This bank data stealing Android malware is back - and it's now even sneakier

An Android banking trojan managed to infiltrate Google's official Play Store a second time potentially infect thousands with financial data stealing malware before it was kicked out again.
The Bankbot malware first appeared in the Google Play store earlier this year, stealing victims banking information by presenting an overlay which looked identical to a bank's app login page. The malicious apps were removed in April, but Bankbot was once again discovered in the Play Store in early September.
Uncovered by researchers at ESET, this time, the malware came hidden inside a functioning Android game called 'Jewels Star Classic'. The app first appeared in the store on 26 August before an update on 4 September raised the alarm. By the time the app was removed from the store on 7 September, it could have been downloaded 5,000 times.
This version of BankBot is more sophisticated than its predecessor, adding improved code obfuscation, a more sophisticated payload dropping functionality and exploits Android's Accessibility Service in a similar way to other forms of mobile banking malware.
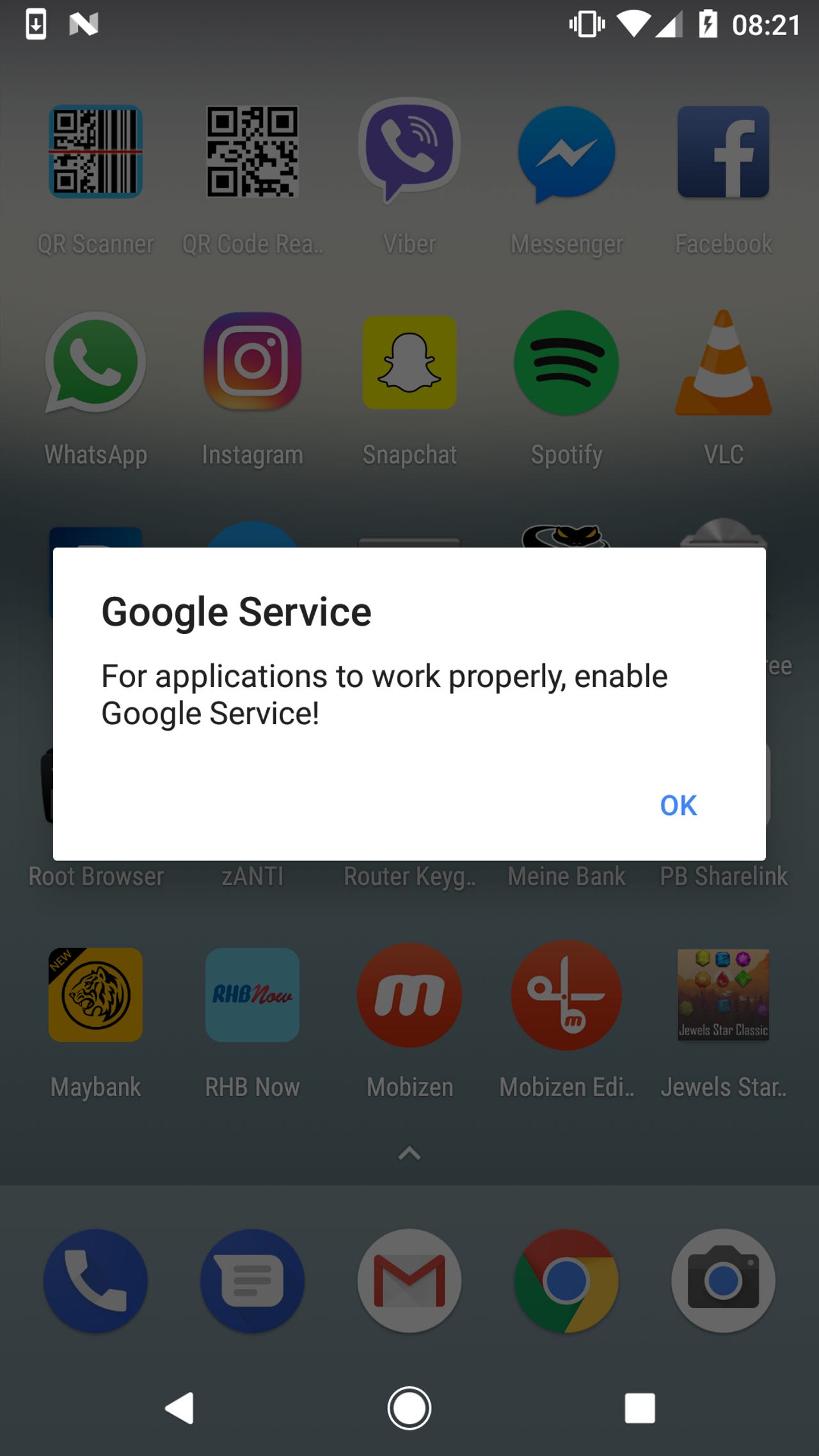
The fake alert prompting users to enable 'Google Service'
After being downloaded, the malicious app waits until 20 minutes after the first time the game is played before running the programme to install the BankBot trojan. It's possible that this delay is one of the factors which helped the app infiltrate the Google Play Store in the first place.
Following the 20 minute delay - and no matter which app they're using at the time time - the victim is presented with an alert to enable "Google Service".
When the user activates this fake Google push notification, they're asked to grant various permissions to the malicious app, including the ability to Observe user actions, Retrieve window content, Turn on Explore by Touch, Turn on enhanced web accessibility and Perform gestures.
By giving the app permission, they're giving BankBot a free pass to monitor their activity and eventually steal their bank details. In the meantime, the malware pretends to run a service update as it makes its next steps towards running the trojan and stealing banking data.
See also: Can Google win its battle with Android malware?
Indeed, while this fake update is running, the malware is in fact using its newly granted permissions to allow the installation of apps from unknown sources, install BankBot and launch it, activate BankBot as the device administrator, set BankBot as the default SMS messaging app and obtain permission over other apps.
With all of this in place, BankBot is able to steal the victim's credit card details - and in a much more streamlined fashion when compared with previous versions of the malware. Previously the malware came with a list of banking applications it attempted to mimic, but now it only pretends to be Google Play - an app pre-installed on every Android device,
When the user next loads Google Play, they're presented with a screen asking for their credit card number. This fake overlay hands puts their details straight into the hands of hackers who can use BankBot's control over messaging to bypass SMS-based two-factor authentication on the victim's bank account.
While this particular malicious app has been removed from the the Play Store, Google is in an ongoing battle with cyber criminals attempting to use the official Android marketplace to distribute malware.
Google keeps the vast majority of its 1.4 billion Android users safe from malware, but malicious apps still sneak through to the official store.
In order to protect against installing malicious apps, ESET researchers recommend users check the popularity of the app, it's ratings and reviews in order to ensure the download is really what it purports to be.
READ MORE ON CYBER CRIME
- Android app stores flooded with 1,000 spyware apps
- This is the easiest way to prevent malware on your Android device [CNET]
- Android malware in Google Play racked up 4.2M downloads: Are you a victim?
- This scary Android malware can record audio, video and steal your data
- Android malware bypassed Google Play store security, could have infected 4.2 million devices [TechRepublic]