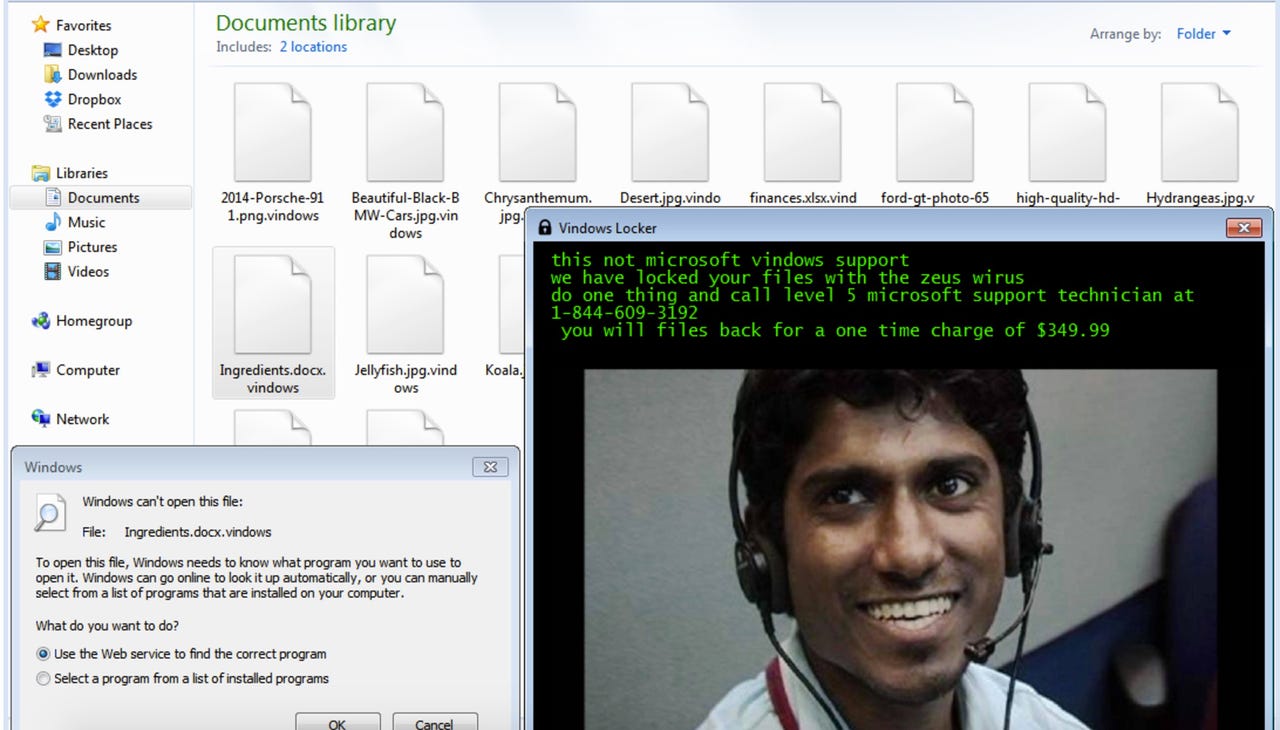
The new twist was discovered after tracking the "Vindows Locker" ransomware which appears to be true ransomware that encrypts your files. However, the standard blackmail note -- which often portrays the malware as a government agent, law enforcement agency, or similar group -- demands a $349 ransom not in Bitcoin, but as a payment made to a supposed Microsoft technician.
A number is displayed on the ransom note which if called leads to a team of Indian support scammers, who promise to decrypt your files in return for the fee. However, pay up or not, those files are not going to be decrypted by them.
There is little that is particularly interesting about Vindows Locker. The malware is written in C#, mildly obfuscated, files are encrypted with AES and the malware adds the .vindows extension to each file.
However, the malicious code does contain one unusual element; the abuse of Pastebin's API to establish communication between the ransomware and the operator's command-and-control (C&C) center.
The malware is not sophisticated and neither do the creators appear to be. Mistakes made in how cryptography has been applied to lock files has allowed the Malwarebytes team to create a decryptor for victims.
As always, you should never pay up if you are infected with ransomware; there is no guarantee you will be able to rescue your content and doing so only encourages this trend to continue.