Thousands of legitimate sites SQL injected to serve IE exploit
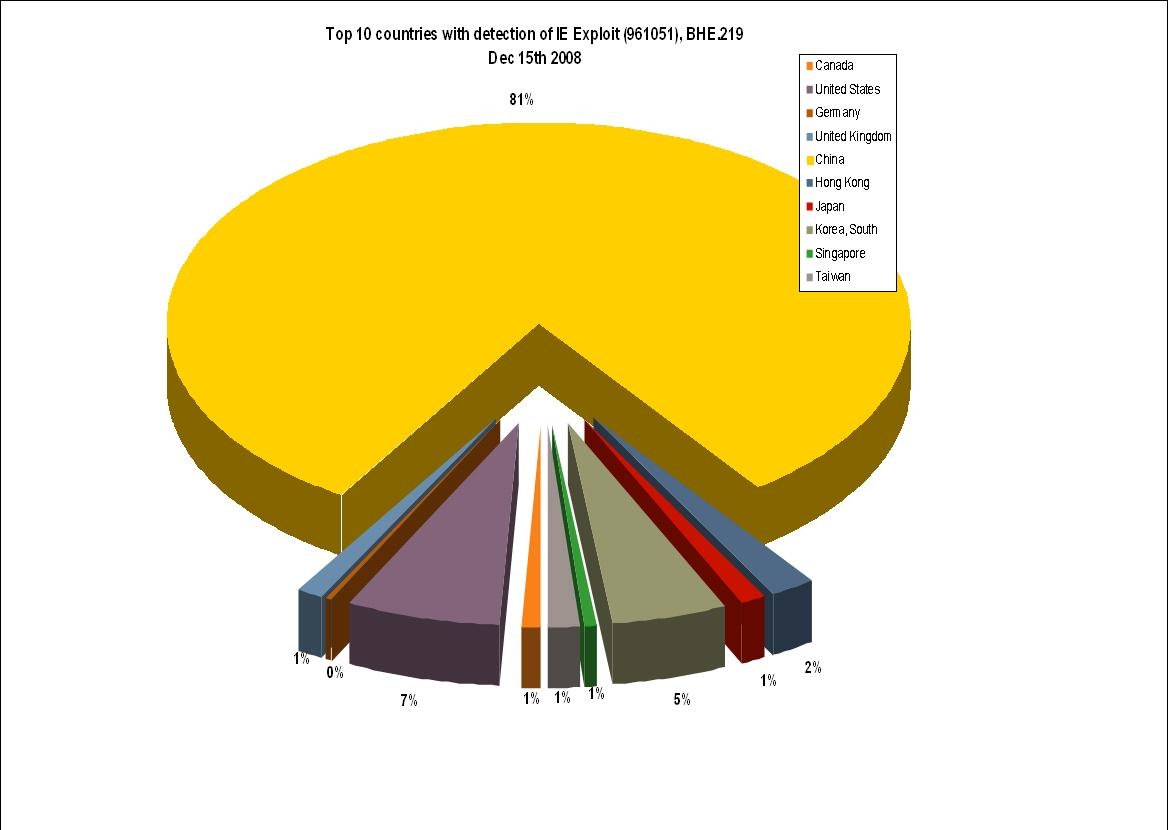
The SQL injection attacks serving the just patched Internet Explorer XML parsing exploit, are launched by several different Chinese hacking groups, and with several exceptions, are primarily targeting Asian countries which is a pretty logical move given the fact that it's a password stealing malware for online games that is served at the bottom line.
Which is the most targeted country?
According to some stats from Symantec, China ironically remains the most actively targeted country by the IE exploit, ironically in the sense that it was Chinese researchers that leaked the exploit at the first place. Moreover, the 100,000 web sites cited as being infected by Symantec, should be taken as a very conservative metric, since more domains are being injected and as previous campaigns, the number of affected sites could change pretty fast.
Recent studies continue emphasizing on the fact that millions of users not only continue browsing the web using insecure browsers, but also, are so browser vulnerabilities centered and they ignore the rest of the software running on their PCs as a potential infection vector given they're running an insecure versions of it - and yes they are. Cybercriminals are aware of this insecure Internet browsing, and are therefore including sets of exploits targeting each and every version known to be vulnerable of a particular software in order to increase the chances for a successful infection. This particular SQL injection attack is the most recent example of this mentality.
In 2008, cybercriminals continue infecting thousands of new hosts on daily basis using 2007's critical vulnerabilities, because instead of patching vulnerable software, the majority of end users remain comfortable with their false feeling of security.