'Trojanised' Steamy Window targets Android phones

Symantec has identified a botnet-building Android Trojan that hackers can use to send out text messages from a compromised smartphone.
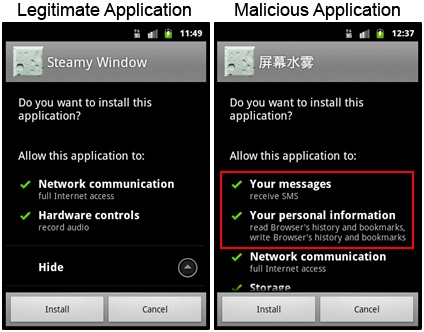
Symantec has identified a Trojan that piggybacks on versions of a legitimate app called Steamy Windows, and asks users for excessive permissions. Photo credit: Symantec
The Trojan, which Symantec has named Android.Pjapps, piggybacks on versions of a legitimate phone app called Steamy Window that are available on unregulated mobile app marketplaces. Once a malicious version is downloaded to a phone, it sends the subscriber ID, line number and other personal information to hackers and communicates with the hacker's server to receive instructions.
"The aim of Android.Pjapps is to build a botnet controlled by a number of different Command and Control (C&C) servers," Symantec said in a blog post on Monday. "Among other things, it is able to install applications, navigate to websites, add bookmarks to your browser, send text messages, and optionally block text message responses."
Steamy Window overlays a 'steamed-up' effect on a phone screen. People can distinguish between the legitimate software and the compromised versions by checking the permissions required when installing the app. On installation, malicious versions ask for excessive permissions, including access to messages and personal information, Symantec said.
The app is one of a growing number of programs that have been 'Trojanised' to target Android users and put up for download on third-party Android apps sites, the security company added. Other malicious programs that open a backdoor on Android devices include Android.Geinimi.
Both Android.Pjapps and Android.Geinimi are classified as a low risk by Symantec, as the number of infections and geographical distribution is low in each case, while threat containment and removal is classified as easy.
Get the latest technology news and analysis, blogs and reviews delivered directly to your inbox with ZDNet UK's newsletters.