Tracking down the Storm Worm malware
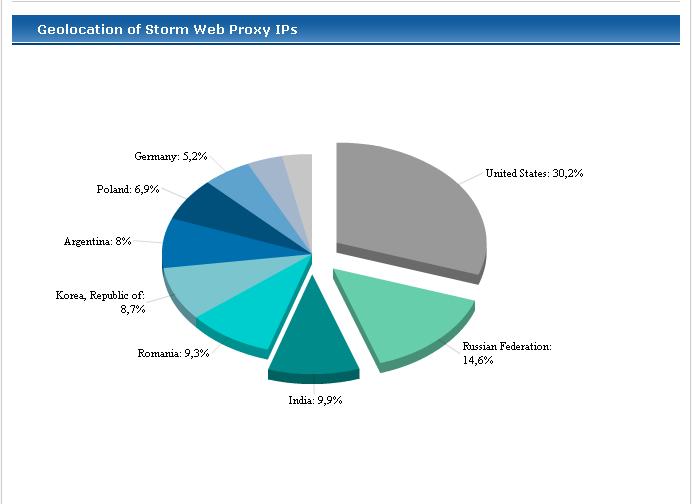
What is the current state of Storm Worm activity, how many infected IPs are found to host the malware on a daily basis, which are the latest domains used by the Storm Worm, and which countries have the largest infected population? You can easily find that out, if you keep an eye on TrustedSource's Storm Tracker, a handy tool providing both, researchers and end users with a real-time overview of the current Storm Worm activity, of course, based on a single vendor's sensor network as a sample of malicious activity. What are some of the categories monitored by the service?
TrustedSource's Storm Tracker monitors the following categories :
- Daily New Web Proxy IPs - Most Active Storm Web Proxy IPs - Top Storm Domains - Newly Activated Storm Web Proxy IPs - Recently Seen Storm Web Proxy IPs - Geolocation of Storm Web Proxy IPs
After taking credit for the pioneering of P2P botnet command and control, next to the rest of commonly used botnet communication platforms, as well as the fast-fluxed botnet structure in order to create a dynamic and harder to shut down botnet, Storm Worm is currently in the orienting process if we're to consider the OODA loop. What does this mean? It means that, for instance, once observing the success rate of the recent SQL injection attacks, the botnet masters decided to enjoy all the noise generated by the copycats, reintroduce the same tactic that they were using in August, 2007, and started injecting their exploit serving domains into vulnerable sites hoping they would go unnoticed in between the rest of the currently active SQL injection campaigns.
Considering Storm Worm's historical pattern of utilizing event-based social-engineering campaigns, and periods of passive behaviour, once the botnet masters orient and decide, they'll act again for sure. It's always calm before the real storm, especially in times when multiple storms are fighting for market share, isn't it?