WannaCry ransomware attack at LG Electronics takes systems offline

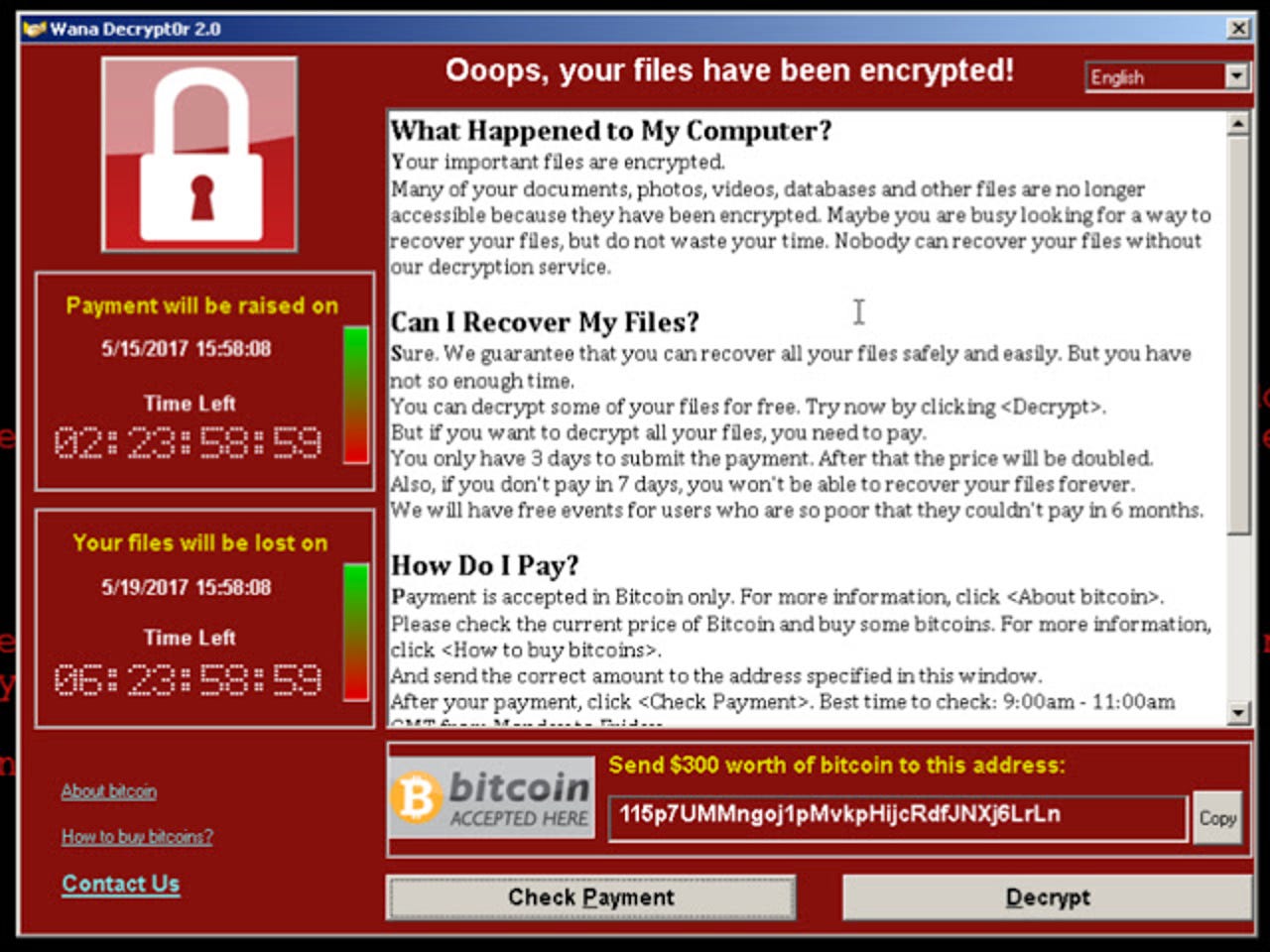
LG Electronics found itself infected by WannaCry three months after the initial global outbreak.
Global consumer electronics manufacturer LG has confirmed it had to shut down some parts of its network after systems fell victim to WannaCry ransomware.
Security
Ransomware was found on an LG self-service kiosk in South Korea, with analysis of the code identifying it as WannaCry, the file-encrypting malware that used a leaked NSA exploit to spread around the world in May this year.
WannaCry infected over 300,000 Windows systems and crippled networks, resulting in a number of major organisations -- including the UK's National Health Service (NHS) and car manufacturer Honda -- being forced to take systems offline.
While security researcher Marcus Hutchins found a killswitch to prevent further spread of the malware, and Microsoft released an emergency patch to protect older systems against WannaCry, the ransomware has continued to infect unpatched systems.
Now WannaCry has raised its head again, and infected self-service kiosk systems at LG Electronics in South Korea.
"We analyzed the malicious code that caused delays at some service centers on Aug 14th with the help of KISA [Korea Internet & Security Agency] and confirmed that it was indeed ransomware. According to KISA, yes it was the ransomware known as WannaCry," an LG spokesperson told ZDNet.
As soon as the ransomware was spotted on the network, LG blocked access at the service centre, preventing the malware from spreading to other parts of the organisation. The company says no data has been lost and no ransom has been paid.
See also: Ransomware: An executive guide to one of the biggest menaces on the web
According to LG, all unmanned reception terminals infected with WannaCry were functioning normally again after two days, and "all security updates of the unmanned reception terminals that had been infected with malicious code have been completed".
That potentially indicates that patches hadn't been applied to the network prior to this attack, leaving LG vulnerable to WannaCry and other malware that exploits vulnerabilities in the Windows' Server Message Block (SMB) v1 networking protocol to spread laterally through networks.
LG and KISA are still trying to determine how WannaCry came to infect the network at the self-service centre.
There's no official confirmation of who carried out May's original WannaCry attack, but both private cybersecurity firms and investigating government agencies have pointed to North Korea -- South Korea's geographical neighbour -- as the culprit.
Whoever was behind the attack finally cashed out the Bitcoin wallets containing the ransom payments at the beginning of August.
While the attack was high profile, mistakes in the code meant many victims were able to unlock systems without giving into the demands of hackers.
At the time of withdrawal, the Bitcoin wallets associated with WannaCry contained just 338 payments amounting to $140,000 -- something of an insignificant haul given the ransomware infected hundreds of thousands of computers.
Unfortunately, the ease with which WannaCry was able to spread has inspired other malware creators to attempt to copy WannaCry's worm-like features.
Previous coverage
Hospitals across the UK hit by WannaCrypt ransomware cyberattack, systems knocked offline
'Major Incident' declared as at least 45 NHS hospital groups across the country are taken offline by WannaCrypt ransomware attack
WannaCrypt ransomware: Microsoft issues emergency patch for Windows XP
Microsoft takes unusual step of providing direct support to unsupported systems as targets in 74 countries -- including vast swathes of UK hospitals - have been impacted by ransomware attack across the globe.